By monitoring the dark web, organizations can stay protected and remain on the latest trends in cybercrime. It is the perfect time to start if you’re not using any dark web monitoring services.
Here’s the list of the best dark web monitoring for individuals and business organizations:
- ZeroFox – It uses an advanced AI-powered search engine to inspect the dark web deeply.
- ACID Intelligence – This tool relies on a cluster of robots to monitor and scan various darknet resources.
- DarkOwl Vision – It uses Boolean and Regex-supported search logic to scan thousands of darknet sites and other platforms.
- CrowdStrike Falcon X Recon – It looks into thousands of darknet platforms to provide insight into over eight years of data.
- Have I Been Pwned – A free website that informs about login credentials being compromised and leaked on the dark web.
- SpyCloud ATO Prevention – It uses AI and ML technologies to monitor and track dark web data and is best suited for large-scale organizations.
- DigitalStakeout Scout – This tool monitors the Active Directory that prompts users to change their passwords.
- Digital Shadow SearchLight – It alerts the user about any threat in the monitoring dashboard so they can take safety measures.
- Ecosec Systems – This provides in-depth dark web risks and enables security teams to take preventive actions.
- Cobwebs Technologies – It automatically scans dark web marketplaces and other platforms and sends custom alerts.
- Dashlane Business – It allows adding up to five email addresses and getting real-time insights about security breaches and other online threats.
- Keeper Security – Breach Watch is a Keeper password manager dark web monitoring tool that scans records from billions of resources and notifies the users.
- WhatsUpGold – It uses Network Traffic Analyzer to monitor Tor and other doubtful sites.
- LastPass – It monitors users’ email addresses for potential data breaches. Best suited for individuals and small businesses.
Note: If you are on a budget and not much tech-friendly, we recommend using NordVPN. It comes with the dark web threat protection which is similar to the other expensive dark net monitoring services on our list. In addition, the VPN will keep you anonymous and protect your online activity by encrypting the online traffic.
The dark web’s anonymity makes it a hub for illegal and nefarious activities. Cybercriminals use the dark web to sell stolen business data and personal information like usernames, passwords, and credit card details. It is highly alarming as the stolen data is later used for identity fraud or to commit crimes. This increases the need for dark web monitoring tools.
Using dark web monitoring scanners, individuals and companies can proactively map, monitor, and reduce the rising digital threat landscape. They can protect their sensitive data, intellectual property, and brand reputation from emerging threats. Individuals can also take action, such as changing their passwords and boosting their privacy.
Read along as we hand-picked some of the best Dark web monitoring services that work in 2024.
What is dark web monitoring?

Dark web monitoring is using a service to search and track organizations’ information available on the dark web. These tools use a combination of manual and AI-powered scans to extensively monitor and track the dark web and its forums, websites, and private networks. By continuous tracking and monitoring, these tools help in finding leaked or stolen information such as:
- Breached credentials
- Compromised passwords
- Intellectual property
- Social Security Numbers
- Phone numbers
- Credit/Debit card numbers
- Email addresses
- Usernames and other sensitive information
These tools classify the security risks and provide visibility into threats that traditional security tools fail to discover. When the tool detects a threat, it creates alerts and notifies the team members and everyone else within the organization so they can take action to minimize the risk. With these tools, businesses can find indicators that can result in a breach. Also, they gain insights into the attacking methods and develop a cyber defense strategy.
All in all, dark web monitoring services are great tools for identifying the exposed data and the time your data remains exposed. Anyone committed to protecting their data, be it an individual or a business, must consider using them.
14 Best dark web monitoring services of 2024
Dark web monitoring tools provide an uncut view of the current cybercrime landscape and cyber attack trends on the dark web and provide actionable alerts to companies and individuals.
Like other cybersecurity solutions, the functionality and features of dark net monitoring tools can vary slightly. Let’s search the 14 best dark net monitoring tools and decide which suits you the best.
