Asking people about their websites and social media credentials at the US border is unethical and illegal. However, the Trump administration will probably ask for this information if you visit the country. You can prevent this threat by following these tips:
U.S. Homeland Security Secretary John Kelly signaled the presumption that U.S. border agents could soon be curious visitors on your sites.
The Trump administration will probably ask people entering the US from seven Middle Eastern Countries about their websites, passwords, and social media accounts. Financial information and phone contacts are also on the inquiry list.
After this alleged step, the question arises: Is this a legal measure taken? Does it have a chance to be imposed shortly? And what could you do to make yourself safe?
A legal search or not
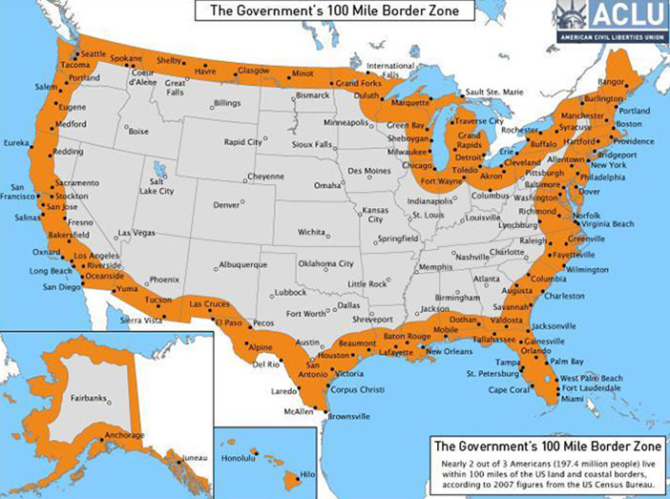
National border demanding one’s password for their social media accounts seems unjustified and illegal as the Fourth Amendment inhibits the US government from carrying out “unreasonable searches and seizures.” However, this law appears unimplemented as immigration agents have expanded dominance at the border up to 100 miles from it.
However, the issue of digital information has become convoluted. According to Orrin Kerr, talking to The Atlantic, a search of an online account could be considered to happen where the data is stored rather than at the border.
The proceeding hasn’t been initiated, making the issue more obscure and preventing it from being a subject of legal allegations. The Department of Homeland Security has already asked people about their social media handles at the border. This seems a bit controversial rather than optional.
In all these matters, the legal value of this issue is under question, specifically when the Fourth Amendment has been halted at the border.
Will it be operational?
However people ask for passwords at many borders, but it’s still a tricky question. Asking for personal information is known for many borders with strict security rules. The quest about one’s stuff has already been started in many other parts.
Recent restrictions and attempted travel bans on most Muslim countries show the present government’s endeavor to apply these practices. However, queries regarding password inquiries remain doubtful, and the legality of this issue is still unknown.
So, if you are planning to visit the U.S., you should be prepared because you will likely be asked about your stuff.
What can you do?
Many professionals are trying to figure out how to proceed, but the solution is unclear because it is unclear which strategy would work and which would trap them.
Your endeavor to visit the U.S. will decide how far you go, considering the probability of failure to reach the country. Also, the level of privacy you want plays a vital part.
Here are some tactics based on our expertise to secure your privacy and help you succeed in visiting the country. The ones at the start of the list are less likely to work and are easy to carry out. However, the ones discussed later are harder to try with the preceding list but are more likely to work.
NOTE: Use your mind for the laws and remain alert about the rules and regulations of the country you are traveling. The laws around the world differ from each other.
1. Delete your social media and email apps
This seems easy, but it only works out if you don’t have mobile data on your phone. Mobile data may enable you to re-download the app and sign in again.
On the other hand, the airport WiFi may not trap your mobile phone, and asking you to sign in through your mobile phone will prevent border agents from being inquisitive.
2. Enable two-factor authentication
Proving your identity in two ways would help if you sign out from your accounts. Also, you should not keep any other device with you so that an agent cannot force you to sign in with the 2FA code.
The query of how to get access back is simple to solve. You could ask someone you trust to tell you the 2FA code, or you can mail any device that could unlock your account to your living place.
3. Use a burner device
Burners could help protect your privacy. Your data in your primary phone is at high risk if it’s stolen or lost. While traveling, you should carry a cheap burner that does not have access to your accounts; at the border, it wouldn’t have access to them. Also, if you want your device back, you can mail it yourself or buy a new one after entering the country.
These choices could hurt but would help you secure your privacy and not give your private stuff to anyone.
4. For social accounts, use a different email account
A border agent could access your account, even if it’s two-factor authentication, by resetting your password. But if you have a second email account that is not synced to your mobile, you could prevent agents from accessing your account.
If a border agent looking into your primary email account is not annoying, this technique will help. It will also restrict them from inquiring about your social accounts. But ensure your mobile doesn’t have hints of that secondary account.
5. Change from fingerprints to passcode
In the U.S., forcing an individual to enter his mobile code is illegal, at least for now. However, you could be compelled to unlock your phone using fingerprints. If you use the fingerprint technique to unlock your phone, you must change it to the passcode.
6. Deny the demand
If you think it to be a frail idea, you are right. In the U.S., it is legal but doesn’t assure success. There is a probability that you would be stopped from entering the country. It doesn’t alter this decision whether you have particular citizenship, business in the country, or nationality of a specific country.
This is the absolute last solution and should not be used when you are just seeking your demands and rights.
Few more suggestions
You should consider certain things. The stuff you ship internationally will also likely be searched without explicit notification. Sending your packages through international delivery is not a bad option if you don’t want them with you at the border.
But what must be clear is that the above information contains no legal advice. Also, it is possible that this information could become irrelevant and illegal at a particular time, as U.S. laws are regularly changing.
Share this article
About the Author
Zehra Ali is a Tech Reporter and Journalist. She has done her Masters in Mass Communication. Topics related to cybersecurity, IoT, AI, Big Data and other privacy matters are extensively covered by her on various platforms. You can follow her on twitter.
More from Zehra AliRelated Posts

How to Avoid Gambling Restrictions in 2024
KEY TAKEAWAYS Gambling is prohibited in multiple countries as it is addictive, and many people go ba...

20 Best Penetration Testing Tools For Security Professionals
KEY TAKEAWAYS If you’re in a hurry, then have a look at the list of 20 best penetration testin...

The Role of Developer Security in Software Development
KEY TAKEAWAYS The revolution of DevOps has reduced the SLDC and resulted in the creation of many sof...

How To Detect Hidden Cameras And Listening Devices? A Complete Guide
Many people feel like someone is watching them or listening to their conversations. They may be righ...

What is Virtual Firewall and How it Helps Us in 2024?
Scientists and technicians are trying to invent the latest technology protection to create barriers ...

10 Ways to Prevent Ransomware Attacks
KEY TAKEAWAYS Ransomware attacks are growing frequently and affecting every sector of the business i...


