Tor does provide some level of protection, but it will never provide enough data encryption and privacy to secure your entire connection. Here are quick steps you can take to use Tor safely.
- Install Tor privately – It’s important to install and set up Tor properly before use.
- Enable Tor VPN – Before getting into Tor browser, you need to enable the most secure VPN.
- Use bridges – You can connect to a bridge to get around these restrictions.
- Install anti-malware – The Onion browser lets you access various malicious sites unknowingly. Therefore, use an antivirus to stay safe.
- Avoid torrenting – If you use Tor for downloading torrent files, you are compromising your anonymity.
- Use private search engines – Private search engines make your searches anonymous and doesn’t record your activity.
- Practice safe browsing – You must follow some safe browsing tips to enhance security.
The Tor network was designed and developed to provide anonymous connections without trackbacks. Law enforcement agencies and other spies used Tor to communicate. Since it is open source, used by thousands of users, and handled by unknown volunteers, it has become more vulnerable. So, it’s necessary to use Tor safely and anonymously.
Even though the Onion browser provides more robust security and privacy features than any other browser, privacy loopholes must be patched. Our guide covers multiple ways to use this privacy browser safely. Read on to find out.
How does the Tor browser work?
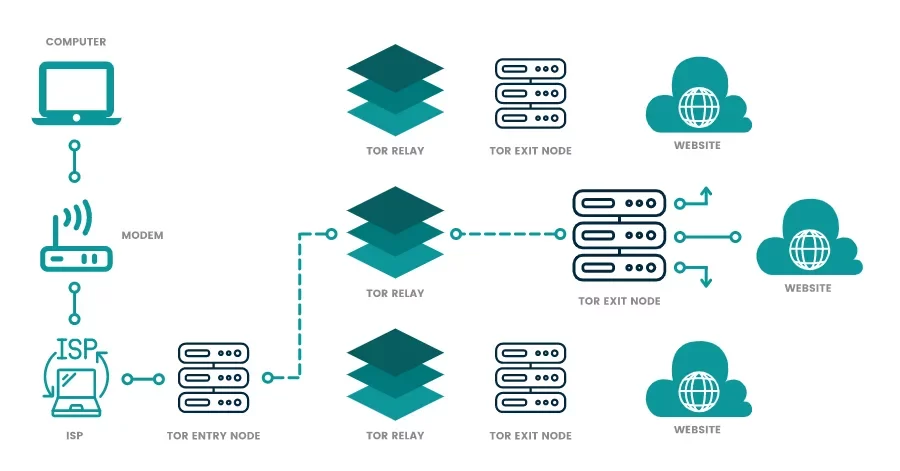
Tor, instead of encrypting all data traffic, provides layered encryption. It routes the data through multiple nodes and goes unencrypted when it leaves the exit node. This makes your data vulnerable to both spying and hacking. Your ISP can also throttle and monitor your connection using the Tor browser.
Nonetheless, despite all the flaws and vulnerabilities, the Onion browser is somewhat safe to use if you practice specific tips to enhance your security on the Tor browser.
Who uses the Tor browser?
The purpose behind developing the Tor browser was to gain anonymity while surfing the web. People who hide or want to benefit from online anonymity use the Tor browser. Besides this, the Tor browser is used in the following situations:
- People who want to keep their activities confidential from ISPs, such as journalists or political activists. It routes the traffic in multiple layers, so it isn’t easy to trace back to the original user. Thus, you can surf the web without leaving any digital footprints.
- Users who want to circumvent censorship, like people in China or Iran, benefit from Tor. Tor provides anonymity by hiding your IP address and bypassing firewalls to access the open web.
- Tor browser also serves as a gateway to the dark and the deep web.
- Law enforcement agencies who want to trace criminals use the Tor browser to gather their previous criminal records.
- People who are concerned about cyber spying. Tor’s onion routing method obscures your private details as the data passes through the open network. Thus making it difficult for anyone to spy on your IP address.
Risks associated with the Onion browser
Some issues and risks are associated with the Tor browser, and it is crucial to know about them to assess your vulnerability.
The following mentioned below are some of the issues with using the Tor browser:
- Tor is vulnerable to exit nodes and malware attacks, so it doesn’t guarantee complete protection.
- Some network administrators have blocked access to the Tor browser.