1. ZeroFox Dark Web
- Website URL: zerofox.com
- 24/7 monitoring of credentials, IP, PII, and other sensitive data
- Provides extensive details of the compromised data
- AI-powered platform
- Full-spectrum threat intelligence and expertise
- Protects assets from OSINT and deep/dark web sources
- Breach-responsive service
ZeroFox is a leading cybersecurity platform that offers unified solutions to uncover malicious activities and cyber threats. Part of this SaaS-based platform is its Dark Web Monitoring solution that provides early warnings about information leaks and contextual analysis of cyber-attacks and offers actionable alerts to protect clients, brands, and employees. Companies looking for continuous in-depth dark web monitoring must try out this tool.
ZeroFox analyzes text images and videos and remediates threats faster by employing the industry’s advanced AI-powered engine. It enables Digital Risk Protection and easily integrates into SIEM, SOAR, TIP, Business Intelligence, and other technologies.
Besides this, by continuous scanning and monitoring, ZeroFox safeguards businesses against data breaches and illegal data sales on various deep and dark web forums and websites, like ZeroNet, Tor, I2P, and Paste Sites. It also ensures that businesses never miss out on any critical alert that might put their sensitive data at risk. This allows security experts to involve cybercriminals and negotiate the return of sensitive data, which is rare in other monitoring solutions.
The dark web monitoring tool’s interface and ease of use make it an organization’s popular choice. With a single click, users can take all essential actions. ZeroFox’s dedicated OnWatch Managed Services team works 24/7 throughout the year to protect brands from digital threats. This solution allows users to request a free demo before buying the product, which is impressive.
2. ACID Intelligence
- Website URL: acid-tech.com
- Wide coverage of credential monitoring, IP, and brand
- AI-powered algorithms for effective search results
- Tailored threat detection
- Real-time alerts
- Actionable advance alerts
ACID Intelligence is a leading threat intelligence company that protects companies from cyberattacks on the dark web. It continuously scans and monitors the dark web forums and websites to detect attacks early in the planning stage. After in-depth analysis, it provides real-time information about the potential attacks targeting the organization. It also prepares a response strategy to reduce the consequences and avoid them in the future.
The security-focused solution uses a cluster of robots that deploys AI algorithms to monitor a wide range of deep and dark web resources. When the monitoring tool identifies potential threats, it displays them in a centralized dashboard and sends real-time alerts. These alerts prove invaluable to organizations as they can optimize their responses and implement the most effective tools to control the threats based on their intensity.
Being one of the best dark web monitoring tools, ACID works throughout the year and investigates deeply into the dark web to find any clue of malicious activities targeting the clients. The most notable thing about this service is that it automatically and constantly updates the technological tools that deal with the latest threats and attack methods.
This dark net monitoring tool is best suited for all mid-sized to corporate-level organizations. As it is a paid security solution, organizations can directly request a demo or contact the team to hear about the pricing plan.
3. Dark Owl vision
- Website URL: darkowl.com
- Customizable search options and threat alerts
- The alerting dashboard provides active results from automated searches
- User-friendly app
- API for feed integration
- Boolean and Regex-supported search logic for most querying needs
DarkOwl is a leading darknet company that provides the largest commercially available database of darknet content worldwide. Part of the DarkOwl product is Vision UI, which enables users to monitor, search, and analyze the dark web and provides real-time threat intelligence.
Vision UI is an easy-to-use app that offers an intuitive and user-friendly interface backed up with querying solid capabilities to search, monitor, and create alerts for users’ sensitive information. The investigation begins by entering the keyword or other operator in the search bar. The Boolean and Regex-supported search logic allows deep and highly targeted queries.
The company continuously updates the database from thousands of darknet sites and other specific platforms like Tor, Discord, Paste sites, and Telegram.
Furthermore, users can also set filters like entities and search builders to define particular variables to return, like IP addresses, email, and cryptocurrencies. For any organization looking for a solution that searches and monitors the dark web across various sources, then DarkOwl is the best option. It offers a complete package that users always look for and thus emerges in the best dark web monitoring tools list.
