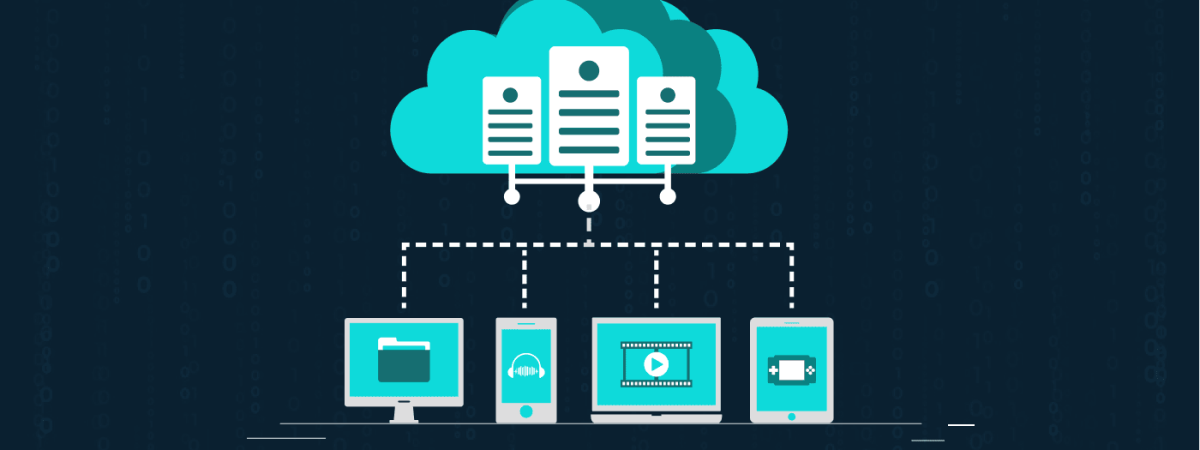
The information technology industry sometimes takes the lead itself. Cloud storage has become one of the most frequent, approachable, and affordable ways to stock up, store, share, or back up digital data in a secure place.
Users and individuals worldwide can easily access the data in these remote storage locations at any time, from anywhere. Cloud technology allows you to play around with your files without consuming more or any space on your computer’s hard drive or server network.
Companies mostly use cloud storage to securely store all official documents, use less space on storage appliances, and provide customers’ documents to their staff and employees anywhere in the world.
What is cloud storage?
Cloud storage is a technique or practice for storing, organizing, and securing essential data in a virtual cloud that numerous users can readily access.
The particular network only allows authorized users to access the data storage anywhere. Or, if we look at the broad concept of how a third party accumulates cloud storage works, that data is at an inaccessible location. These service providers have various tactics depending on the quantity of storage one needs for his computer.
Data gets sent out through the internet, and the users can have access to their stored data readily regardless of their location via the internet.
Benefits of using cloud storage
These services have been serving for an extended period, and we noticed that many people still don’t know what they can get from cloud storage services. So, let’s have a look at the primary benefits that one can have from cloud storage services:
- A secure and trustworthy system to backup your important files
- Files that are stocked up in the cloud can be returned remotely
- Files are handy from anywhere at anytime
- A frequent and reasonable way of shielding important data
- A pledge of restoration of data from any unwanted failure, malfunctioning, or data loss
- No necessity to install storage gear and equipment
- Provides flexibility and motility in the workflow of a company or business
Although these are just some of the central benefits of using cloud storage, the main perks are that you can access data from anywhere. The data is always accessible and readily available for restoration in case of any detrimental hard drive failure on your computer.
Uncertainty or risks of cloud storage
With Cloud Storage, there are many perks, but still, there are some flaws, and we can’t take it as a ‘foolproof service.’ Along with the goods and benefits, they also come with a few risks and uncertainties. It’s up to you to pick out the service providers that properly serve your principles, or else you may face some perils in the backup process. Below are a few risks attached to the usage of cloud storage:
- It requires a high-speed internet connection almost every time
- A third-party server accumulating your data
- When a supplier shuts its service for upholding, you may find it niggling to access your data
- If your suppliers shut their service enduringly, you may lose your important and valuable data
- The reliable services will charge you more for ample data storage
Many cloud storage service providers suggest a free preparation or plan to meet your general needs. In the case of managing or facing a massive mass of files or business fundamentals, cloud storage can be a logical way of protecting your data in the cloud.
The functioning standards
Let’s assume you want to store some data but don’t know how much storage you require. In such cases, you either buy more or less than you need.
This is where the cloud is helpful, as it’s auto-scaling, and you pay only for what you use.

