In 2012 Saudi Aramco, the Saudi national oil company got hacked by a disk-wiping malware Shamoon 2 that wiped data from 35,000 computers. A new disk wiper StoneDrill has been unveiled, which is identical to Shamoon 2 malware, striking a European petroleum company.
Kaspersky researchers discovered StoneDrill while researching the reoccurring of Shamoon 2 malware attacks, among which two occurred in November and one in January. These researchers also uncovered that the new disk-wiping malware StoneDrill was built with similar mindset and programming style as that of Shamoon 2, but they don’t have the same code base.
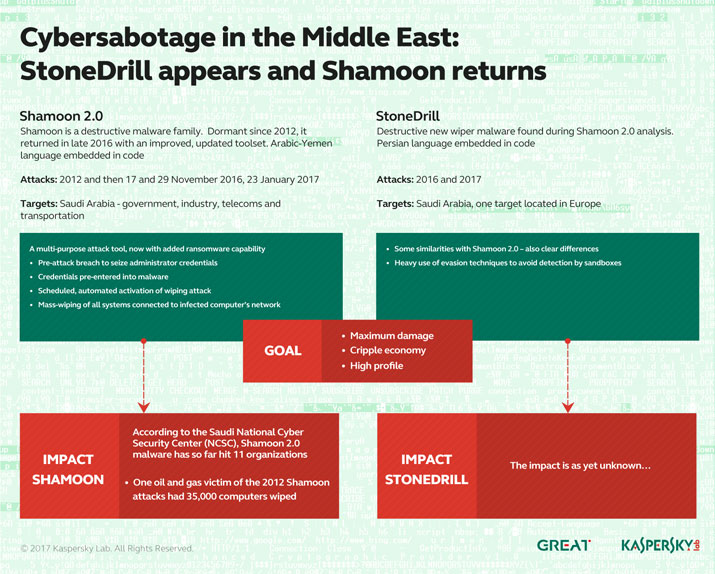
StoneDrill seems more identical to Charming Kitten malware, said Kaspersky. This both malware have similarity in code, C&C (command and control) servers, classified commands and functionality and Winmain signatures.
The four C&C servers discovered by researchers in a StoneDrill malware are used for spying on countless prey. Similarly, for spying and stealing purpose, a StoneDrill sample serving as a backdoor has also been uncovered.
Once an organization gets struck by disk-wiping malware, it tends to debilitate the organization by completely eradicating data from the hard drives and external storage on a targeted system. Although it is not yet known that how StoneDrill gets dispatched to its prey, but once it infects a system it notoriously wipes off data and destroys its prey.
StoneDrill has been designed so that it targets all systems of an organization. This malware confines itself on a list of hard coded, stolen usernames and passwords of administrators of the targeted system. Once StoneDrill gets a strong hold on the system, it generates a custom wiper malware module and leaves the system nonfunctional. StoneDrill wiper malware is comprised of new escaping techniques, backdoor ability and ransomware component for financial profit.
According to Kaspersky, ‘The discovery of the StoneDrill wiper in Europe is a significant sign that the group is expanding its destructive attacks outside the Middle East’.
Share this article
About the Author
Rutaba Rais is Editor at Be Encrypted with focus on Technology and Internet Security. Apart from her Healthcare background, she has interests in Lifestyle, Journalism, and expressing her opinion by her writing. You can follow her on Twitter.
More from Rutaba RaisRelated Posts

Passengers’ Data Stored on User Devices, not on DigiYatra Storage, says India Govt
KEY TAKEAWAYS Unblocking streaming content from Amazon Prime is easy only if you know the reliable V...

NCSC Chief: Clear Rules Needed to Prevent Cyberspace Conflict and Struggle
A safe and secure digital world necessitates a clear definition and enforcement of international cyb...

‘Revive’ has been upgraded to a banking Trojan on Android
This month, Cleafy’s security researchers discovered a new Android Banking Trojan in the wild....

Asian Industrial Control Systems Targeted by Hackers Using the Shadowpad Backdoor
Unpatched Microsoft Exchange servers in various Asian countries were the target of an attack campaig...
Data Breaches Could Occur Due to Kubernetes Misconfigurations That Were Leaked.
Over 900,000 Kubernetes (K8s) have been discovered to be vulnerable to malicious scans and/or data-e...

Attacks by Cybercriminals Will Become the Main Threat in 2024. Privacy Issues Tendencies
Internet Privacy is the main Concern today Advertisers track your online activities and interf...