4. CrowdStrike Falcon X Recon
- Website URL: crowdstrike.com
- Available 24/7 to monitor and handle alerts and incidents
- Best suited for all business types
- Provides customizable threat alerts
- Real-time and practical threat warnings
- Fast and efficient investigation
CrowdStrike is a pioneering cybersecurity leader in business for almost a decade. It offers various security solutions but markets its dark web monitoring tool as the CrowdStrike Falcon X Recon. It’s designed to help organizations of all sizes and types detect data leaks and breaches, monitor and track fraudulent activities, and the tools cybercriminal uses.
This dark web monitoring tool looks into thousands of darknet platforms, pages, and forums to provide instant access to over eight years of data. Digging out the raw intelligence data about fraud activities, enterprise threats, and stolen data of old-time gives CrowdStrike Falcon X Recon an edge over its competitors.
On the top, you can continuously monitor the hidden underground environments for threats without creating complex queries. The investigation results appear in a customizable dashboard, and the users can review the results in the original language and translate them into other 18 languages.
It has a Universal Search engine that automatically allows users to relate Falcon Intelligence Recon results with other CrowdStrike modules. The dark web tool offers two subscription packages. The Express plan is best for SMBs, while the other is for mid-sized and large organizations. Moreover, you can integrate this solution into primary tools like SIEM and SOAR, making it one of the best dark web monitoring solutions.
5. Have I Been Pwned
- Website URL: haveibeenpwned.com
- Free to use
- Comes with a password generator
- Searches on email addresses and phone numbers
- Perfect choice of individuals
- Doesn’t use AI algorithms
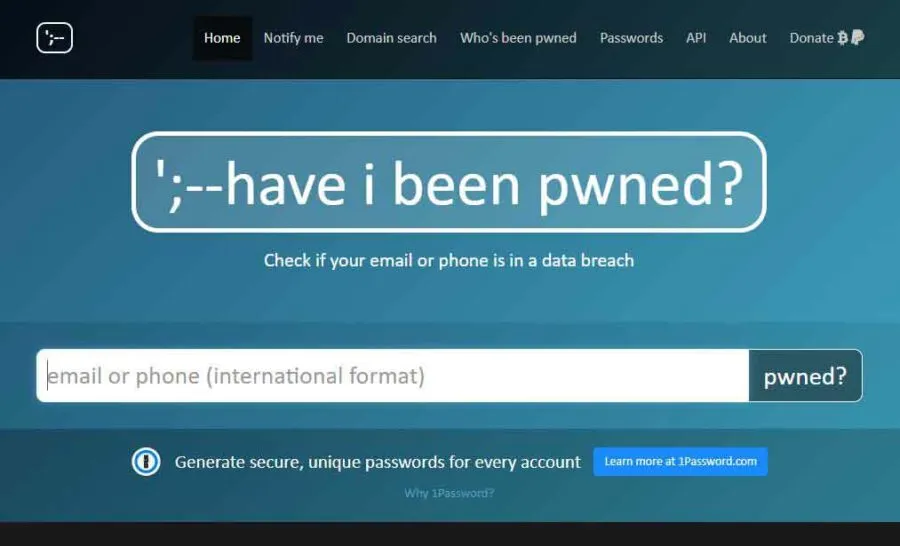
Have I Been Pwned is a free dark web monitoring tool popular for individual users. Created by Troy Hunt, an Australian web security consultant, it discloses whether your login credentials and personal and financial data have been stolen or leaked online.
The tool collects and analyzes thousands of database dumps and pastes the information about billions of leaked accounts. It also sends email alerts about new data breaches. The website possesses a simple and easy-to-use interface.
It has a dedicated search bar where you can enter your email address or phone number to determine if it’s compromised in a data breach. The most impressive part about this security tool is that it encourages users to change their passwords.
