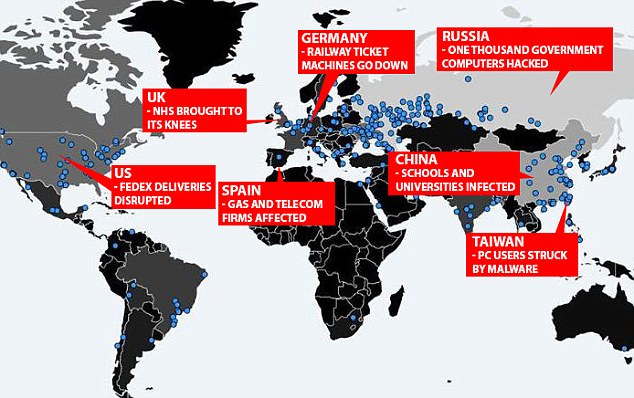
More than 45,000 cyber-attacks were recorded in nearly 99 countries around the world, including the UK, Russia, India, China, Ukraine, Italy, and Egypt. A ransomware cyber-attack that was supposed to have originated by mugging the ‘cyber weapons’ linked to the US government crippled a number of hospitals in England and spread worldwide in no less than 24 hours.
Relate article: what is torrenting and how it works
The chief scientist, Markus Jakobsson, from security firm Agari, said that the attack was ‘scattershot’ instead of targeted. He further said, ‘It’s a very broad spread whereas the ransom demand is relatively small.’
In the mid of April, the malware got leaked by a group called ‘Shadow Brokers’ from an archive of powerful software tools designed apparently by the National Security Agency –NSA – to defile and control Windows computers. However, not even a whole month later, the threat of rumoring that the criminals would use the leaked malware tool against the public turned out to be real and attacked hundreds of thousands of computers worldwide.
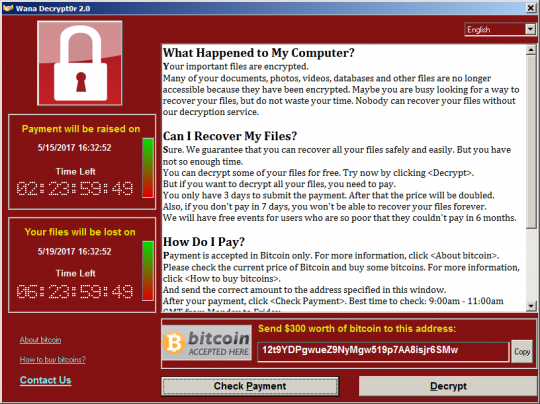
Ransomware is a sophisticated type of malware that encrypts a user’s data and then asks its victim to pay the demanded ransom in order to get their precious data recovered. This global attack was caused by ransomware namely ‘WannaCryptor 2.0’ or ‘WannaCry’ that exploits a vulnerability in Windows OS.
This ransomware spread worldwide, infecting thousands of computers and demanded a ransom of $300, which was threatened to be increased with the passage of time. And as time goes by, without the ransom being paid within the due time, the hacker(s) might make the data inaccessible. The malware spread through email and translations of the ransom message in 28 different languages was included.
Microsoft Condemns The Global Attack
A patch for this flaw was released by Microsoft in March, which was basically a software update that fixes the problem, but those computers that did not install the security update faced the peril of cyber attack. In its current statement, Microsoft indicated that its engineers had included the detection and protection against the WannaCrypt ransomware attack. A Microsoft spokesperson stated:
“Today our engineers added detection and protection against new malicious software known as Ransom:Win32.WannaCrypt. In March, we provided a security update that provides additional protections against this potential attack. Those who are running our free antivirus software and have Windows updates enabled are protected. We are working with customers to provide additional assistance.”
The malware was also been reported to reach universities, FedEx and Telefonica, along with the UK’s National Health Service (NHS). However, the global attack caused by the WannaCry ransomware came to a standstill by an ‘Accidental Hero’, after spending some dollars on registering a domain name hidden in the malware.

With the help of Darien Huss from Proofpoint security firm, the 22-year-old UK cybersecurity researcher – identified on Twitter as @malwaretechblog – generated a ‘Kill Switch” in WannaCry software. In case the creator wanted to stop it from spreading, the switch was fixed in the malware. This included the use of a quite long nonsensical domain name that the malware makes a request to and if the request returns and shows that the domain is live, then the kill switch knocks off the malware from spreading.
The UK researcher further said, ‘I saw it wasn’t registered and thought, “I think I’ll have that’.” He spent $10.69 on the purchase and found that the domain name was registering thousands of connections per second.
However, by the time @malwaretechblog registered the domain, it was quite late to aid Asia and Europe, where a number of organizations were infected. According to Kalembar, it gave people in the US enough time to develop immunity to the attack by patching their systems before they got infected.
It has to be noted that the Kill Switch won’t help those who already have their computer infected with WannaCry ransomware. It is also possible that there might even exist different other variants of the malware that may hypothetically continue to spread in the future next. For this purpose, some of these basic tips to prevent ransomware attacks might come in handy.
Share this article
About the Author
Rutaba Rais is Editor at Be Encrypted with focus on Technology and Internet Security. Apart from her Healthcare background, she has interests in Lifestyle, Journalism, and expressing her opinion by her writing. You can follow her on Twitter.
More from Rutaba RaisRelated Posts

Passengers’ Data Stored on User Devices, not on DigiYatra Storage, says India Govt
KEY TAKEAWAYS Unblocking streaming content from Amazon Prime is easy only if you know the reliable V...

NCSC Chief: Clear Rules Needed to Prevent Cyberspace Conflict and Struggle
A safe and secure digital world necessitates a clear definition and enforcement of international cyb...

‘Revive’ has been upgraded to a banking Trojan on Android
This month, Cleafy’s security researchers discovered a new Android Banking Trojan in the wild....

Asian Industrial Control Systems Targeted by Hackers Using the Shadowpad Backdoor
Unpatched Microsoft Exchange servers in various Asian countries were the target of an attack campaig...
Data Breaches Could Occur Due to Kubernetes Misconfigurations That Were Leaked.
Over 900,000 Kubernetes (K8s) have been discovered to be vulnerable to malicious scans and/or data-e...

Attacks by Cybercriminals Will Become the Main Threat in 2024. Privacy Issues Tendencies
Internet Privacy is the main Concern today Advertisers track your online activities and interf...