If you’re in a hurry, then have a look at the list of 20 best penetration testing tools that are worth considering:
- Nmap – It uses IP packets to analyze what hosts are available on the network, which operating systems they use, and the services they offer.
- Metasploit – Ethical hackers use custom codes to uncover network vulnerabilities and gain deep visibility of the network.
- Burp Suite Professional – It provides a detailed report for the pen-testers to understand the network’s vulnerabilities clearly.
- Hydra – It prevents password theft and brute force attacks and works efficiently well on Windows, macOS, Linux, and Solaris operating systems.
- Wireshark – It efficiently debugs the common TCP/IP connection problems and analyzes hundreds of protocols, including the real-time analysis and decryption of various protocols.
- OWASP-ZAP – It is a flexible and easy-to-use tool that can be used as a daemon process or as a stand-alone application on Windows, Linux, and macOS.
- John the Ripper – It is a password-cracking tool whose primary purpose is to detect weak passwords on a given system and expose them.
- Cain and Abel – It allows easy recovery of different types of passwords through brute force, dictionary, and cryptanalysis attacks.
- CANVAS by Immunity – It includes hundreds of exploits for different use case categories and exploits library extendability to penetration testers and security professionals globally.
- Kali Linux – It saves time manually setting up tools by adding an automated configuration system that optimizes the tool according to your case.
- SQLmap – Penetration testers utilize the tool to hack the databases and understand the depth of network vulnerabilities.
- Hashcat – It is an open-source, MIT-licensed, and advanced password recovery tool capable of cracking over 100 algorithms like DXX, SHA1, and UNIX.
- Netsparker – It can identify everything from cross-site scripting to SQL injections, find websites and web services, tell which are now outdated, and track their updated status.
- BeEF – It is an advanced tool that explores weaknesses beyond the client system and network perimeter.
- Aircrack – This tool works on various operating systems, including Windows, Linux, and macOS, with full support for WEP dictionary attacks.
- Ettercap – It features sniffing of live connections, content filtering on the fly, and other interesting tricks that enhance the user experience.
- Nessus – It can perform credential and non-credentialed scans, providing more visibility and depth into the vulnerabilities.
- W3af – It is an open-source tool and is free to download on various popular devices and operating systems.
- Acuntenix – The micro recording technology scan complex multi-level forms and password-protected areas of the site to identify the flaws and mitigate them
- Wapiti – It scans the web pages and injects the testing data to check for any lapse in security.
To get more detailed insight into each product, read their reviews below and decide on one for your company.
Cyber attacks are growing in severity and frequency, and businesses of all sizes are at risk. Statistics reveal global cybercrime damage will likely hit $10.5 trillion by 2025. Identifying, assessing, and remediating these risks is a significant aspect of optimizing cybersecurity, and it can be done by penetration testing.
A penetration test or ethical hacking is an effective cybersecurity technique organizations use to detect, test, and highlight the vulnerabilities within their security posture. Ethical hackers carry out cyberattacks against a system to uncover exploitable security vulnerabilities. Security professionals use penetration testing techniques with specialized tools to discover problems before attackers exploit them.
Penetration testing tools help ethical hackers evaluate the organization’s security infrastructure and defend against unknown or zero-day threats. Due to the high number of penetration testing tools available, it has become difficult for security professionals to pick up the best testing tool. This article provides a detailed insight into the 20 best penetration testing tools businesses can deploy within their network.
Why should businesses perform Penetration testing?
Penetration tests have become an integral part of security testing. It offers critical information that helps companies to stay ahead of hackers. The ultimate goal of penetration testing is to safeguard the organizational network and data against cyber attacks. It enables ethical hackers to assess the security framework and their ability to defend it. In addition, it provides high-risk weaknesses and common vulnerabilities within the network.
Besides this, penetration testing offers other benefits too. Below are the reasons why businesses must perform penetration tests:
- Penetration testing ensures organizations meet regulatory compliance requirements like EU GDPR, PCI DSS, and ISO 27001.