Besides this, you can also receive email notifications whenever your information is available in a recent data breach. Also, if you want to, you can remove their email address and use your email address to prevent others from looking to get more information linked to your email address. This way, users can take steps to mitigate the risk of identity theft and online fraud. It is free software but accepts donations via bitcoins or PayPal to run its service.
6. SpyCloud ATO prevention
- Website URL: spycloud.com
- Active directory and strong password policies
- Identifies compromised user accounts
- Account takeover and fraud detection and prevention
- Early breach notification
- Best suited for MSPs and corporate organizations
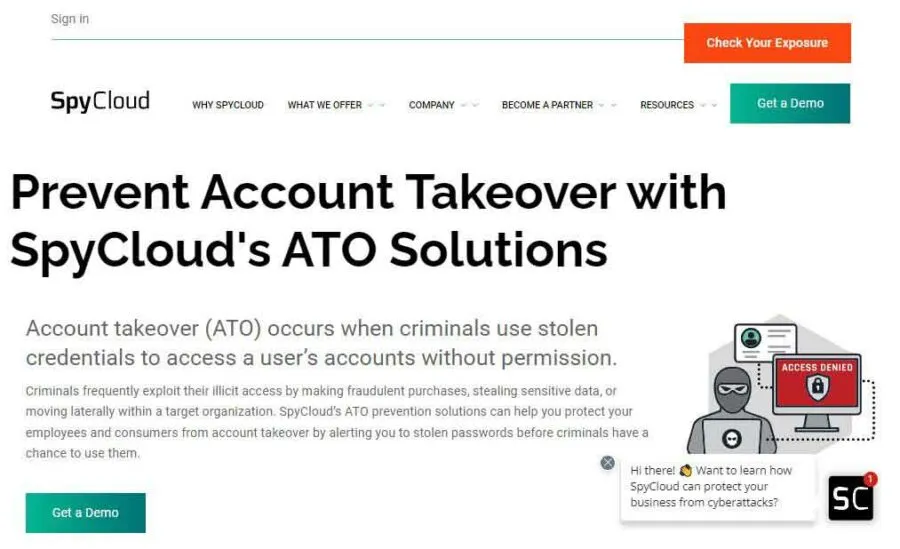
SpyCloud is a renowned cybersecurity vendor that provides a good range of cybersecurity solutions to protect users against threats and cyber-attacks. ATO Prevention is the dark web monitoring tool that safeguards users from account takeover by warning them about compromised passwords before malicious actors can use them.
The dark web monitoring tool utilizes a combination of automated scanning and human intelligence to scan dark web communities, pages, and sites that are not accessible to ordinary scanners. It also actively monitors Active Directory, automatically prompting users to change their passwords soon after discovering a data breach. This fantastic feature makes ATO Prevention twice as good as other dark web scanners discussed here.
The security researchers assess the breach data early in the breach timeline. This allows the end users to validate user identities and reset passwords before the hackers misuse them. Besides this, it offers visibility and a cloud-based threat intelligence database that helps the security teams stay one step further from the cyber-crooks and check user logins against the most extensive database of recovered breach assets globally.
Organizations, preferably mid-sized and large-scale, can consider using this security solution. Request a free trial to see how effectively ATO Cloud performs.
7. DigitalStakeout Scout

- Website URL: digitalstakeout.com
- Automated open-source intelligence
- 15 dashboard views
- Protects and defends the company’s reputation
- Detects all forms of cyber attacks
- Uses Machine Learning to detect abnormal behavior
Another reliable dark web monitoring tool that’s the best choice for all sizes of businesses is DigitalStakeout Scout. This dark web threat intelligence service uses automation to monitor the surface and deep web, news sites, and social media to provide more in-depth results. By monitoring the potentially harmful material about the organization, Scout safeguards the brand reputation and maintains the data’s integrity.
The security solution includes machine learning technology that detects abnormal behavior within the network. Upon detecting a threat, Scout raises an alert in the monitoring dashboard. It is then up to the network administrator to manually shut down the network traffic or use any protection software. One impressive thing about this tool is that it has over 50 dashboard views that allow security teams to investigate and analyze insights and search the data.
