Torrenting is considered illegal in some countries and that’s why most torrenters use anonimity tools like a proxy or VPN to mask their IP addresses. However, sometimes due to connection problems these tools can leak your IP. Therefore, it’s important to perform a Torrent IP leak test by visiting a tool site like “Torrentprivacy.com“.
Here’s how to do it
- Open the tool site
- Connect your VPN or proxy
- Download a torrent file
- Run on client
- Verify torrent IP
Note: We recommend using NordVPN for torrenting as the VPN service guarantees DNS/IP leak protection and offers P2P-optimized servers to torrent safely.
Torrenting continually exposes your IP address to other torrent downloaders and the Internet Providers or governmental agencies who could be tracking you. That’s why most torrent users use anonymity tools to mask their identity.
However, conformity for anonymous torrents can only be attained if one regularly checks torrent IPs while connected to one’s proxy or VPN.
There are many tools for performing torrent leak tests, which we will discuss here in this article.
What is an IP address?
Knowing what an IP is is necessary to get the right idea of torrent IP leaks. The IP address is a unique set of numbers different for every device.
IP address shows the location of a person/device similar to the rental address. In other words, it is the internet address of every device you use.
The IP address is visible, and your activities, such as websites you visit, when you visit those sites, and how much time you spend there, are all visible to your ISP.
You can check your IP address with any IP testing tool.
Why do you need to perform a torrent leak test?
Torrenting sometimes causes some serious issues. It could be malware injection, IP monitoring from ISP, or other DMCA notices. However, expert torrents use private trackers with the best compatible VPN service behind torrenting to secure their identity and IP.
Hiding your IP and using VPN encryption secures all the downloading processes with the best speed, avoids such threats, and increases the speed by bypassing ISP throttling issues.
Most VPN providers don’t allow torrenting or have enough privacy features to protect your identity and reveal your IP address. So! It’s essential to check your torrent IP while connecting through VPN or slipt tunneling.
How to test torrent IP leak
It is worth checking torrent IP addresses if you use IP masking tools like VPN or proxy.
Here’s how to check torrent IPs with specially designed tools. First of all, you need to select any tool among all these;
- IPMagnet
- upcoil.com
- torrentprivacy.com
All these tools work more or less the same, so it doesn’t matter which one you select. Ensure your chosen tool is unbiased and does not involve any VPN provider.
5 steps to check your torrent IP
Time needed: 5 minutes
Steps to check your torrenting IP address
- Open Tool Site
Head on to the selected free tool website (we are using checkmyip.torrentprivacy.com as an example). Here you will see your actual IP address.
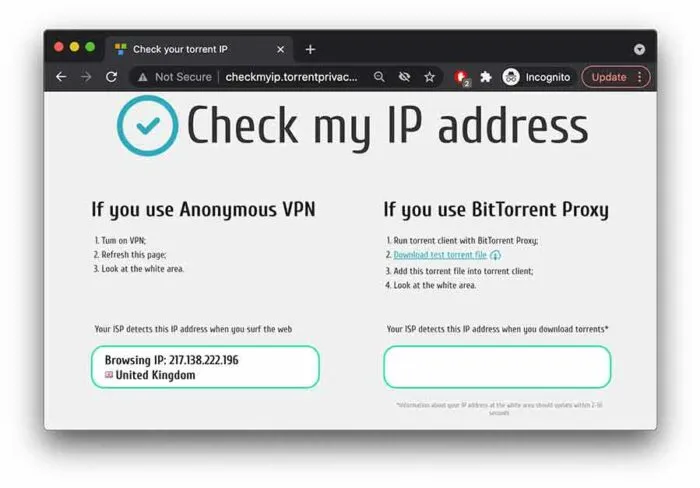
- Connect Your VPN Before
Now connect your VPN and refresh the page. This step will display your VPN IP in the ‘anonymous VPN’ section. (Remember that this IP should be different from your real IP)
- Download Torrent File
Click the ‘download test torrent file’.