The word cloud is a trope for the internet or the online world. Cloud storage is a mishmash of an online backup or storage service and cloud computing for data supervision. The service provider stores the information in a stack room full of computers called data centers.
Data centers can be found anywhere worldwide, relying on your storage supplier. Most cloud storage services ensure your files’ security and privacy by encrypting the data. Therefore, it cannot interrupted and read by malevolent third parties.

Users can stock up on all their files on a secure online site for a moderately low monthly fee and never fret about finding legroom. Files can be uploaded and downloaded with no difficulty. They are secure and safe and can be approached by you and anyone you approve.
Users can access it from anywhere, any place at any time, through any device using a web browser with alleviation. Such services can even automatically backup and sync files on any device without any extra exertion on the user’s part.
Additionally, by providing space, cloud storage can serve as a means to protect and secure your files and data from computer failure or malfunction. Also, breaching or any other event may permanently cause your valuable and important information to be lost. Having your data online will allow you to share some or all of it with your friends, family, co-workers, or anyone you want.
All you need to do is send them a link or log in with particular details, and they’ll be able to enter it, which is as easy as A.B.C.
Cloud storage breaches
In the last few years, cyber attacks on cloud storage services have increased from 30% to 44% of clients, and exposure scans have increased from 27% to 44%.
Without further argument, here is a rundown of history’s most reprehensible cloud security breaches.
1. Microsoft
Almost at the end of 2010, Microsoft had a breach that hinted at a configuration issue within its Business Productivity Online Suite. The problem permitted unsanctioned cloud service users to enter employee contact info in their offline address books. Microsoft asserts that clients had access to their data and that they preset the issue two hours after it cropped up.
While only a few users were perturbed, this happening is worth noting. It was the first significant cloud security breach and an indication of upcoming things.
2. Dropbox
In 2012, Dropbox had a severe breach; it wasn’t until four years later people knew what had happened. Hackers struck into over 68 million user accounts, email addresses, and passwords, signifying nearly 5 gigabytes of data. But this is not it! Those theft credentials reportedly made their approach to a dark web marketplace. The price for them was bitcoins.
At the time, this was approximately $1,141. Dropbox took action by requesting a site-wide password reset from the user base. They also went into some general spiel about its constant commitment to data privacy.
3. National Electoral Institute Of Mexico
Elections and shenanigans are generally going with affection. In April 2016, the National Electoral Institute of Mexico had a breach that took over 93 million voter registration records away. Most records were lost due to a feebly arranged database that made this private or confidential information publicly available to anyone.
The salt on the dish came when it was noticed that the Institute was storing data on an apprehensively insecure, illegally hosted Amazon cloud server outside of Mexico. Indicating the silent bargain and handshake.
4. LinkedIn
The business-optimized social networking site LinkedIn got the burn of cyber criminals when some 6 million user passwords were stolen and leaked on a Russian forum in 2012. Unfortunately, its splash of bad luck was just getting started. In May 2016, hackers breached and posted for sale on the dark web probably 167 million LinkedIn email addresses and passwords.
In addition to changing passwords, LinkedIn has implemented two-way authentication. This optional feature requires you to enter a PIN code on your mobile device before logging in to the network.
5. Home Depot
DIY retailer Home Depot reminded us of the financial consequences that may follow a significant security theft. In 2014, an attack demoralized the Home Depot point of sale workstation at the self-checkout lanes for months before someone finally noticed it. The tactical onslaught affected 56 million credit card numbers, making it the chief data breach of its kind at the time.
Home Depot paid well over a hundred million dollars in proceedings settlements and repaid the clients and financial institutions affected by the occurrence.
6 Apple iCloud
Jennifer Lawrence and many other celebrities had their private information and photos leaked online; at this moment, Apple endured what may be the worst high-profile cloud security breach due to the victims being drawn in. Many of the victims initially believed that someone had hacked their individual phones.
However, the iCloud service they used for personal storage was removed. In the comeback, Apple insisted on users utilizing stronger passwords and setting up a notification system that sends alerts when a doubtful account or suspicious activities are detected.
Cloud computing applications include Microsoft Corp.’s, Azure, and Apple Inc.’s MobileMe and iCloud offerings. The Microsoft Business Productivity Online Suite is also intended for marketable enterprises, according to a report;
“It was hit with a data breach in 2010, and customers of the BPOS cloud service apparently could download information on other customers of the suite, albeit inadvertently. The technology giant said it resolved the issue within two hours of its discovery, and only a few customers were involved.”
Some commercial cloud dealers have experienced breaches, such as GoGrid, which reported in March 2012 that ‘an unauthorized third party possibly had viewed its customers’ account information, including payment card data.’
They further added;
“The provider took immediate action, notifying federal law enforcement authorities and it believed the situation had been contained and that there was no indication that customers’ personally identifiable information had been shared with unauthorized parties.”
Tips and majors to keep your cloud storage data secure
With all that permissible vagueness, you have no option but to be in charge of your data and deal with it with accountability. Following are five data privacy guard tips to help you tackle the concerns of cloud privacy:
- Avoid storing sensitive information on the cloud, so if you have an option, you should choose to keep your important information away from the effective world or use suitable solutions.
- You should read the user agreement and context of the service you intend to sign up for; no doubt it is complicated and tedious, but habitually, the document that suffers from less attention may contain vital information you seek.
- Be attentively severe and responsible with your password creation; the more you keep your password complex, the harder it gets to crack.
- Encryption is, so far, the best way you can protect your data. The easiest and most versatile way to zip and encrypt files with a password is so that no one can see the file’s content without knowing the password.
- Using an encrypted cloud service is also wise. Some cloud services provide local encryption and decryption of your files, adding up to storage and backup. It means the service thinks about encrypting your files on your computer and storing them carefully and securely on the cloud.
Inclinational demanded services of cloud storage
Some companies are heading to provide the best of their services. Some of the most requested cloud services are given below:

Share this article
About the Author
Waqas is a cybersecurity journalist and writer who has a knack for writing technology and online privacy-focused articles. He strives to help achieve a secure online environment and is skilled in writing topics related to cybersecurity, AI, DevOps, Cloud security, and a lot more. As seen in: Computer.org, Nordic APIs, Infosecinstitute.com, Tripwire.com, and VentureBeat.
More from Iam WaqasRelated Posts
How to Encrypt Your Emails on Gmail, Yahoo, Outlook, and G Suite
KEY TAKEAWAYS Email encryption is necessary amid rising cyberattacks. It secures your email from thi...
How to Encrypt a Flash Drive on Windows, MacOS, and Linux
KEY TAKEAWAYS It is crucial to encrypt or password protect your flash drive, as they can be stolen o...
2 Best Ways to Encrypt Your Files and Folders in macOS
KEY TAKEAWAYS Many people use mac becasue of its robust privacy and security features. However, most...
How to Encrypt PDF Files on macOS and Windows
PDFs are the most common attachments in the email after docs. These lightweight, presentable documen...

How to Encrypt and Decrypt Folders in Windows in 2025
KEY TAKEAWAYS Windows is the most used desktop OS. However, it is vulnerable to cyberattacks. Theref...

3 Best Ways to Encrypt uTorrent or BitTorrent Traffic
KEY TAKEAWAYS You can adopt many ways to encrypt uTorrent or BitTorrent traffic, but the most reliab...