- It reduces the risk of data breaches and ensures that the clients’ and stakeholders’ data is secure and protected.
- Pen testing takes a proactive approach, so organizations know what remediations are needed.
- Penetration testing helps the decision-makers to evaluate the existing security strategy and develop ways to improve it.
As a whole, penetration tests enable organizations to discover security gaps before hackers can exploit them. Hence, security professionals must use reliable tools and maximize their security.
20 best Penetration testing tools
Penetration tools are typically used for the security assessment of a network or a service. If your company hasn’t started using one, it’s the right time. Below is a detailed insight into the 20 best penetration testing tools worth using, so look at them and decide which suits your needs the most.
1. Nmap
- Website URL: nmap.org
Nmap is an open-source pen-testing tool popular for discovering any holes or weaknesses within an organizational network. It comes with a debugging and comparison tool that compares the scan results and ensures the most accurate results.
Most impressively, this penetration testing tool uses IP packets to analyze what hosts are available on the network, which operating systems they use, and the services they offer. In addition, it can help audit network security issues to provide information on the servers, packet filters, firewalls, ping sweeps, and much more. Since it is open-source software, it is free to download and use and is compatible with all major operating systems like macOS, Linux, and Windows.
2. Metasploit
- Website URL: metasploit.com
Metasploit is a reliable and open-source pen tester tool that discovers the network’s and servers’ systematic vulnerabilities. Ethical hackers use custom codes to uncover network vulnerabilities and gain deep visibility of the network. This penetration testing tool is compatible with all popular operating systems like macOS, Linux, and Windows computers, having a minimum of 4GB RAM and 1GB storage.
Besides this, it comes pre-installed into the Kali Linux system and includes various anti-forensic tools for sincerely evaluating the network against existing vulnerabilities. To benefit from this tool, you can download it for free, or if you want to access all its advanced features and functionalities, you can upgrade to a paid version.
3. Burp suite professional
- Website URL: portswigger.net/burp/pro
Burp Suite Professional is a Java-based penetration testing tool that PortSwigger web security develops. It is a combined testing and vulnerability scanning tool designed for web applications. The tool efficiently determines and decodes the encryption used to transfer the data packets across the network and can even encode similar data within the network and ensure finding all the vulnerabilities within the attack surface.
Burp Suite Professional provides a detailed report for the pen-testers to understand the network’s vulnerabilities clearly. It comes in three different versions, and all versions run successfully on macOS, Linux, and Windows OS. Since it offers a paid version, which is quite expensive, users don’t prefer to use it.
4. Hydra
- Website URL: github.com/vanhauser-thc/thc-hydra
Hydra is a reliable password penetration testing tool that allows ethical hackers to crack network service passwords. This handy tool prevents password theft and brute force attacks and works efficiently on Windows, macOS, Linux, and Solaris operating systems. It is an easy-to-use tool that supports protocols like HTTP, HTTPS, FTP, SMB database, and more.
In addition, it supports more than one connection in parallel, reducing the time to crack a password, unlike in sequential brute-forcing and ensuring efficiency. However, the tool comes preinstalled with Parros and Kalxi Linux OS. If you use any of these tools, you can start using Hydra immediately.
5. Wireshark
- Website URL: wireshark.org
Wireshark is an open-source penetration testing tool that provides a microscopic network view. It efficiently debugs the standard TCP/IP connection problems and analyzes hundreds of protocols, including the real-time analysis and decryption of various protocols. In addition, this pen tester tool allows ethical hackers to identify the flaws within the security systems at the user authentication level.
After performing the tests, it provides a comprehensive report in a format easily understood by any operator and ensures a smooth user experience. The software is compatible with various operating systems, including Windows, macOS, Linux, and Solaris, and is available to download for free.
6. OWASP-ZAP
- Website URL: zaproxy.org
OWASP-ZAP is a free and open-source penetration testing tool that allows users to find vulnerabilities within web applications. The best thing about this tool is that it provides automated scanners and tools that enable you to find security vulnerabilities manually. It intercepts and inspects the messages sent between the browser and web applications and sends alerts about any suspicious activity.