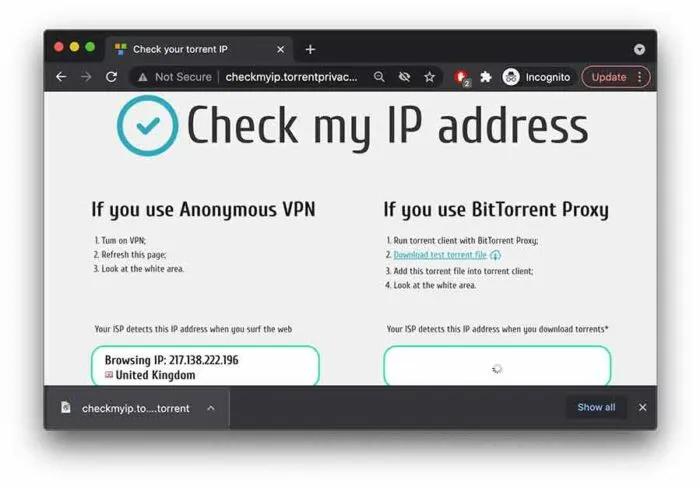
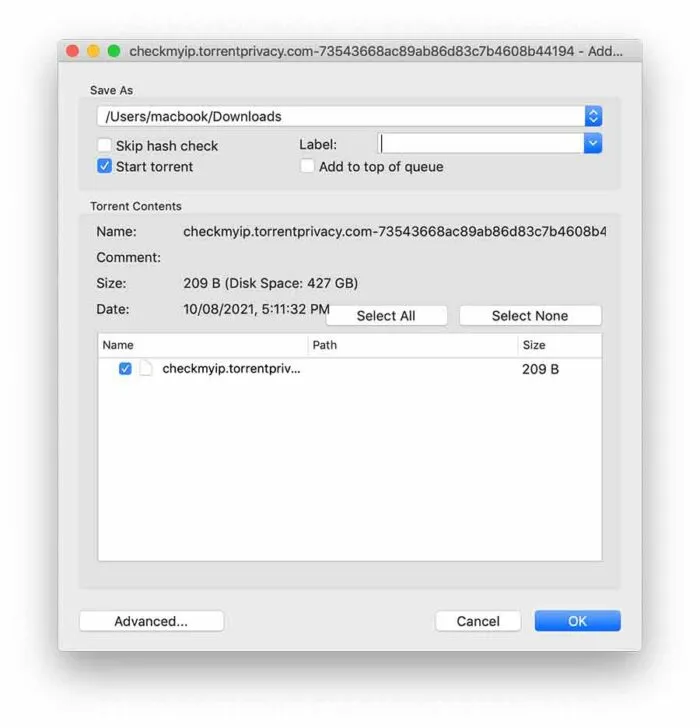
- Run On Client
Run the downloaded link through your torrent client.
- Check torrent IP
Now verify that the displayed IP address is in the field ‘BitTorrent Proxy.’ If it is your VPN IP, then your torrent IP is not leaking.
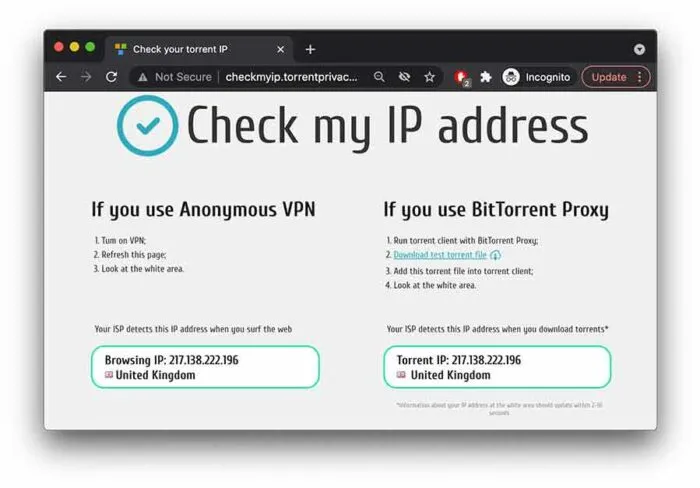
That’s all you have to do if you want to check your torrent IP and whether your VPN leaks it. It is highly recommended that you check your VPN for torrenting through a DNS leak test.
What are HTML5 geolocation leaks?
The advancement of HTML5 has made it possible for web applications to get users’ locations. Genuine HTML5 geolocation first requests users’ permission to get their location details, but HTML5 geolocation leaks allow websites to collect location data without user consent.
Developers only need to run a script on the client or server side to obtain your geographical location. While this technology can be used for legitimate purposes, it can also be misused to collect users’ location information without their knowledge.
For instance, a website may use a user’s location information to send customized ads based on their location. Similarly, other web apps may track users’ movement and predict their location at different times. This invasive practice can provide crucial information to malicious actors who exploit unsuspecting victims. Ensure your browser is up-to-date to protect yourself from HTML5 geolocation leaks.
Additionally, disable any unnecessary location-tracking features and be cautious with the permissions you give to web applications. In addition, subscribe to a quality VPN service that can help you spoof your location and browse privately.
How to change your IP address
Without any precaution, torrent downloading could easily be traced back to you as torrenting publically displays the user’s IP address to every peer in a file swarm.
Also, due to many privacy and security risks, internet users use IP masking tools to change IP addresses. However, torrenting is one of the most surveilled and threatened internet activities; most torrent downloaders use anonymous way-outs to change their IP address to a fake one.