- Tor browser only provides layered encryption instead of encrypting the entire data. This means that encryption is only within the layers. Your data remains vulnerable and unprotected as it leaves Tor’s exit nodes to its destination.
- Using the Onion browser results in slow and sluggish connection speed. The traffic routes through several nodes, increasing loading time and decreasing speed.
- Your ISP can’t see your activity, but they can see that you’re using the Tor browser. As a result, they start throttling your connection and can even target you for surveillance.
- The exit nodes can log the contents of the request you made. They can modify the nodes or inject them with malware.
All these points signify that Tor is not safe to use. However, practicing some protective measures or using a reliable VPN can reduce the dangers and enhance online privacy while using the Tor browser.
Note: Not all VPNs do support Tor over VPN. Double encryption could be a nightmare if we talk about “Internet speed.” Your browsing experience will be slower than you ever imagined. A Compatible VPN with the Tor browser will solve both issues; your ISP can’t see if you are using the Onion browser, and your browsing speed will be improved.
7 Tips to use Tor browser safely

Here are some pro tips based on our research to avoid mishaps while browsing.
1. Installing Tor safely
As per the working mechanism, Tor establishes the connection first with the ISP. This way, your ISP monitors and throttles your connection.
Furthermore, they put your IP address in suspicious profile records. In other words, your ISP knows when you use the Tor network.
Before installing and using the Tor browser, a VPN is crucial for safe and secure access.
- Install VPN first. We recommend using NordVPN with the Onion browser.
- Then, click Here to download The Tor.
- Run the file to set up the Tor BROWSER.
- Select a destination folder.
- Click on “Install” and download the Tor browser.
- Once completed, open the Tor browser and “set up” the circuit.
2. Always enable a VPN
A compatible VPN is the best way to enhance your security on the Tor browser. A VPN encrypts all your traffic and replaces your IP address with a temporary one. This way, your ISP can’t detect which websites you’re visiting. They can only view the encrypted traffic from the VPN but can’t intercept it.
There are two ways to use a VPN to boost your security on the Tor browser:
- Tor over VPN: The easiest way to connect to the Tor browser guarantees complete online protection. First, connect to the VPN and then route your traffic to the web via Tor. Your data becomes encrypted before routing, maximizing your online privacy and security. However, it doesn’t protect you against malicious nodes.
- VPN Over Tor: It is a bit complicated to connect to the Tor browser and then manually configure the VPN. Although it protects against malicious nodes, it isn’t recommended because of its connection complexity.
It is better to use Tor over VPN instead of VPN over Tor. Ensure you choose a reliable VPN provider like NordVPN that works efficiently with the Tor browser to enhance your online privacy.
3. Use bridges
Network administrators ban the Tor traffic by blocking the entry nodes through their systems. You can connect to a bridge to get around these restrictions. They look like regular traffic and don’t reveal your connection to the Tor browser. Also, there is no complete list of bridges, so even if the ISP filters the connection to know the Tor relays, they can’t block them.
This method adds an extra layer of anonymity and prevents users from getting caught while connected to the Tor browser. There are no significant drawbacks to using Tor bridges. However, for better results and protection, it is suggested that you connect to a VPN first.
4. Use an antivirus software
The dark web is a hub for illicit activities. If you use it for some legitimate purpose, hackers can trick you into downloading malware or spyware that can compromise your Privacy and even harm your other files. When you use the Tor browser to access the dark web, there are higher chances of becoming a target of malware or spyware.
To prevent this from happening, run the best antivirus software. It scans and removes malware or viruses on your device, boosting your security levels.
5. Refrain from torrenting
Tor Browser is not built for P2P file-sharing. The Tor exit nodes block the file-sharing traffic, and if you still download torrents, be prepared for slow speed. If you use Tor to download, you compromise your anonymity.
Also, the BitTorrent client’s insecure design exposes your IP address to trackers and threatens your online anonymity.
6. Use private search engines
Popular search engines like Google or Microsoft Edgework work as data collection tools. They collect and share your sensitive information, such as search queries and website visits. Thus, you should use the private search engine on Tor.
Private search engines make your searches anonymous, hide your IP address, and prevent trackers and adware from spoiling your browsing experience. They are not the best, but they are way better than Google.
7. Practice safe browsing tips
You must follow some safe browsing tips that enhance your security when using the Tor browser. These tips include:
- Always check the URL of the browsing websites. Ensure that you use encrypted HTTPS websites instead of HTTP.