Besides this, it is a flexible and easy-to-use tool compatible with Windows, Linux, and macOS. You can also run OWASP-ZAP in a Docker container, and its functionality is scalable with various diverse extensions published on GitHub that ensure a fantastic user experience.
7. John the Ripper
- Website URL: openwall.com/john/
John the Ripper is another password-cracking tool whose primary purpose is to detect weak passwords on a given system and expose them. One impressive feature of John the Ripper is that it uses dictionary attacks, meaning it uses random words from the dictionary to detect a password.
Also, it can access encrypted passwords and ensures that it doesn’t miss out on any password combination within a given parameter. This tool is free to download and is compatible with Windows, macOS, and Unix. However, this tool won’t allow the users to test network vulnerabilities at a deeper level.
8. Cain and Abel
- Website URL: cain-abel.en.softonic.com
Cain and Abel are one of the best free penetration testing tools that use various methods for password recovery and packet analysis on Microsoft Windows. It allows easy recovery of different types of passwords through brute force, dictionary, and cryptanalysis attacks. In addition, it also monitors and sniffs network data packets, which they capture and analyze to get important information about the network.
The tool offers a range of impressive features like the APR, which allows sniffing on switched LANs and Man-in-the-Middle attacks and boosts efficiency. Developers created this tool to run on Microsoft Windows from Vista to the latest Windows operating system, and hence won’t work on any other platform, which might disappoint the users.
9. CANVAS by Immunity

- Website URL: immunityinc.com/products/canvas/
Canvas by Immunity is a leading security assessment tool that allows penetration testing, hostile attack stimulations, and exploit research and development. It includes hundreds of exploits that can be used by different use case categories and exploits library extendability to penetration testers and security professionals globally.
This tool is easier to use than most free and open-source tools and efficiently operates on Linux and Windows operating systems but on Android phones with certain restrictions. It is a premium penetration testing tool with yearly licensing fees, which some might find costly.
10. Kali Linux
- Website URL: kali.org
Kali Linux is an open-source penetration testing tool managed and maintained by Offensive Security. It is a free penetration testing tool for experts and visually impaired individuals using the Linux operating system. Being an open-source project, Kali Linux provides meta-packages, tool listings, and version tracking to generate software versions of their testing processes.
It offers other advanced multi-platform features that support security professionals while conducting a test on desktop, mobile, docker subsystems, and virtual machines. Besides this, Kali Linux also saves time manually setting up tools by adding an automated configuration system that optimizes the tool according to your case and ensures a smooth and hassle-free user experience.
11. SQLmap
- Website URL: sqlmap.org
SQLmap is another open-source penetration testing tool used to uncover and exploit SQL injection flaws, i.e. when user input can alter the execution of the SQL query. It is an impressive automated tool with detailed features like remote commands, DB fingerprinting, and detection engines, making the search process more manageable. Ethical hackers or penetration testers utilize the tool to hack the databases and understand the depth of network vulnerabilities.
Besides this, SQLmap also works as a password-cracking tool that automatically recognizes the hash formats and uses a dictionary-based attack technique to detect vulnerable and exploited passwords. This tool is compatible with Microsoft Access, SQLite, MySQL, and IBM DB2 servers and Linux, macOS, and Windows operating systems.
12. Hashcat
- Website URL: hashcat.net/hashcat
Hashcat is a trusted and fastest password recovery tool that supports hashing algorithms and efficiently works with various attack modes. It is an open-source, MIT-licensed, and advanced password recovery tool capable of cracking over 100 algorithms like DXX, SHA1, and UNIX. Another impressive thing about this software is its multi-device compatibility feature.
You can download this tool on macOS, Linux, and Windows to prevent password cracking and brute-force attacks, and because of its open-source nature, you can use it for free. Besides this, developers are also continuously updating this tool. Thus, the penetration testers must check their GitHub repository to use the latest version.
