A malware attack on National Health Service (NHS) network caused hundreds of scheduled appointments, operations, and diagnostic procedures to be canceled.
The situation has become infuriating and dangerous as healthcare industry continue to be a prime target for malware and hackers.
On Sunday, England-based Hospital “National Health Service” experienced an attack from unknown malware which resulted in the cancellation of scheduled operations, diagnostic procedures, and appointments.
To stop the malware, the IT staff of the hospital had to shut down their entire shared IT network to isolate and remove the malware from the systems.
Some patients with critical conditions were diverted to the neighboring hospitals for immediate treament.
Other hospitals that recently experienced malware attacks includes Scunthorpe General, Diana Princess of Wales in Grimsby, and Goole and District Hospital.
The NHS Foundation Trust (NLAG) and Northern Lincolnshire made an announcement on October 30th that the malware infected the hospital systems in Grimsby and Scunthorpe. The foundation classified the problem as a ‘major incident’ on its Twitter account and website.
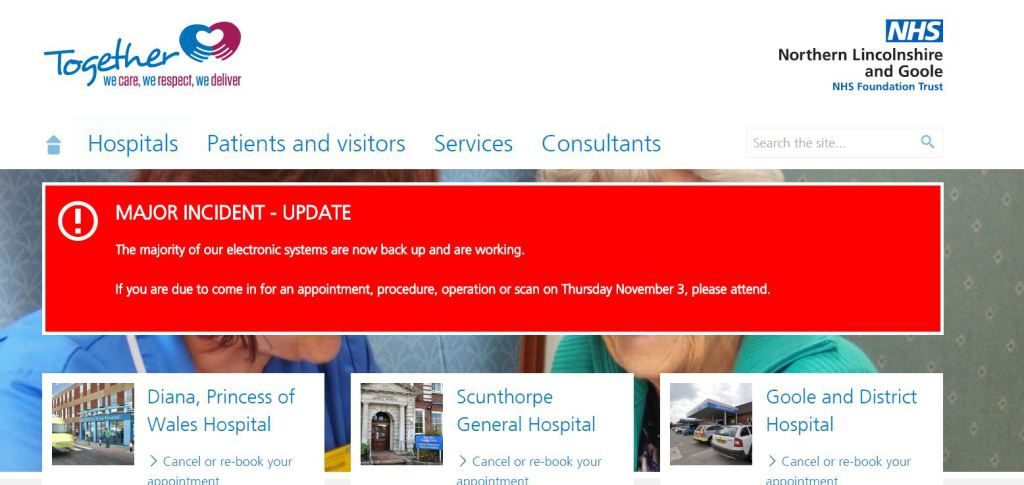
As mentioned on the site, the notification reads “We have taken the decision, following expert advice, to shut down the majority of our systems so we can isolate and destroy it.”
The systems are now back online and running their routine work. However, the NHS Trust did not provide any details related to possible data breach and damages.
2015 experienced a tremendous increase in ransomware attacks on hospitals, causing damage to their operations. The FBI had to issue urgent “Flash” messages to notify businesses and organizations about the “SamSam Ransomware” threat. Also known as ‘MSIL’ and ‘Samas’ the ransomware encrypts the sensitive data and ask for ransom (which becomes unlikely to retrieve data even after payments).
In 2015, MedStar Hospital in Washington D.C. experienced this malware and were asked 45 BTC (approx. $18,500). The hospital had to shut down its operations and restore the backup data. The practice that every organization should follow to avoid such attacks. You can find more information about this ransomware on Microsoft’s page.
In the case of NHS Trust, the origin, and the name of malware are unknown, it is likely that it is the previous malware that attacked in 2015 have attacked now after someone speculated the malicious code.
The cyber security is now becoming the critical factor while strategizing the infrastructure of healthcare industry.
Share this article
About the Author
Peter Buttler an Infosec Journalist and Tech Reporter, Member of IDG Network. In 2011, he completed Masters in Cybersecurity and technology. He worked for leading security and tech giants as Staff Writer. Currently, he contributes to a number of online publications, including The Next Web, CSO Online, Infosecurity Mag, SC Magazine, Tripwire, GlobalSign CSO Australia, etc. His favorite areas Online Privacy, AI, IoT, VR, Blockchain, Big Data, ML, Fintech, etc. You can follow him on twitter.
More from Peter ButtlerRelated Posts

Passengers’ Data Stored on User Devices, not on DigiYatra Storage, says India Govt
KEY TAKEAWAYS Unblocking streaming content from Amazon Prime is easy only if you know the reliable V...

NCSC Chief: Clear Rules Needed to Prevent Cyberspace Conflict and Struggle
A safe and secure digital world necessitates a clear definition and enforcement of international cyb...

‘Revive’ has been upgraded to a banking Trojan on Android
This month, Cleafy’s security researchers discovered a new Android Banking Trojan in the wild....

Asian Industrial Control Systems Targeted by Hackers Using the Shadowpad Backdoor
Unpatched Microsoft Exchange servers in various Asian countries were the target of an attack campaig...
Data Breaches Could Occur Due to Kubernetes Misconfigurations That Were Leaked.
Over 900,000 Kubernetes (K8s) have been discovered to be vulnerable to malicious scans and/or data-e...

Attacks by Cybercriminals Will Become the Main Threat in 2024. Privacy Issues Tendencies
Internet Privacy is the main Concern today Advertisers track your online activities and interf...


