Hackers are now leveraging Facebook Messenger’s trust to spread locky-ransomware via SVG images in a Facebook spam campaign.
The ongoing Facebook spam campaign is the culprit behind the spreading of malware downloader by taking advantage of ‘seem to be’ harmless SVG image file to infect the masses.
The Facebook spam campaign was first spotted by the researcher Peter Kruse and malware expert Bart Blaze.
On his blog post, Bart Blaze wrote, “Earlier today, a friend of mine notified me of something strange going on with his Facebook account; a message containing only an image (a .svg file in reality) had been sent automatically, effectively bypassing Facebook’s file extension filter:”
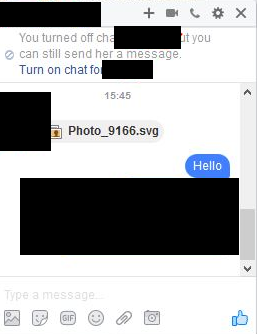
The SVG image file can embed any content (such as JavaScript) to bypass security filters.
What is SVG?, as mentioned at Wikipedia:
“Scalable Vector Graphics (SVG) is an XML-based vector image format for two-dimensional graphics with support for interactivity and animation. The SVG specification is an open standard developed by the World Wide Web Consortium (W3C) since 1999.
SVG images and their behaviors are defined in XML text files. This means that they can be searched, indexed, scripted, and compressed.”
When a victim clicks and opens the malicious SVG file, it redirects him to a malicious website disguised as YouTube and asks to install a chrome extension to play the video.
“A website purporting to be Youtube, with a video from Facebook – of course, you’ll need to install an additional extension to view it,” wrote Bart Blaze.
The malicious chrome extension appears invisible with no icon and has the following permission: “Read and change all your data on the websites you visit.”
Once a victim installs the extension, the attack spreads further and installs a downloader Nemucod which executes the locky-ransomware.
The security researcher, Peter Kruse noticed the similar behavior and got locky-ransomware as a consequence
Confirmed! #Locky spreading on #Facebook through #Nemucod camouflaged as .svg file. Bypasses FB file whitelist. https://t.co/WYRE6BlXIF pic.twitter.com/jgKs29zcaG
— Peter Kruse | Cybercrime Research (@peterkruse) November 20, 2016
To remove the malicious extension immediately from your browser, follow these steps:
- Open the browser, and click on menu (three-lined option).
- Navigate to More Tools > Extensions.
- Click the extension you want to remove and click on the ‘trash bin‘ to remove it from chrome.
- A notification will appear to confirm the removal of the extension. Click on Remove.
After removing the malicious extension, run a system scan and change your Facebook’s password.
Moreover, notify your friends about this campaign, and ask them if they received a spam message from your end. If you receive the same message from one of your compromised friend’s profile, temporarily block their messages.
Share this article
About the Author
Peter Buttler an Infosec Journalist and Tech Reporter, Member of IDG Network. In 2011, he completed Masters in Cybersecurity and technology. He worked for leading security and tech giants as Staff Writer. Currently, he contributes to a number of online publications, including The Next Web, CSO Online, Infosecurity Mag, SC Magazine, Tripwire, GlobalSign CSO Australia, etc. His favorite areas Online Privacy, AI, IoT, VR, Blockchain, Big Data, ML, Fintech, etc. You can follow him on twitter.
More from Peter ButtlerRelated Posts

Passengers’ Data Stored on User Devices, not on DigiYatra Storage, says India Govt
KEY TAKEAWAYS Unblocking streaming content from Amazon Prime is easy only if you know the reliable V...

NCSC Chief: Clear Rules Needed to Prevent Cyberspace Conflict and Struggle
A safe and secure digital world necessitates a clear definition and enforcement of international cyb...

‘Revive’ has been upgraded to a banking Trojan on Android
This month, Cleafy’s security researchers discovered a new Android Banking Trojan in the wild....

Asian Industrial Control Systems Targeted by Hackers Using the Shadowpad Backdoor
Unpatched Microsoft Exchange servers in various Asian countries were the target of an attack campaig...
Data Breaches Could Occur Due to Kubernetes Misconfigurations That Were Leaked.
Over 900,000 Kubernetes (K8s) have been discovered to be vulnerable to malicious scans and/or data-e...

Attacks by Cybercriminals Will Become the Main Threat in 2024. Privacy Issues Tendencies
Internet Privacy is the main Concern today Advertisers track your online activities and interf...