13. Netsparker
- Website URL: invicti.com/web-vulnerability-scanner
Netsparker Security Scanner, previously known as Invictic, is one of the best automatic web applications for penetration testing. It can identify everything from cross-site scripting to SQL injections, find websites and web services, tell which are outdated, and track their updated status.
One impressive characteristic of this pen-testing tool is that as it allows ethical hackers to scan up to 1000 web apps simultaneously, the users can customize the security scans with attack options and URL rewrite rules to ensure a more efficient process. In addition, it saves the users from conducting manual scans and instead performs continuous automated scans, which saves time and increases efficiency.
14. BeEF
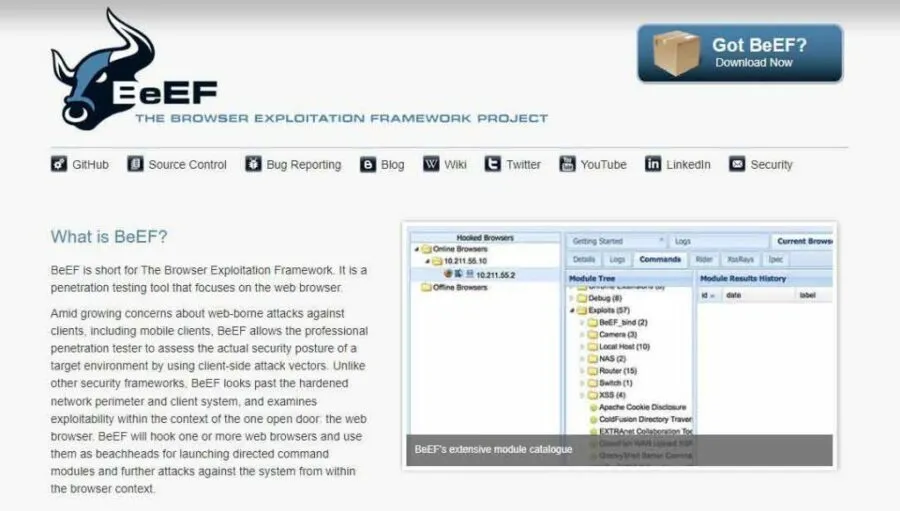
- Website URL: beefproject.com
BeEF (Browser Exploitation Framework) is a reliable penetration testing tool that uses GitHub to locate the issue and is suitable for checking a web browser. It is an advanced tool that explores weaknesses beyond the client system and network perimeter. In addition, this tool has an impressive feature that allows the pentester to use the client-side vectors to determine the security state of the web browser.
Besides this, it hooks one or more web browsers and uses them as beachheads for launching directed command modules and further attacks against the system within the browser context. As BeEF relies on the GitHub repositories to recognize the issues, it’s free to use and download. But it does accept donations to keep running its services.
15. Aircrack NG
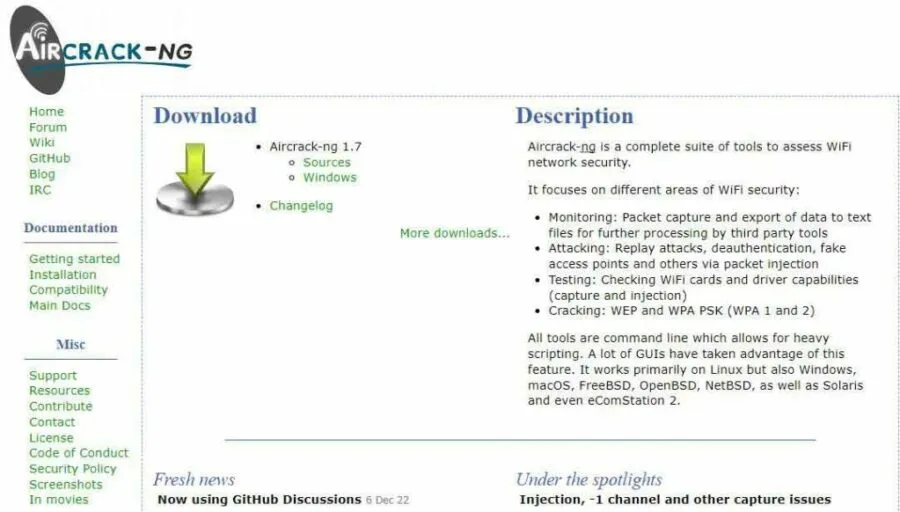
- Website URL: aircrack-ng.org
Aircrack NG is an advanced penetration testing tool for identifying flaws within wireless connections. It is a complete suite of tools to test the Wi-Fi network security. The tool efficiently monitors the given Wi-Fi network, captures the data packets, and then exports them to text files for further network analysis.
