Everyone uses Wi-Fi, but most of them don’t know what threats it can lead you to. However, you can secure your Wi-Fi connection and prevent malicious threats by following these tips:
Wi-Fi connections could be unsafe when there are suspicious connections to them. But how could it be possible for someone to know how many illegitimate connections there are? Or it might be possible that someone is eavesdropping or snooping through your Wi-Fi.
Such vulnerabilities may prove fatal, as they could allow a neighbor or a hacker to access your identity by stealing bandwidth.
But it’s never too late. You can follow some useful steps to ensure your wireless security, which are easy and less time-consuming.
Tips to protect your Wi-Fi connection
Here are seven effective steps we have gathered so that you can have a secure Wi-Fi connection.
1. Change the manufacturer name of your wireless network
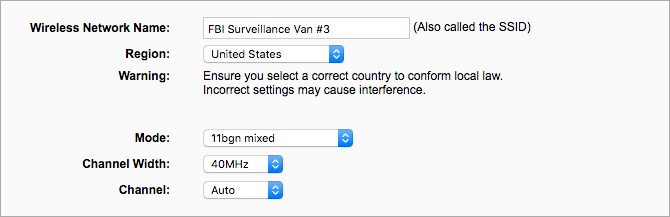
The most important step towards security is to change the existing name of your Wi-Fi network or router, also known as Service Set Identifier (SSID).
Resetting the Wi-Fi name will help you from letting a hacker guess the type of router you are using. The manufacturer’s information could cater to the cybercriminal in knowing the weaknesses of that particular model you have, and they could exploit them easily.
However, while changing the name, you must remember that it should not contain your name, for instance, “Finn’s Wi-Fi.” Such Wi-Fi names make your connection obvious to others’ snooping eyes. Yet, those who include much personal information in their network names are prone to identity theft and cyber-attacks.
2. Create a stringent password for your connection
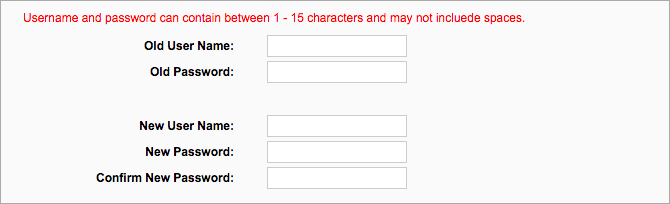
When you receive a wireless router, it already possesses a password that could easily be presumed by a data snooper, especially when he is familiar with the manufacturer of that device.
For a strong password, ensure that the password you create is a combination of numbers and alphabets, the insertion of symbols makes it more difficult to be guessed.
Yet, very few people would know that websites such as RouterPassword.com and Default passwords exist, where default admin credentials could be searched through router models. This means it’s child’s play for a hacker to access your router if he knows the router model.
3. Enable network encryption using WPA2 and AES
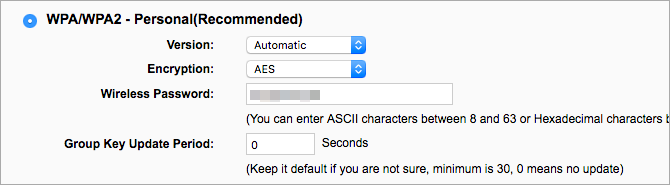
Encryption is a necessary tool for security purposes in all online deeds. Similarly, a router protected with encryption is difficult for an individual with malicious ambitions to access.
Enabling router encryption is a substantial feature. Yet, you must look for WPA2 Personal mode while resetting. If it’s not available, you could use WPA Personal. However, it is recommended not to use WEP mode, which can be easily accessed.
The recent version of encryption, AES, should be selected after setting WPA2/WPA mode. However, TKIP mode is not less secure, yet AES is preferable because of its modern features. Also, people testing the combination of AES and TKIP could fall prey to vulnerabilities. So, it’s better to remain with AES technology.
Finally, make a strong WPA2/WPA key on the password principles described above.