IP masking tools such as a proxy, Tor browser, and VPN software place an anonymous server between your device and internet sites through which you are given a fake IP address. When such tools are connected, it ensures that your URL request does not pass through the ISP server; otherwise, everything will be revealed.
What is a Tor exit node?
Tor nodes are typical servers hosted by volunteers in the Tor network to route user traffic. Traffic from your device bounces through at least three nodes (entry, middle, and exit) before it gets out of the Tor network to the regular internet. The exit node is the last before your traffic exits the Tor network. The last encryption layer peels off at the exit node, exposing your data.
Therefore, exit node operators have a chance to dig deeper into your request, which can compromise your privacy. However, it is implausible, so Tor is the most popular anonymity tool. The exit node also changes your IP address, giving you another anonymity layer so no one can associate the IP address with your internet activities.
DNS leak could leak your torrent IP
DNS is the domain name system that enables communication between your device and the internet system.
It changes the wordy URL into numerical form so that the browser understands it and shows the desired result for the request sent from a device. You could visit this page about the DNS Leak Test for a more detailed DNS explanation.
Mostly, the DNS server is set to the ISP DNS server; therefore, they can also see the IP address of the device from which the DNS request is coming. However, using a VPN or proxy places an anonymous DNS server so every request passes through it. In this way, the IP address remains masked. However, sometimes, the DNS requests leak to the ISP server, exposing the user’s real IP.
Why is a VPN the best way to hide your torrent IP?
A VPN reroutes your connection through a remote server and assigns you a new IP address to mask your identity. The new IP address will appear on every website you visit on the internet. Generally, VPNs assign you shared IP addresses to ensure nobody can associate the IP address with your device.
Furthermore, the VPN encrypts your traffic, rendering your data unreadable to third parties. When torrenting, the privacy provided by a VPN prevents even your own ISP from knowing the websites you visit and what you are browsing at any given time. This way, you can torrent at full connection speeds because the ISP cannot throttle your speed. Also, you can avoid surveillance from copyright owners and ISP.
Best VPN for hiding your torrent IP address
1. NordVPN
- Automatic kill switch
- Split tunneling
- Dedicated IP
- Next-generation encryption
- Onion over VPN
- SOCKS5 proxy
- Dark web monitoring
- Threat protection
- Meshnet
- Browser proxy extensions
- Dedicated P2P servers
NordVPN is a comprehensive privacy tool with a reputation for robust security, high speeds, and impressive unblocking abilities over the years. The VPN is headquartered in Panama, a privacy-friendly jurisdiction where government agencies don’t interfere.
Thankfully, all applications are easy to use, with an intuitive interface and unique privacy features. In addition, it is compatible with all major operating systems and allows you to protect up to 10 devices simultaneously. Moreover, you can test the service risk-free with the 30-day money-back guarantee.
Besides all its unique features, the VPN enforces a strict no-logs policy, ensuring your online activities cannot be traced back to you. Furthermore, it protects DNS, IP, and WebRTC leaks to safeguard your real identity in the torrenting swarm.
NordVPN’s connection speeds are fast and consistent, thanks to its proprietary NordLynx, based on the WireGuard tunneling protocol. The fast speeds and the SmartPlay feature allow you to bypass all geographic restrictions and unblock websites seamlessly.
It secures your data in the connection tunnel using AES-256 encryption. The VPN also offers an automatic kill, ensuring data does not leak accidentally when the disconnection drops. In addition, it has a double VPN feature that preserves the integrity of your connection and data even when one server is compromised.
2. ExpressVPN
- 3000+ servers in 105+ countries
- AES-256 encryption
- 30 days money back guarantee
- Effective split tunneling
- Supports P2P connections
- DNS/IPv6 leak protection
- Lightway protocol
- Trusted server technology
- Tor over VPN
- Threat manager
ExpressVPN is the best privacy tool for hiding your IP address. The VPN has over 3,000 servers in 105 countries and has headquarters in the British Virgin Islands, a privacy-friendly country. So, you don’t need to worry about the government interfering with your connections.
It has applications for various devices and operating systems, including iOS, Android, Linux, Mac, and Windows. However, you can only connect up to eight simultaneous devices simultaneously. Moreover, it has its own Aircove router with preinstalled ExpressVPN software.
The VPN has a Smart location feature that automatically connects you to the fastest server. Besides, it supports OpenVPN, IKEv2, and its proprietary Lightway protocol, providing fast speed, robust security, less power consumption, and sustainable connectivity.
Its security features are formidable, like the military-grade AES 256-bit encryption that protects traffic when torrenting. Also, it has an excellent automatic kill switch called ‘Network Lock,’ which disconnects your device from the internet when your VPN connection drops. This prevents your actual IP address from leaking, a great torrenting feature.