It also uses a password dictionary and statistical techniques to break into the WEP and can set up fake access points and carry out replay attacks on the network. Initially, the tool worked on Linux OS, but now it has extended its support for Windows and macOS.
16. Ettercap
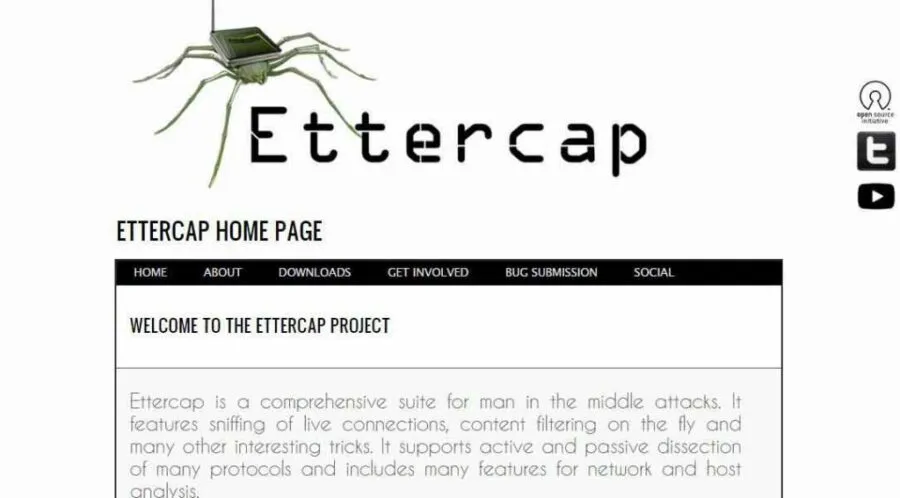
- Website URL: ettercap-project.org
Ettercap is a free and open-source security suite designed to prevent man-in-the-middle attacks. It is an excellent tool for building the packets per the user’s need and performing specific tasks. It is an excellent tool for building the packets per the user’s need and performing specific tasks. The software can send invalid frames and complete techniques that are more difficult through other options.
What’s impressive is that it features sniffing of live connections, content filtering on the fly, and other exciting tricks that enhance the user experience. Also, it supports active and passive dissection of many protocols and includes several features for host and network analysis. You can use this tool for free on Windows and other supported platforms.
17. Nessus
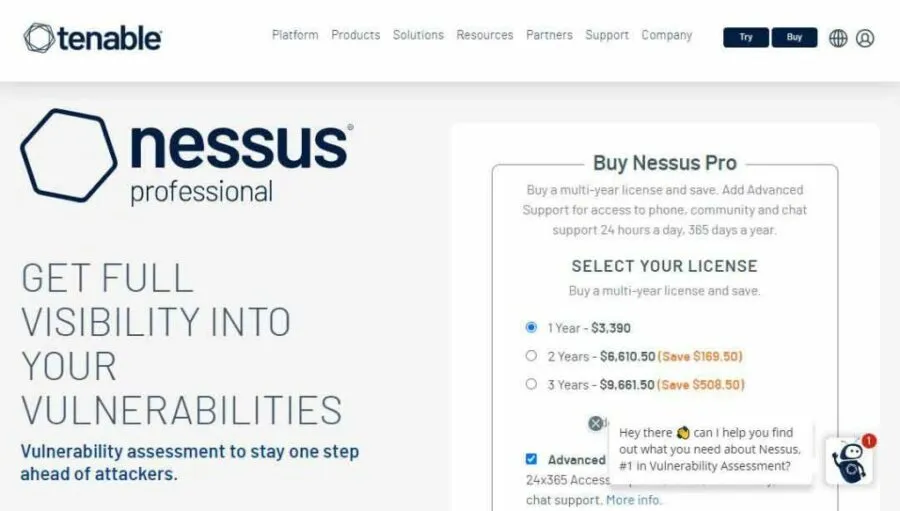
- Website URL: tenable.com/products/nessus/nessus-professional
Nessus is a penetration testing tool that enables users to perform a complete vulnerability assessment of web applications and operating systems. It is a fantastic tool that efficiently detects and fixes vulnerabilities, including missing patches and software flaws. In addition, it can perform both credential and non-credentialed scans, providing more visibility and depth into the vulnerabilities.
