A recent discovery in mobile malware family been calling as “DressCode” has infected over 400 apps that are in distribution via Google Play, expert researchers at Trend Micro warns.
The malware “DressCode” has infected around 40 apps in Google play and 400 new apps distributed through third-party app stores, but the actual number of infected apps might be more. Security researchers at Trend Micro say that they detected the malware “DressCode” as ANDROIDOS_SOCKSBOT.A and discovered at least 3,000 Trojanized apps.
The malware “DressCode” is in the spread stealthily since April and distributes through various apps including skins, games, themes, and more. Since the malware is a small part of the infected app, it makes its detection rather difficult. However, Google took the necessary steps to remove those apps from its server when Trend Micro notified Google in September.
Once the victim installs the infected application, the malware connects to its C&C (Command and Control) server, which is now a domain in newer versions of malware (as it was a hardcoded IP address before in previous ones). The device is then converted into a proxy that can transfer traffic between the internal server (the mobile is connected to) and the attacker.
Trend Micro explains the threat mechanism as, “A background service creates a Transmission Control Protocol (TCP) socket that connects the compromised device with the C&C server and sends a “HELLO” string to finish registering. Once the C&C server replies, a “CREATE, <Attacker IP>, <Port>” command prompts the device to establish a TCP connection between it and the attacker. It allows the device to receive commands from the attacker via the SOCKS protocol.”
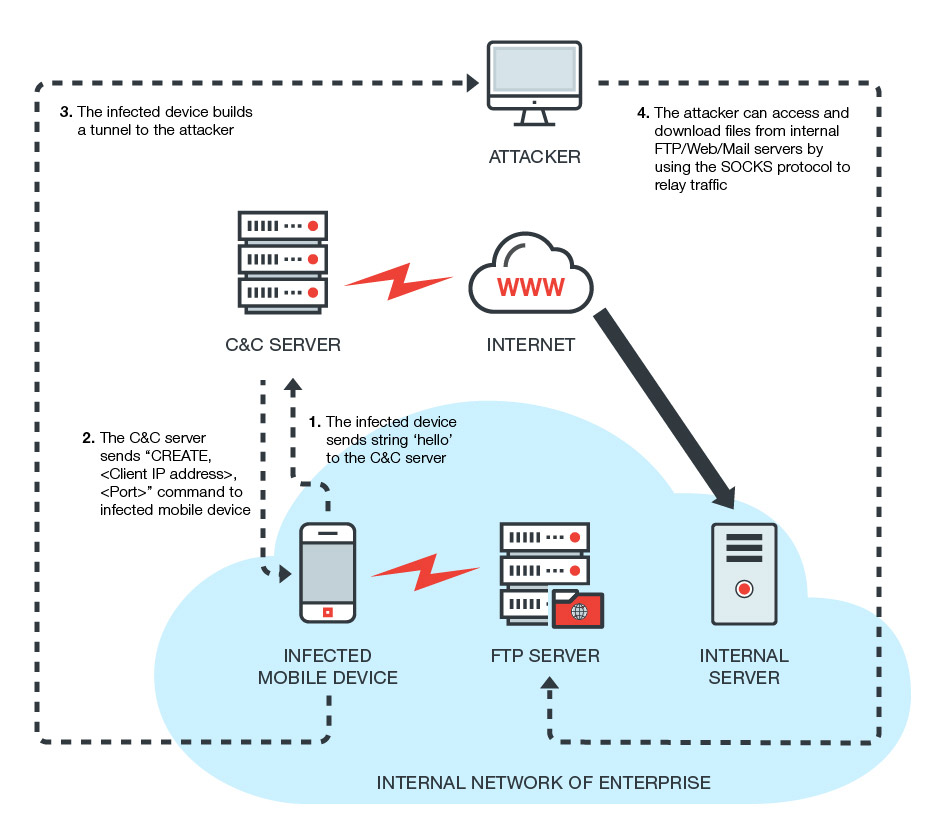
According to Trend Micro, the malware “DressCode” infected device starts a TCP connection between C&C server and the attacker, as the device is behind the router. The moment the SOCKS proxy is established, the device is then able to run commands by the attacker to other servers in the connected LAN (the device is connected to), which allows the attacker to log-in to the internal servers located behind the router.
By leveraging mobile devices as a proxy, the device owner, and the connected network is exposed to the attacker. It could pose a significant threat to the businesses internal servers, researchers say.
Describing this scenario, the researchers said, “This malware (DressCode) allows threat actors to infiltrate a user’s network environment. If an infected device connects to an enterprise network, the attacker can either bypass the NAT device to attack the internal server or download sensitive data using the infected device as a springboard. With the growth of Bring-Your-Own-Device (BYOD) programs, more enterprises are exposing themselves to risk via carefree employee mobile usage.”
Because of the forced installed SOCKS proxy, the device is misused as a bot, if the attackers use them in BotNet attack i.e. DDoS attack or spam emails. The attackers could monetize the process through such attacks.
Such malware attacks can exploit weak routers connected to the device and expose IP addresses; the malware, in turn, can be used to exploit other vulnerabilities like connected cameras, researchers say.
Image credits: Trend Micro
Share this article
About the Author
Rebecca James is an IT consultant with forward thinking approach toward developing IT infrastructures of SMEs. She writes to engage with individuals and raise awareness of digital security, privacy, and better IT infrastructure.
More from Rebecca JamesRelated Posts

Passengers’ Data Stored on User Devices, not on DigiYatra Storage, says India Govt
KEY TAKEAWAYS Unblocking streaming content from Amazon Prime is easy only if you know the reliable V...

NCSC Chief: Clear Rules Needed to Prevent Cyberspace Conflict and Struggle
A safe and secure digital world necessitates a clear definition and enforcement of international cyb...

‘Revive’ has been upgraded to a banking Trojan on Android
This month, Cleafy’s security researchers discovered a new Android Banking Trojan in the wild....

Asian Industrial Control Systems Targeted by Hackers Using the Shadowpad Backdoor
Unpatched Microsoft Exchange servers in various Asian countries were the target of an attack campaig...
Data Breaches Could Occur Due to Kubernetes Misconfigurations That Were Leaked.
Over 900,000 Kubernetes (K8s) have been discovered to be vulnerable to malicious scans and/or data-e...

Attacks by Cybercriminals Will Become the Main Threat in 2024. Privacy Issues Tendencies
Internet Privacy is the main Concern today Advertisers track your online activities and interf...


