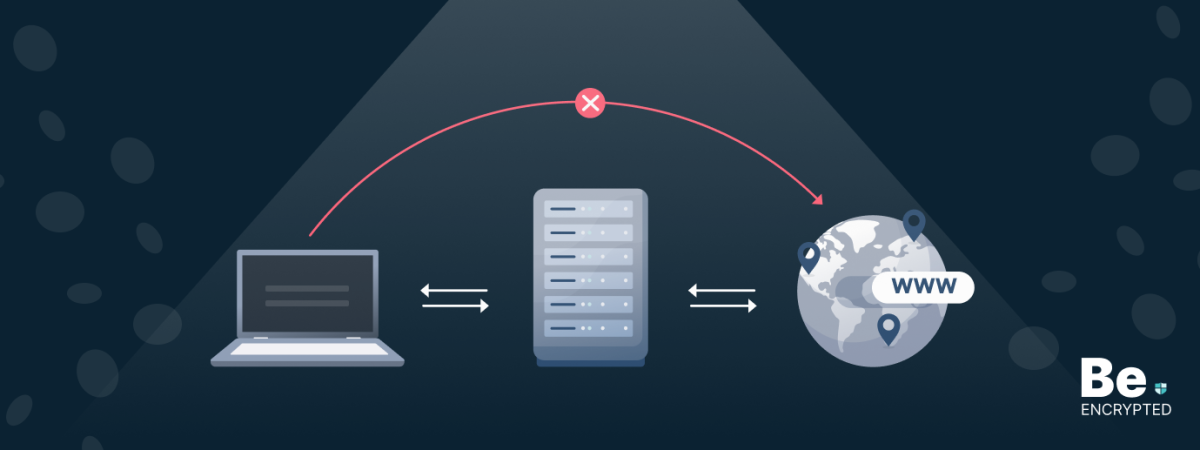
Torrenting is considered illegal in some countries. Therefore, it is advisable to use a proxy service or a VPN to hide your IP address while torrenting. Although proxy services don’t provide enough security, like encryption, they mask your IP address, which is enough for some users.
Setting a torrent proxy with uTorrent and other torrent clients is different. Our guide shows you how to do it properly step-by-step.
Note: People use torrent proxies because they don’t offer encryption, which results in fast downloading. However, torrent sites may contain malicious programs or track your online activity. Therefore, we recommend using a reliable VPN like NordVPN while torrenting.
Proxies are known for surfing the web anonymously. They offer a means to hide your real identity and IP address from the public. When you connect to the Internet through proxies, your computer’s IP address will not be shown; instead, the IP of the proxy server will be the Internet.
Proxies are numerous and can provide more privacy to users, but not all proxies work with the same terms and conditions. Some proxies are free for the public or charge a fee. It is entirely up to the user to decide which proxy to choose. However, it has been found that proxies that charge fees provide better security, are steadfast, and work much better and faster than unpaid proxies.
What type of proxy to use for torrenting?
The recommended type of proxy to use for torrenting is the SOCKS5 proxy. It is best for secure and efficient data transfer between the server and the client. However, when choosing a proxy service, ensure you go for a trustworthy provider with a good reputation and various proxy servers in different locations.
Some benefits of using SOCKS5 include the following:
- Improved speeds: SOCKS5 has a low latency that helps improve your torrenting speeds. They do so by reducing the data sent from your PC to the torrent swarm.
- Peer-to-peer support: SOCKS5 is designed to support a P2P network for improved and direct communication between peers and torrent clients. Therefore, it’s more suitable for torrenting.
- Proxy authentication: It supports username and password authentication to improve security. This ensures that only authorized personnel have access to the proxy server.
- Masking your IP address: SOCKS5 proxies allow you to mask your IP address and substitute it with the proxy’s IP address. This helps keep your identity private when torrenting.
What would a proxy do for your torrent client?
A proxy has various functions when you use it with your torrent client. They include:
- Anonymity: A proxy provides anonymity since your IP address is hidden. Routing your traffic through proxies ensures that your torrent IP address and browser IP address are different.
- Bypass geo-restrictions: Some regions impose strict internet restrictions, restricting the websites you can access. However, with a proxy, you’re masking your IP address and disguising it as a different person. This way, ISPs and government agencies can’t tell your real identity, enabling you to access geo-blocked sites anonymously.
- Bandwidth optimization for faster torrent transfers: Proxies optimize your bandwidth usage using features such as caching and compression. When torrenting, proxy servers cache frequently accessed sites making them load faster, thus improving your torrenting speed.
- Keep no user logs: When using a proxy, your browser IP address and the torrent IP address are entirely different. The only way to reveal your identity is by keeping your logs. However, the best proxy service providers don’t retain your internet logs. Therefore, always ensure you use a paid proxy server when torrenting.
How to setup a proxy in the uTorrent client
By following the steps given below, you can easily set up a proxy in the uTorrent client:
- Open uTorrent.
- Go to Options and then to Preferences.
- Click on connections.
- After going to connections, come to the proxy section for ‘’Type’’.
- In the Type section, choose HTTP, HTTP, or SOCKS5 (depending on the streaming sites you are using)
- Just next to the Proxy section is the Proxy field; type the IP address of the proxy server you wish to use.
- Then, in the port field, enter the port number.
- Enter your VPN username and password.
- Click on the ‘’OK’’ tab.
How to set up a proxy in a BitTorrent client
It’s important to note that BitTorrent is available in 3 versions: Classic, Android, and Web. However, proxy settings are only possible on the Classic version, which is available as a client program on macOS, Windows, and Linux.
Setting up a proxy in BitTorrent is relatively easy using these steps:
- Launch the BitTorrent desktop client
- Select ‘Options’ and click on ‘Preferences’ from the dropdown menu
- Navigate to Connection
- Under the ‘Proxy Server’ section, choose ‘Socks5’ on the dropdown menu
- Enter your preferred IP address under the ‘Proxy filed’
- Type the port number in the ‘Port field’ (This information is available from the proxy service provider)
- Under the ‘Authentication’ section, check the two options
- Under ‘Proxy privacy,’ check the three options
- Click ‘Apply,’ then ‘Okay’