This way, Nessus ensures complete test coverage of your operating system and identifies every security flaw within your app. Another good thing about this tool is that it easily integrates with tools like Microsoft Azure, ServiceNow, and Google Cloud. Plus, it works on various operating systems like Windows, macOS, and Linux. However, it is not a free penetration testing tool but comes with a seven-day trial version, so you can use it and decide whether it’s worth using.
18. W3af
- Website URL: w3af.org
W3af is an open-source, python-driven testing suite that helps audit your frameworks and web applications for vulnerabilities. One impressive feature of W3af is that it enables the pen testers to easily exploit the SQL injections to understand the scope of security risks.
In addition, it offers a manual request generation feature that acts like a man-in-the-middle attack proxy and helps in manual web app testing. This tool is also handy for expert users who want to create custom HTTP requests and responses. Since it is an open-source tool, it is free to download on various popular devices and operating systems and attracts more users.
19. Acuntenix
- Website URL: acunetix.com/plp/penetration-testing/
Acuntenix is an automated penetration testing tool for your web application. It checks and scans for the ever-growing threat of web application vulnerabilities and ensures the security of all assets. The advanced micro recording technology is Acuntenix’s most impressive feature. It lets you scan complex multi-level forms and password-protected site areas to identify and mitigate flaws.
Besides this, it can detect over 7000 vulnerabilities, including SQL injections, weak passwords, XXS, misconfigurations, and exposed databases. The tool has a paid version, but you can contact the support team to have a demo of the product.
20. Wapiti
- Website URL: wapiti-scanner.github.io
Wapiti is a rare penetration testing tool that allows you to audit the security of your web applications. It performs black-box scanning of the web application by crawling the web pages of the deployed web apps. It scans the web pages and injects the testing data to check for any lapse in security.
In addition, Wapiti detects vulnerabilities in file disclosure, database injection, Command Execution detection, and XXE injection. It is a free and open-source tool, so users can download it and start using it immediately on Linux and FreeBSD.
Key features you must look into the best Penetration tools
Several pen-testing tools are available, but not all are worth using. Hence, it’s essential to choose the tool wisely. Here are some key features you must look into in the penetration testing tool before using them:
- The tool must offer a comprehensive suite of features that enables you to test and analyze every aspect of the operating system.
- Choose a penetration testing tool that performs multiple scans to discover vulnerabilities and provides a detailed report with minimum false positives.
- Ensure the tool provides a centralized customizable dashboard for experienced and non-technical users.
- The best penetration testing tool is the one that works on different devices. Select a tool compatible with various devices like Windows, Linux, and macOS.
- Passwords are the weakest link in any organization. Ensure you use penetration testing software with password cracking ability to assess the password’s strength.
You must choose a pen-testing tool with all the above features to get accurate results.
What are the stages involved in Penetration testing
Penetration testing involves hacking in to check for vulnerable spots that the malicious attackers can exploit. For this purpose, ethical hackers use manual and automated technologies to compromise servers, web applications, network devices, wireless networks, mobile devices, and other potential exposure points. The entire process comprises five different stages, and below is a brief overview of them:
- Reconnaissance: In this stage, the testers prepare a list of vulnerable areas that can result in a potential breach and rank them in order of criticality.