Additionally, it enforces a strict no-logs policy and protects you against IP, DNS, and WebRTC leaks to preserve your privacy. The VPN’s extensive network and unique features make it easy to bypass censorship and unblock websites. Unfortunately, it is expensive but has a 30-day money-back guarantee, so you can test it risk-free.
3. Private Internet Access (PIA)
- Split tunneling feature
- Fully supports P2P
- No-logs policy
- Automatic kill switch
- Unlimited simultaneous connections
- 30-day money-back guarantee
Private Internet Access (PIA) is a classic VPN that is highly rated in the privacy industry because of its customizable security features and applications. For example, it has the largest server network and over 10,000 dedicated IPs in different countries to mask your identity.
The massive server network ensures you can access many servers near your location to boost connection speeds. This is also ideal when you want to bypass geographic restrictions and censorship or unblock websites in your network.
Recently, PIA scrapped the limit on the number of simultaneous connections, allowing you to connect unlimited devices. In addition, it supports all major devices and operating systems, so you can protect many devices using one account.
Security-wise, PIA protects your torrenting traffic using the unbreakable AES-256 encryption protocol. It also has an effective automatic kill switch that prevents your device from making unsecured connections in case of VPN failure.
PIA also uses the reliable WireGuard transmission protocol to ensure fast and reliable connection speeds, which improves your torrenting experience. Fast connection speeds are vital, especially when unblocking streaming platforms or downloading torrent files.
Regarding privacy, the VPN enforces a strict no-logs policy to cover your tracks and ensure no one can access your browsing records. Furthermore, it has a DNS/IPv6 leak protection feature that prevents sensitive information, such as your IP address, from leaking. Moreover, you can use the VPN’s 30-day money-back guarantee to test it risk-free.
4. Surfshark
- GPS spoof
- Clean Web
- No borders
- Camouflage mode
- Multihop
- Device invisibility
- Two-factor authentication
- Bypasser
- Perfect forward secrecy
- Auto Connect
- Tor over VPN
Surfshark is another low-budget VPN with dependable privacy and security features to hide your IP address. It also has super-fast connection speeds and powerful unblocking abilities to help you bypass geo-restrictions and unblock all popular streaming platforms, including Netflix and Amazon Prime.
The VPN takes data security seriously, encrypting it using the AES-256-bit algorithm and a kill switch to prevent unsecured connections in case your VPN malfunctions. It also has a CleanWeb feature that blocks trackers, malware, and ads to improve your torrenting experience.
Surfshark has two features dedicated to people living in regions with high surveillance: a no-border mode that detects heavily censored regions and allocates you special servers and a camouflage mode that hides your VPN activities. Furthermore, the VPN keeps no logs and has a DNS/IP leak protection feature to protect your identity.
It also has applications for various devices, including Windows, Mac, Android, iOS, and TVs. Surfshark supports unlimited simultaneous devices, meaning you can protect various devices using one account. In addition, it has a 30-day money-back guarantee, allowing you to test it without any financial burden.
Will torrenting get me into trouble?
The underlying technology of torrenting is legal. The only thing that can get you in trouble is downloading and uploading copyrighted files. If you are sharing files freely available in the public domain or whose copyright has expired, you are okay, and nobody can come after you.
Additionally, nowadays, most copyright holders go after the users who upload copyrighted content rather than those who download it. Subscribe to a premium VPN like NordVPN and torrent privately to avoid any possible trouble.
FAQs
Share this article
About the Author
Rebecca James is an IT consultant with forward thinking approach toward developing IT infrastructures of SMEs. She writes to engage with individuals and raise awareness of digital security, privacy, and better IT infrastructure.
More from Rebecca JamesRelated Posts

Torrent Privacy Risks: How to Torrent Safely and Anonymously?
KEY TAKEAWAYS Anything related to the internet comes with cybersecurity risks. Torrenting is one of ...

21 Best Torrent Search Engines in 2024 (100% Working)
KEY TAKEAWAYS The best Torrent search engines work to provide reliable torrent links. However, torre...

12 Best Torrent9 Alternatives in 2024
KEY TAKEAWAYS Torrenting with your original IP address can cost low-speed Internet speed, called ISP...
10 Best Torrent Apps for Android in 2024 (100% Working)
KEY TAKEAWAYS If you’re looking to find out the torrent apps for your smartphone, then have a ...

20 Best ExtraTorrent Alternatives For Torrenting in 2024
KEY TAKEAWAYS Finding a reliable ExtraTorrent alternative might be challenging for most users. There...

20 Best Kickass Torrents Alternatives in 2024
KEY TAKEAWAYS After thorough testing and research, these are the top 20 best Kickass Torrent alterna...