- Restart your BitTorrent client program.
How to configure proxy settings on other torrenting clients
Configuring proxy settings on other torrenting clients differs based on your preferred torrent client. However, there are general steps to guide setting up a proxy:
- Open the torrent client you are using
- Go to ‘Settings’ or ‘Preferences’ menu
- Select the ‘Network’ or ‘Connection’ tab
- Go to the ‘Proxy server’ or ‘Proxy setting’ section and enable it
- Enter your proxy server’s IP address and port number
- Choose the proxy type (we recommend SOCKS5)
- If authentication is required, enter your credentials, including username and password.
- Click ‘Apply’ then ‘Ok’ to save the changes
- Restart the torrent client
How to verify that your proxy is working?
Different torrent clients handle failed proxy connections differently. Some route traffic via a regular connection, while others require you to enter the correct proxy settings.
Either way, you must confirm your torrent IP address to ensure that only the proxy server’s IP address is visible to your peers.
To test this, we use a free website that allows you to download a custom magnet link. After adding the link to the torrent client, the tool tells you the IP address visible to the peers and allows you to contrast it with your browser’s IP address.
This method is viable with all torrent clients:
- Visit checkmyip.torrentprivacy.com
- Download the tracking torrent by copy-pasting the magnet link address into the torrent client or by downloading the magnet link directly.
- Verify: In between 5 seconds and a minute, a popup should appear on the tracker page if the proxy functions correctly. At this point, a new proxy IP address should also appear. However, it should be distinct from the IP address you used to access the page initially.
- Use your torrent client to see your proxy IP address: There is no need to save the magnet or bookmark the webpage for future tracking. Instead, you can easily find your current torrent IP address by accessing your torrent client’s ‘trackers’ tab.
VPN or proxy: Which one is better for torrenting?
Not really. In most cases, people use both.
A significant proportion prefers using a VPN for private torrenting because it’s simple. A VPN doesn’t need in-client configuration, which can be tiresome and confusing for non-tech savvy. Additionally, VPNs offer encryption as an added advantage compared to proxies.
Most highly rated torrent clients support in-built encryption, but it’s primarily weak and unreliable since it depends on other peers having encryption. Therefore, using a VPN is better if you want to remain 100% secure and private.
On that note, most torrent monitoring is done using your IP address. A proxy hides it to ensure your ISP can’t monitor your internet activity.
Proxy has several benefits of its own, including;
- Lacks encryption: Normally, you’d need to dig deeper into your pockets to secure a top-rated encryption tool. Furthermore, encryption slows down your connection since traffic has to travel through secure servers to protect your data. However, with proxies, you can hide your IP address and retain almost 100% of your network speed.
- Torrent IP address and browser IP address are different: The difference between the two IP addresses makes it hard to distinguish between the downloaded torrent file and the one stored in your client. Each has a unique IP address; hence, you can’t link one to the other.
However, if you prefer hiding your IP address and encrypting your connection, just use a VPN and a proxy. First, you’ll need to set up a proxy in your torrent client and then connect to a VPN before launching your torrent program. This way, the torrents will pass through the VPN and the proxy tunnel.
There are benefits of using a proxy with a VPN, including:
- Your ISP can’t monitor your activity since your torrents will be secured with an encryption protocol.
- You’ll be using a different torrent IP address from the browser address.
FAQs
Share this article
About the Author
Rebecca James is an IT consultant with forward thinking approach toward developing IT infrastructures of SMEs. She writes to engage with individuals and raise awareness of digital security, privacy, and better IT infrastructure.
More from Rebecca JamesRelated Posts

Torrent Privacy Risks: How to Torrent Safely and Anonymously?
KEY TAKEAWAYS Torrenting comes with its risks, but they aren’t insurmountable. Here are some ...

21 Best Torrent Search Engines in 2024 (100% Working)
KEY TAKEAWAYS The best Torrent search engines work to provide reliable torrent links. However, torre...

12 Best Torrent9 Alternatives in 2025
KEY TAKEAWAYS The popularity of Torrent9 has declined over time. It is because it offers copyrighted...

10 Best Torrent Apps for Android in 2025 (100% Working)
KEY TAKEAWAYS If you’re looking for a torrent downloader client for your smartphone, then have...

20 Best ExtraTorrent Alternatives and Proxy Sites in 2025
KEY TAKEAWAYS Authorities shut down the official ExtraTorrent website and erased all of its content....

20 Best Kickass Torrents Alternatives in 2025
Kickass Torrents was one of the famous torrent sites, like the Pirate Bay, until the alleged ow...