4. Enhance firewall protection
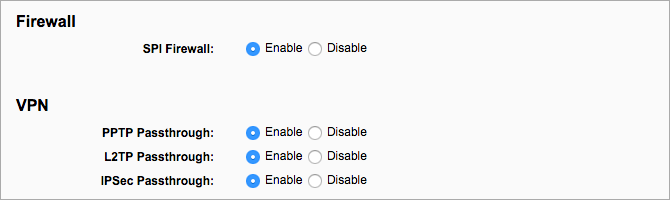
Like other devices and browsers, routers also contain vulnerability holes that are necessary to identify and patch up. For such protection, a firewall helps to scan the incoming data and restricts the data that seems illegitimate and vulnerable.
However, many routers are pre-installed with firewall features, such as the SPI firewall, which allows data after examining its legality.
The firewall protection is most likely enabled by default, but it is better to check if it is on. However, you could face some interruptions while playing online games. Such issues can be resolved by heading to Port Forwarding.
Besides, we still recommend you add protections with the router firewall. These router firewalls sometimes become weak against vulnerabilities, and unsafe data could get through them. Therefore, you must install antivirus software on your device to add a second layer of protection.
5. Disable WPS and UPnP
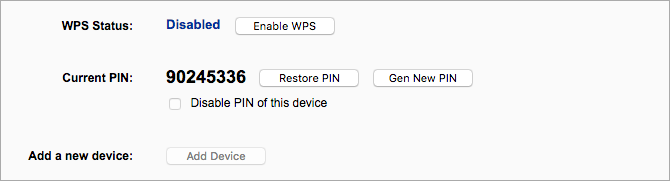
If the WPS (Wi-Fi protection features) is enabled, a new device can easily be added to your network. To disable this feature, you just have to press the WPS button on the router, then on the device, and voila, which will establish the connection. After that, you must disable the WPS as it can easily crack.
Universal Plug and Play (UPnP) makes a newly connected device visible to the other devices on the network. However, the UPnP design has obvious security vulnerabilities and flaws, so you must disable it as soon as possible.
6. Update the router firmware
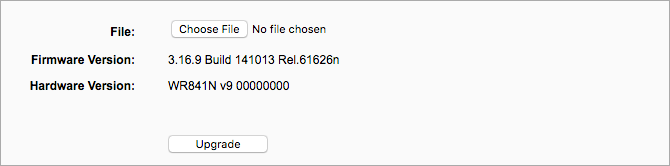
Most of the time, outdated software causes vulnerabilities. A software update is a must privacy measure for all kinds of security flaws and data issues. Likewise, firmware, the software that operates your router, also needs to be updated.
Outdated firmware is risky as pre-existing security loops could be exploited and cause vulnerabilities. However, new firmware could enhance security through extra features and improvements.
Update your device regularly. You can download these updates from the router’s manufacturer’s website, where you should look for your model.
7. Disable Wi-Fi connection when not in use
The simplest but necessary security preventive measure is disabling your network connection when not in use. While this practice doesn’t give you much protection, it lessens the chances of malicious access to your Wi-Fi network.
Is your network secure after these security modifications?
Many individuals think that such security measures couldn’t help much, or they presume it is a long procedure. Yet, the protections for your wireless router mentioned above are rapid cures to avoid vulnerability exploitation.
Following these steps does not fully guarantee protection against strong and advanced malicious intrusions, but it does make it really difficult. Therefore, never leave your device an easy target for illegitimate access.
Share this article
About the Author
Zehra Ali is a Tech Reporter and Journalist. She has done her Masters in Mass Communication. Topics related to cybersecurity, IoT, AI, Big Data and other privacy matters are extensively covered by her on various platforms. You can follow her on twitter.
More from Zehra AliRelated Posts
15 Best Data Recovery Software in 2025 – Free & Paid
KEY TAKEAWAYS Having reliable and advanced data recovery tools saves money, time, and reputation by ...
15 Best Free Cell Phone Tracker Apps in 2024
KEY TAKEAWAYS There are several phone tracking apps on the internet, with millions of users worldwid...
How to Get Free WiFi Anywhere with Privacy
KEY TAKEAWAYS Almost everyone needs the Wi-Fi connection to stay connected to the digital world. How...
10 Tips to Use Public Wi-Fi Securely
KEY TAKEAWAYS Public Wi-Fi is easily accessible at cafes, restaurants, airports, and other places. T...

How to Setup Wireless Network for Your Mac Computers
If you have two or more Mac computers and want to connect them for fast and hassle-free sharing of f...


