Hundreds of free encryption software are available, not all meet our expectations. Therefore, we’ve finally come up with the best free encryption tools that most people trust on the internet. So, let’s learn about them one by one.
- VPN Software – It encrypts the data and hides the user’s location, and changes its actual IP address.
- Tor Browser – It is free and open-source software developed to make you anonymous and secure private communication.
- Cryptomator – It’s easy to use and compatible with Android, Windows, macOS, iOS, and Linux.
- VeraCrypt – It adds military-grade encryption to your data and even offers full disk encryption for free.
- AxCrypt – The encryption software automatically protects the files saved on Google Drive and Dropbox.
- 7-Zip – If you are a less tech-savvy person, diving deep into the menu can be pretty intimidating.
- AES Crypt – It is reliable and secure to use software that uses powerful AES-256-bit encryption to secure sensitive files.
Note: Encrypting your files and data is highly recommended, but using free software would be alarming; use a free trial instead. We recommend using NordVPN for encryption. The encryption tool offers 256-bit encryption and comes with a 30-day money-back guarantee.
Encryption is an excellent option for anyone who wants to transfer large volumes of data or ensure their data remains safe from data theft and other cyber-attacks. Encryption adds a layer of security and protection to your data stored in files and folders, so you shouldn’t ignore it.
Several encryption tools and software exist to maintain and protect your privacy. Many of them won’t cost you a single penny. Below is our top recommendation for the best free encryption software to secure your data.
Why use encryption software?
Encryption software works by using complex algorithms that jumble the data being sent. The encrypted content is decrypted using a key provided by the message’s sender. Only people who have the decryption key can have access to the data. In this way, the encryption software keeps the information safe and secure. Without using encryption software, you put your data at significant risk.
There are several benefits of using encryption software, some of which are as follows:
- Because of the COVID-19 pandemic, remote working culture has become quite popular. Employees are increasingly using their own devices for work. Cybersecurity risks also increase with the increased convenience and reliance on these devices. Laptops, tablets, and smartphones are easy to hack.
- Encryption software ensures security across many devices. It allows you to ensure that your data across any device is fully encrypted and eliminates the risk of invasion from any unwanted source. It gives individuals and businesses peace of mind because their data remains protected at rest and in transit. Encryption makes it impossible for anyone to access the data from outside.
- The encryption software prevents identity theft and ransomware blackmailing. Since all your files undergo encryption, cybercriminals cannot access your data. They only see scrambled data as useless and can’t be used to ask for a ransom.
- Encryption software used for data protection also helps increase the business’s integrity. Only authorized people can access the organization’s information for analysis or work. Moreover, it reduces the chances of a hacker tempering the available data.
7 Best free encryption software
Although hundreds of free encryption software are available, none meet our expectations. Many of them are vulnerable and can expose your sensitive data to threat actors. After thorough research, we’ve finally found the best free encryption programs that most people trust online. So, let’s learn about them one by one.
1. VPN Software