Scout is the most preferred choice of users because of its dark, solid web monitoring capabilities, automated alerts, and real-time intelligence. Another prominent feature of this tool is that it functions as a data loss prevention system, endpoint protection system, and insider threat defender.
This security-focused solution offers different pricing plans, but requesting a demo to know if it meets your standards is better. However, the tool’s most disappointing element is a 24/7 live chat option. This means the only way to contact the support team directly is to submit a ticket.
8. Digital Shadow SearchLight
- Website URL: reliaquest.com
- Searches passwords, VIP, and executive threats
- The automation feature gives a quick action response
- Uses advanced data analytics and API integrations
- Investigate instantly with MITRE techniques
- Free trial available
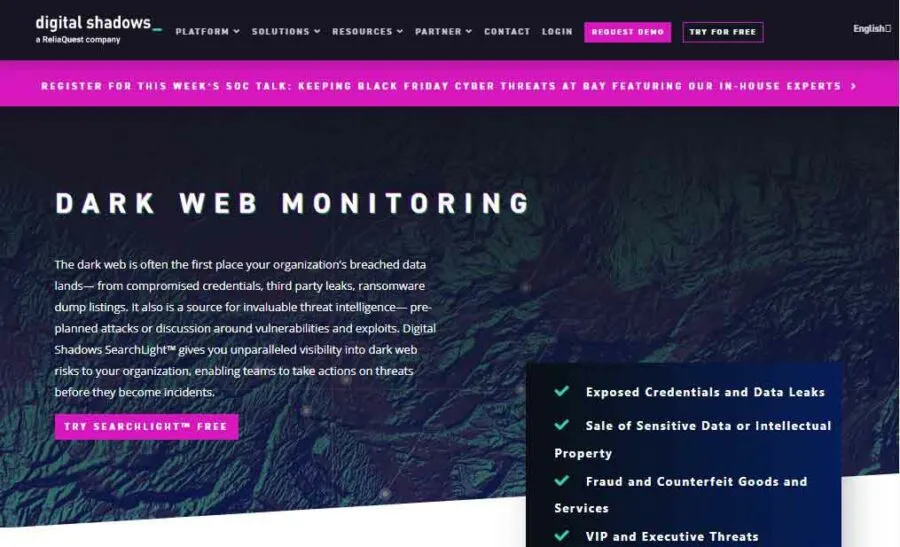
Digital Shadow enjoys a dominant position as a cybersecurity vendor. SearchLight is part of the service that provides unparalleled visibility into the organization’s dark web risks. It delivers alerts and can assess an extensive threat intelligence library and historical archive of dark web data for over ten years. In addition, it enables security teams to take immediate action on threats before they cause any damage.
This tool monitors extensive dark web resources for exposed credentials, intellectual property, fraudulent activities, stolen data, VIP and executive threats, and more. It inspects underground marketplaces, Telegram, IRC, Tor, I2P pages, forums, and paste sites and sends alerts to notify the affected organizations.
The best part of SearchLight is that users can try it for free for seven days. Organizations, preferably small and mid-sized, can get instant insights into dark web pages, criminal forums, and threat feeds and get 200 threat intelligence profiles of threat actors, campaigns, and tools.
9. Ecosec Beacon Systems
- Website URL: echosec.net
- Automated data collection
- Provided analysis reports on threat trends
- Free trial available
- Gathers sources from extensive dark web sources
- Relies on Machine Learning technology to provide custom alerts
Ecosec Beacon Systems is one of the leading publicly available information (PAI) and open-source intelligence (OSINT) providers. The service leverages Machine Learning to classify threats, send custom alerts that disqualify noise, and draw the company’s attention to serious issues. It locates compromised passwords, hijacked financial data, and personal data leaked on the web.
