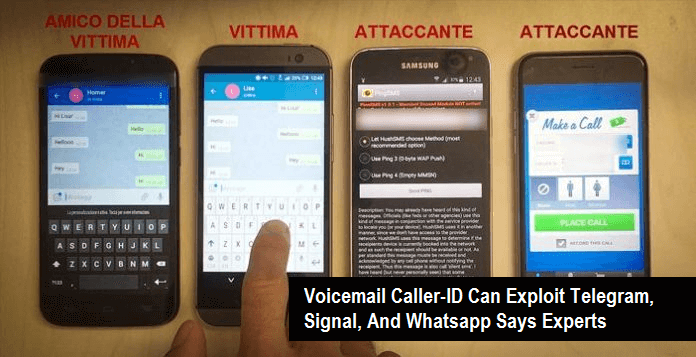
Italian cyber security experts have found a voicemail caller-ID vulnerability that can potentially be exploited to hack into the messaging apps such as Telegram, Signal, and Whatsapp.
According to InTheCyber experts, an old voicemail caller-ID spoof can be leveraged into stealing activation codes sent from messaging apps services and compromise the victim’s account. The experts said that the there are two major network operators in Italy, that allows such kind of attack, and an attacker only requires victim’s phone number to carry a successful attack.
Based in Lugano and Milan, the security firm InTheCyber explained in a blog post that the bug can be exploited in three different scenarios and all those scenarios require victim not to respond, engaged in a conversation, and not reachable.
The concept behind this attack is that messaging apps like Signal, Telegram, and Whatsapp send an activation code via SMS when requested. If the SMS fails or doesn’t comply promptly, it then sends the activation code via an automated call. Thus, if the user does not respond, the call leaves a voicemail for the user to respond it later. The attacker simply needs to spoof the caller-ID in order to retrieve the activation code.
Since calls are sent to voicemail when a user is occupied, does not respond, or is unreachable, the attacker can execute the attack to leverage all three possible scenarios. An attacker can send silent-SMS to determine whether the phone is unreachable and detach from the network. He can request the activation code late at night and could set up a scam to keep the phone in a busy state during the attack.
Once the code is sent to the voicemail, the attacker can spoof the caller-ID to impersonate as the victim and retrieve both the voicemail and activation code. The experts have demonstrated the attack in a video for the explanation and publicized the details on Monday, at ‘Cyber Warfare’ 7th National Conference in Milan.
The researcher estimates that roughly 32 million users are at risk who are using H3G and Wind. The immediate solution is to turn off the voicemail, while both the wireless carriers and messaging app service providers look into the matter and resolve it.
Share this article
About the Author
Peter Buttler an Infosec Journalist and Tech Reporter, Member of IDG Network. In 2011, he completed Masters in Cybersecurity and technology. He worked for leading security and tech giants as Staff Writer. Currently, he contributes to a number of online publications, including The Next Web, CSO Online, Infosecurity Mag, SC Magazine, Tripwire, GlobalSign CSO Australia, etc. His favorite areas Online Privacy, AI, IoT, VR, Blockchain, Big Data, ML, Fintech, etc. You can follow him on twitter.
More from Peter ButtlerRelated Posts

Passengers’ Data Stored on User Devices, not on DigiYatra Storage, says India Govt
KEY TAKEAWAYS Unblocking streaming content from Amazon Prime is easy only if you know the reliable V...

NCSC Chief: Clear Rules Needed to Prevent Cyberspace Conflict and Struggle
A safe and secure digital world necessitates a clear definition and enforcement of international cyb...

‘Revive’ has been upgraded to a banking Trojan on Android
This month, Cleafy’s security researchers discovered a new Android Banking Trojan in the wild....

Asian Industrial Control Systems Targeted by Hackers Using the Shadowpad Backdoor
Unpatched Microsoft Exchange servers in various Asian countries were the target of an attack campaig...
Data Breaches Could Occur Due to Kubernetes Misconfigurations That Were Leaked.
Over 900,000 Kubernetes (K8s) have been discovered to be vulnerable to malicious scans and/or data-e...

Attacks by Cybercriminals Will Become the Main Threat in 2024. Privacy Issues Tendencies
Internet Privacy is the main Concern today Advertisers track your online activities and interf...