A VPN is one of the most effective encryption software out there. It encrypts data, hides the user’s location, and changes its IP address. Like other encryption software, VPNs are compatible with various devices and operating systems.
They are easy to use and download. A Virtual Private Network is reliable to use because:
- It encodes the traffic into deep packets in scrambled form, and no one can recognize it.
- It uses military-grade encryption to encrypt your traffic, sending it via a private tunnel that any snooping eye can’t breach.
- A VPN hides your IP address by redirecting your internet traffic through a remote VPN server in another location. In this way, a VPN spoofs your location and makes you more anonymous and private over the web.
- It will secure your downloads, whether it’s torrenting or streaming.
- It will bypass the ISP speed throttling and provide a faster connection.
While VPNs are the best encryption software, it is not recommended to use free VPNs to encrypt your data. Free VPNs come with security vulnerabilities that risk your digital privacy.
The free VPN lacks work as data miners. They collect and sell users’ data to third parties to make money. The advertisers bombard you with unwanted ads when you’re connected via their VPN.
Besides this, the free VPNs fail to encrypt the user data and lack basic security and privacy-boosting features such as a kill switch or DNS leak protection. As a result, users suffer from frequent data leak incidents.
The good news is that various premium VPNs are secure and reliable. Our most recommended paid VPNs regarding robust encryption include NordVPN, ExtremeVPN, and Surfshark. However, if you are on a budget and can’t afford a premium VPN service, you can take advantage of these VPNs’ free trials and money-back guarantee policies.
2. Tor Browser
- Website URL: torproject.org
The Tor browser is among the most trusted internet security and privacy names. It is free, open-source software developed to make you anonymous and secure private communication. The Tor network uses Tor’s distributed network of nodes to bounce your communication.
Tor browser hides your IP address and prevents anyone from monitoring your internet connection or learning about your location or the websites you visit. The anonymous browser is famous among journalists, social activists, and whistleblowers. It is reliable to use because:
- The Tor network consists of nodes that provide encryption in three different nodes and hide your activities on the internet. Each time the data passes through the node, it undergoes encryption. This way, Tor prevents you from ISP tracking or hackers’ surveillance of your activities.
- It comes with pre-installed extensions like No Script and HTTPS Everywhere that encrypts your communication with websites and result in a more secure browsing experience.
But, there are some significant flaws associated with the Tor browser. Since the Tor browser routes the data through different nodes, this results in a slow connection speed.
The browser doesn’t provide encryption, and you are not entirely anonymous. It’s because Tor encrypts the data with the nodes; when the data traffic leaves the final exit node to reach the destination, the information is not encrypted. Your data and IP address is visible to anyone monitoring your network, and they can easily recognize you.
Moreover, previously Tor has been cracked by the FBI, and even attackers launched SSL attacks on the Tor network. But you can resolve all these issues using a reliable VPN and Tor browser.
3. Cryptomator
- Website URL: cryptomator.org
Cryptomator is one of the best free encryption software designed for digital protection in the cloud. It is client-side software, meaning the vault of encrypted files resides within the cloud storage system.
Cryptomator allows you to access your files from multiple devices. It’s easy to use and compatible with Android, Windows, macOS, iOS, and Linux. Mobile apps offer more functionality than desktop apps. They directly integrate with Google Drive, Dropbox, OneDrive, and WebDAV-based cloud storage services.
The following mentioned features make Cryptomator compete in the list of best encryption software:
- The software is secure to use. It uses the state of the art AES-256-bit encryption and a password-protected script to hide file names, content, and headers. The encryption is transparent, meaning you can view the ciphertext stored once the encryption has finished.
- Cryptomator offers a unique Sanitizer feature. It is a console tool that is built for troubleshooting vaults. If there are any corrupted files in your vault or you can’t decrypt your files, you can use this tool to detect the issue.
- It works by creating virtual drives on your computer. You can open and decrypt it by using the Cryptomator software.
- The company has undergone an independent security audit. Cure53 has reviewed its cryptographic libraries. The software also uses an automated way of testing.
You can even share files and folders with other users of Cryptomator by giving access to your vault. Remember, two people at the same time can’t open the vault. It also prevents any malicious actors from accessing your files. But sharing files with people who don’t use Cryptomator is impossible.
As a whole, Cryptomator is a good option to use for anyone who wishes to keep their files and data private in the age of mass surveillance and data mining.
4. VeraCrypt
- Website URL: veracrypt.fr
If you are looking for free disk encryption software, VeraCrypt should be your top priority. It is an open-source program that allows developers to download and use the source code.
It adds military-grade encryption to your data and even offers full disk encryption for free. This encryption software can also secure external storage devices like the USB stick. It is an excellent alternative to TrueCrypt and improves features and performance each day.
VeraCrypt works well with Linux, Windows, macOS, and Raspberry Pi. All you need is to install it from its official site. Once you’re done downloading, create a new volume, mount that volume, and drag the files and folders you want to encrypt. Its main features are as follows:
- Like other free encryption software, VeraCrypt uses AES-256 military-grade encryption to encrypt the file system. This includes data, filenames, or any other thing which is related to the data. AES is the default encryption used by VeraCrypt. But you can also use different algorithms like Kuznyechik and Camellia.