Enter a name, email address, SSN, or other relevant information to begin the search. The system automatically scans dark web marketplaces, forums, and social media sites to check whether the information is sold or displayed on an open free list. Also, it searches websites with the individual name or information that cybercriminals use to target a person. This way, EcoSec detects data breaches and tracks information involving individuals and business organizations.
As a whole, EcoSec is a great tool for using the deep and dark web and gaining visibility and alerts on insights into discovered data theft practices.
10. Cobwebs Technologies web investigation platform
- Website URL: cobwebs.com
- AI-powered analysis generates actionable insights
- Most useful for large organizations
- Automatically scans and updates the database
- Extracts result from all layers of the web
Cobwebs Technologies is a leading global security and intelligence provider transforming web intelligence’s face. This dark web monitoring tool enables seamless analysis of publicly available data resources available on the darknet. Part of its service is the threat intelligence solution that automatically scans and updates the databases with new information collected all around the web.
The security solution is a top choice for users because of its simple installation and scaling process that adapts to organizations’ growing needs. It deploys AI and ML technologies to analyze data across different web layers. In addition, this platform generates actionable insights and real-time threat alerts that let analysts respond to threats more efficiently and effectively.
Cobweb Technologies is the perfect choice for large-scale enterprises working at private and governmental levels. Anyone who wants automated Al and ML-based web monitoring features in their dark web security solution must try this tool.
11- Dashlane business
- Website URL: dashlane.com
- Scan up to five email addresses
- Detect, assess, and prevent security risks capabilities
- In depth-analysis of the dark web data
- Built-in password generator and manager
- Boost security with a built-in VPN
Dashlane is a popular password manager, but it excels in basic password management functionalities and includes a unique dark web monitoring tool. It notifies users of any leaked passwords and encourages them to act immediately.
The dark web monitoring tool scans billions of accounts and passwords available in the dark web’s databases and flags the exposed ones. Organizations’ IT admins can get real-time insights and alerts about security breaches and other potential threats and vulnerabilities that employees face. In addition, it offers simple actions they must take to reduce the risk of such threats in the future.
Dashlane’s dark web tool is an easy-to-use tool that lets users boost their account security with a single click. You can add up to five email addresses and run an initial scan that searches deep to find any compromised information linked to the email address. The scan results are sent via email, pop-up messages, and dark web alerts.
To benefit from the Dashlane dark web monitoring tool, subscribe to its premium plan. However, you can test this feature if you first opt for the free-trial version. Privacy-conscious individuals, start-ups, and SMBs can prefer using this tool.
12. KeeperSecurity
- Website URL: keepersecurity.com
- Unlimited scans
- In-depth monitoring of the dark web
- A free trial version is available
- Enterprise-level risk assessment and visibility
- Uses zero-knowledge architecture
Breach Watch is a dark web monitoring add-on tool of Keeper Password Manager. This powerful feature enables users to monitor the dark web for compromised accounts and matches them with the records stored in the vault. It works by continuously monitoring and scanning billions of records on the dark web while deploying zero-knowledge architecture that further boosts security.
The dark web tool works on all devices and major operating systems, ensuring a secure and hassle-free user experience. If it finds any alerts, it provides automatic notification records in the vault. In addition, it lets users change the breached passwords within the app, which is another impressive aspect of using this service.
BreachTower is a premium add-on feature of a Keeper password manager. It best suits organizations and prevents credential stuffing and account takeover attacks.
13. WhatsUp Gold
- Website URL: whatsupgold.com
- Leverage on Network Traffic Analysis
- Tor tracker
- Options to block malicious traffic
WhatsUp Gold is a prominent network monitoring system with several add-on modules. Network Traffic Analyzer is one of them that monitors Tor and other suspicious traffic. The Flow monitoring or NTA identifies traffic to known dark web entry or exit nodes. It alerts you when the users or applications connected to your network access the dark web.
On top of that, it also recognizes traffic or some specific suspicious IP lists. Plus, it allows you to set up a list of IP addresses that you find suspicious. All this makes it an option to compete as the dark web tool.