- Scanning: Pen testers use various tools to perform vulnerability scans to look for loopholes for unauthorized access.
- Vulnerability Analysis: The tester uses all the data gathered in the first two steps to detect potential vulnerabilities and determine whether they can be exploited.
- Exploitation: The tester attempts to access the target’s system and exploit the identified vulnerabilities to simulate real-world attacks.
- Analysis: In the last stage, the pen-tester prepares a report regarding the findings that help fix the vulnerabilities and improve the security infrastructure.
That’s it. These are the steps of a successful penetration test; ensure to use a reliable tool like the ones mentioned above.
What are the primary methodologies of Penetration testing
As there are different types of penetration tests similarly, there are various methods to carry out these tests, and below is an overview of these methods:
- External Testing: It targets the company’s assets visible on the web to gain access and extract valuable data.
- Internal Testing: Ethical hackers access an application behind its firewall or through compromised or stolen credentials.
- Double Blind Testing: Only one or two persons within an enterprise know that a test is being performed in this type of testing.
- Blind Testing: This test simulates the actions and procedures of an actual attacker by providing limited information to the team performing the test.
Companies can decide which method to use to test their assets’ security.
What are the different types of Penetration testing
Security professionals adopt different penetration testing types depending on their objective, scope, and requirements for assessing their organizational security. Below is an insight into the most common types of penetration testing software, so have a look:
- Network Penetration Test: It is of two types, i.e., internal and external penetration tests. The internal penetration test assesses the organization’s internal network configuration, while the external penetration tests include testing public IP addresses, servers, and network protocols.
- Web Application Tests: The pentester detects vulnerabilities in web applications, web services, and websites by assessing the security of the code, design, and flaws in the app’s security protocol.
- Wireless Network Tests: It detects security glitches with wireless access points like wireless devices and Wi-Fi networks by accessing vulnerabilities like weak encryption, authentication attacks, and Bluetooth to combat data breaches.
- IoT Penetration Tests: This test allows ethical hackers to look for security flaws in the connected objects such as APIs, Web Interfaces, mobile apps, hardware, and other embedded software.
- Cloud Penetration Tests: This test provides valuable insights into the strengths and weaknesses of cloud-based solutions.
- Mobile Device Penetration Tests: This helps assess the security of mobile devices and applications and uncover vulnerabilities within the application code.
Besides this, social engineering, OT, and database penetration testing are also some types of penetration testing.
Conclusion
Penetration testing or ethical hacking exposed computer systems, networks, applications, and website vulnerabilities. As cyber-attacks increase in number and sophistication, organizations must perform regular penetration testing to boost the security posture of the entire organization. The tools mentioned above are some of the best penetration testing software available. Organizations must invest in such tools to reduce risks and boost security.
FAQs
Share this article
About the Author
Farwa is an experienced InfoSec writer and cybersecurity journalist skilled in writing articles related to cybersecurity, AI, DevOps, Big Data, Cloud security, VPNs, IAM, and Cloud Computing. Also a contributor on Tripwire.com, Infosecurity Magazine, Security Boulevard, DevOps.com, and CPO Magazine.
More from Farwa SajjadRelated Posts

How to Avoid Restrictions When Gambling Online
The figures of people who like online gambling are continuously increasing. Over 155.3 million peopl...

The Role of Developer Security as a Standard in the Software Development Process
Also known as developer-first security, developer security refers to building software while shiftin...

How To Detect Hidden Cameras And Listening Devices? A Complete Guide
Many people feel like someone is watching them or listening to their conversations. They may be righ...

What Is Virtual Firewall And How It Help Us?
Our cybersecurity team is continuously working for the welfare of people by finding out and preventi...

7 Tips to Conquer Ransomware Attacks
Ransomware attacks are growing frequently and affecting every sector of the business industry. These...

What Is Ransomware Attacks and How To Remove It – A Complete Guide
According to a report by Symantec, ransomware attacks affected around 3.5 million people in 2018. Th...