- It uses hashing algorithms along with encryption to customize your protection. In other words, creating a password uses one of the five hashing algorithms to generate three keys. The master, secondary, and salt are developed, enabling you to decrypt your data with a master password.
- It comes with plausible deniability, which means that if by any means you are forced to give away your password, the hidden OS and volumes provide you extra protection.
Though VeraCrypt is reliable encryption software, it comes with flaws too. It lacks cloud integration or sharing features but outstands its competitor regarding local encryption.
5. AxCrypt
- Website URL: axcrypt.net
AxCrypt is another open-source file encryption software for small business teams and individuals. It has a free and a premium version available for Android, iOS, macOS, and Windows.
The encryption software automatically protects the files saved on Google Drive and Dropbox. AxCrypt makes collaboration more private and secure. It allows you to share your confidential files and collaborate with others. This way, you can work on any secret project you might not want to share with any third party.
Furthermore, key sharing enables users to share the encryption keys with multiple users to open the encrypted files with their encryption keys.
AxCrypt is reliable encryption software that comes with some excellent security-focused features like:
- It uses an advanced encryption system that ensures your files are impossible to crack. The software uses AES-128-bit and AES-256-bit encryption standards to protect and secure your files from bad actors.
- The software offers the anonymous file name feature, ‘ file wipe,’ for hiding your file names. By hiding the file names you want to protect, only those who access the files can see them. Also, you can permanently delete files from your device, and even if someone uses advanced file recovery software, they can’t recover those files.
- Besides encrypting your files, it also keeps your accounts protected from cyber-attackers invasion. AxCrypts provides password management features that protect all your passwords in a single dashboard. Moreover, it helps generate and remember impossible-to-crack passwords for all your accounts.
The free version lacks features like the file wipe available in the premium version. Overall, it is secure, simple, and easy-to-use encryption software that offers additional features to increase your file security protection.
6. 7-Zip
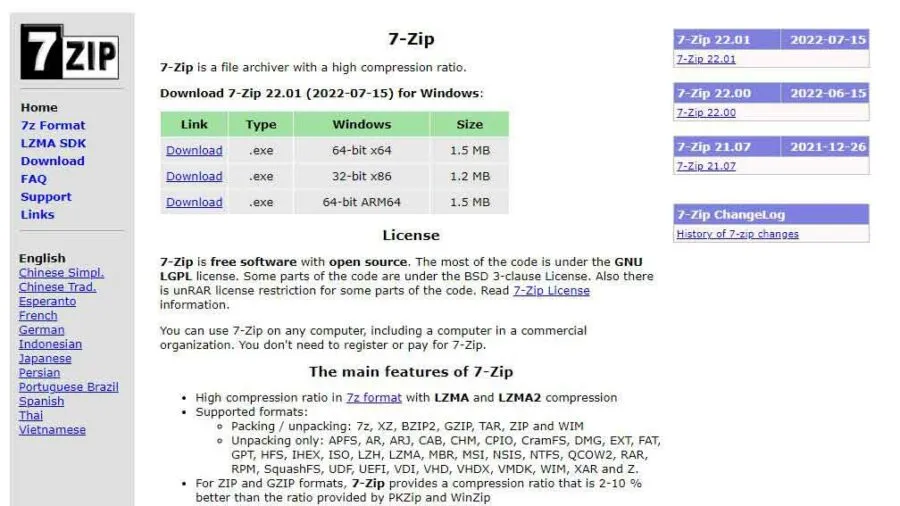
- Website URL: 7-zip.org
7-Zip is a robust, free encryption and file compression software supporting various formats. It is easy to use and is available in more than 79 global languages. If you are less tech-savvy, diving deep into the menu can be intimidating.
You can install 7-Zip on Linux, Windows, and macOS. One should use this encryption software because:
- You can encrypt all your files and password-protected files with AES-256-bit encryption. It generates a key from a user-supplied passphrase using an algorithm based on the SHA-256 hash function. Since the SHA-256 is executed 262144 times, it slows speed before the extraction and file compression begins. The technique is also called vital stretching; it’s used to make a brute-force search for the passphrase even more difficult.
- It offers a new file compression format named ‘7z’. The file format compresses the files more securely and efficiently than other formats like Zip or RAR.
But, there are chances that hackers or scammers might create a file with the name 7-zip that contains spyware, malware, ransomware, or viruses to compromise your data. To avoid it from happening, download the software from its official website. You can also use a VPN or anti-malware software with 7-Zip for maximum protection.
7. AES Crypt
- Website URL: aescrypt.com
The last best free encryption software on our list is AES Crypt. It is reliable and secure to use software that uses powerful AES-256-bit encryption to secure sensitive files. Once the encryption is complete, there is no need to worry about anyone viewing your files because they won’t access the encrypted files unless they enter a password.
The software is available for Windows, macOS, and Linux, allowing you to encrypt individual files manually. Unfortunately, it doesn’t support batch file encryption, but you can overcome this by creating zip files out of folders and then encrypting them with the software.
With AES Crypt, file decryption occurs by double-clicking the encrypted files and entering the password. When you create an encrypted file version, the original unencrypted version remains. For maximum security, it’s better to delete the original files because if, in any case, cyber-criminals get access to it, it can put you in great trouble.
According to its website, the encryption software also offers a password generator feature. The feature stores passwords and helps create complex and unbreakable passwords for your account.
Users blamed the software for having security issues exposing their sensitive information. But, the software company hasn’t resolved the vulnerabilities anytime soon.
Share this article
About the Author
Waqas is a cybersecurity journalist and writer who has a knack for writing technology and online privacy-focused articles. He strives to help achieve a secure online environment and is skilled in writing topics related to cybersecurity, AI, DevOps, Cloud security, and a lot more. As seen in: Computer.org, Nordic APIs, Infosecinstitute.com, Tripwire.com, and VentureBeat.
More from Iam WaqasRelated Posts

How to Encrypt Your Emails on Gmail, Yahoo, Outlook, and G Suite
Encryption is, so far, the best possible way of securing your emails. With encryption, your informat...

How To Encrypt or Password Protected A Flash/Thumb Drives
Encrypt All types of Thumb, Flash, USB, and portable drives. An easy step-by-step guide to complete ...

2 Best Ways to Encrypt Your Files and Folders in macOS
KEY TAKEAWAYS Many people use mac becasue of its robust privacy and security features. However, most...

How to encrypt PDF files on macOS and Windows – Complete Guide
PDFs are the most common attachments in the email after docs. These lightweight, presentable documen...

How to Encrypt and Decrypt Files / Folder In Windows in 2024
Windows is admittedly popular and unexceptionally easy to use. However, you might also know it is on...

How To Encrypt uTorrent And BitTorrent Traffic – Best Easy Ways
KEY TAKEAWAYS You can adopt many ways to encrypt uTorrent or BitTorrent traffic, but the most reliab...