14. LastPass
- Website URL: lastpass.com
- In-depth analysis of the dark web
- Best for individuals and SMBs
- Generate and store passwords within the app
- Intuitive UI and easy-to-use
- Dedicated apps for all major OS
The LastPass password manager also comes with an impressive dark web monitoring tool. It’s an add-on feature included in the Security Dashboard, which gives an overview of the health and security of the stored credentials. Besides assessing the security of the passwords and updating the weak and reused passwords, you can also monitor your email address for potential data breaches.
The security tool asks users to enter their email addresses, continuously scan breached credentials within a database, and immediately alert them if they have been compromised. However, this feature is accessible to all premium users.
Its ease of use and other features make it the preferred choice for individuals, families, and small and mid-sized organizations.
Features to look out for in the dark web monitoring services
The monitoring tools regularly swap thousands of dark web pages and notify you if they find any stolen data. It is a time-consuming process that also requires experience in dark web analysis, plus the efficiency of the tool matters. However, not all dark web monitoring products are equal. Thus, while selecting a solution, look for the following features:
- Social media insights: Monitoring dark web forums, pages, and websites can give great information. It’s best if the dark web tool you select uses monitors and analyzes them.
- Geolocation ability: Select a monitoring tool that provides geofencing ability to help locate the source of information on the dark web.
- Dark web search engines: Dark web search engines make searching and accessing various sites and forums easy. Thus, check if the tool you choose offers darknet search engine access.
- Free trial period: The monitoring tools are more expensive than most security tools. It’s good to test the product before buying it. Thus, choosing a dark web monitoring tool offering a trial period is a plus.
Besides this, ensure the tool offers a range of extra features, such as search filters and results, free consultation, and reports that ensure a hassle-free experience.
How to prevent data leaks on the dark web
Besides using a dark web monitoring service, you can follow the tips below to prevent your information from getting leaked on the dark web:
- Using a reliable VPN provider is advisable when visiting the dark web for anonymous communication, digging out facts, or accessing dark web news sites. A reliable VPN provider encrypts the data traffic and makes it impossible for prying eyes to know who you are and what you are doing on the web. Also, the best VPN providers come with security-centric features that maintain privacy on the dark web and eliminate the chances of data leaks.
- Hackers can gain access to sensitive information using various methods, such as phishing scams, malware, or keyloggers. Installing reliable antivirus software can help you protect against malware and other online threats.
Above all, make sure you use strong passwords and store them safely. It is advisable to use the best password managers that generate strong passwords and store them in a secure encrypted vault.
FAQs
Share this article
About the Author
Waqas is a cybersecurity journalist and writer who has a knack for writing technology and online privacy-focused articles. He strives to help achieve a secure online environment and is skilled in writing topics related to cybersecurity, AI, DevOps, Cloud security, and a lot more. As seen in: Computer.org, Nordic APIs, Infosecinstitute.com, Tripwire.com, and VentureBeat.
More from Iam WaqasRelated Posts

19 Best Vulnerability Management Software or Tools in 2024
KEY TAKEAWAYS Vulnerability management tools scan and detect weaknesses within the network that hac...

How to Detect, Identify and Fix Packet Loss with Best Tools
KEY TAKEAWAYS Packet loss reduces the speed and amount of data that flows through the network. This ...

15 Best Network Security Software – Top Pick Of Organizations
KEY TAKEAWAYS Network security software keeps the data secure and blocks malicious or potentially vu...

15 Best Virtual Machine Software for Windows in 2024
KEY TAKEAWAYS Virtual machine software is a vital tool for developers to deploy VM software to test ...

What is Software Deployment: Risks and Best Practices
KEY TAKEAWAYS Software deployment is facing various security risks amidst the advancements in the in...

Building Encryption into the Network Fabric with SASE
A network fabric is a mesh of connections between network devices such as access points, switches, a...