- Delete your cookies, local data, and temporary files that might contain some malicious codes.
- Configure your Tor browser settings and set your security level.
- Ensure that you’re always connected to a VPN that is compatible with Tor.
- Avoid using any suspicious social networking sites like Facebook or Twitter.
- Use a virtual identity that doesn’t include matching information from your real-world identity.
- Disable Flash and JavaScript because websites can track you from browsing activities without providing protection using the Tor browser.
- Update your system regularly.
Other tips for using Tor safely
While Tor is designed to provide privacy, it is not without vulnerabilities. To ensure maximum security while using the browser, we recommend following these precautions:
- Download Tor only from its official site. Hackers have been known to create fake Tor mirror sites that can infect your device with malware if downloaded accidentally. It is advisable never to obtain Tor from a third-party website.
- Utilize a security-focused operating system (OS). TAILS is an example of such an OS, and we suggest running it from a removable drive. By doing so, hackers will find it challenging to identify your computer on the Tor network. Other private OS options include Qube, Whonix, and ZeusGuard.
- Verify every Onion URL before using it. The dark web contains realistic clone sites that pose significant cyber threats. Avoid using URLs you obtain from social media or forums. A reliable dark web search engine can assist you in finding genuine sites. Consider storing trusted sites in an encrypted notebook, such as Turtl.
- Keep your browser up to date. Running the most recent browser versions helps prevent bugs and vulnerabilities that could compromise your privacy and security.
- Disable location tracking. Turning off any location-tracking functionality on your device helps conceal your identity.
- Avoid using plug-ins. Browser extensions and add-ons can result in tracking through browser fingerprinting. Tor automatically blocks specific plug-ins, such as Flash. In the past, such plug-ins have been compromised to expose users’ real IP addresses.
- Refrain from changing the size of your Tor window. Modifying the window size can make it easier for cybercriminals to track you via browser fingerprinting.
- Cover your camera and microphone. This precaution prevents cybercriminals from collecting recordings if they gain control of your device. Although it may seem excessive, hacking into cameras is alarmingly simple.
- Exercise caution when opening files. Avoid accepting suspicious requests or clicking pop-ups. Also, refrain from downloading suspicious files from the dark web. Even if so, ensure you disconnect from the internet before opening it. This will prevent your actual IP address from being exposed.
- Use cryptocurrency for transactions. Cryptocurrencies provide extra anonymity and security when purchasing on the dark web.
How to install the Tor browser on your devices
We recommend installing the Tor browser from its official site to avoid security risks. Although Tor is unavailable on iOS, you can use the Open-source Onion browser as an alternative. Tor powers the browser and can be found on the App Store.
Installing the Onion browser on Windows and Mac
You can install Tor on your Mac or Windows device using these steps:
- Download Tor: Visit the official Tor download page and choose the appropriate installer for your Windows or Mac operating system.
- Open the installation file: Once the download is complete, locate the file and open it. Choose your language preference and follow the installation wizard’s instructions.
- Complete the installation: The wizard will help you if you use Windows. If you use a Mac, the wizard will prompt you to drag the Tor icon into the Applications folder.
- Configure Tor: If using a restricted connection, click the ‘Configure’ button. Follow the prompts to configure Tor depending on whether you’re on a proxy connection or Tor is censored in your location.
Installing Tor browser on Android
Use these steps to download and install the Tor browser on your Android device:
- Visit Tor’s official website: Go to Tor’s official site. Navigate to the Downloads page and click on ‘Download for Android.’
- Follow the installation prompts: Click on ‘Go to Google Play’ and then ‘Install’ to initiate the app download on your device.
- Connect to Tor: Once the installation is complete, you can start browsing securely using Tor on your Android device.
Installing Tor browser on Linux
The following steps will help you install the Tor browser on Linux:
- Download the Tor launcher: Visit the Tor download page on FlatHub and download the Linux launcher file.
- Install the launcher file: Locate the downloaded file, usually saved in the Downloads folder. Open the file to begin the installation process.
- Connect or configure Tor: Click on ‘Launch’ to start Tor. Choose ‘Connect’ to immediately begin browsing or ‘Configure’ if browsing from a network that blocks Tor. If you select ‘Configure,’ you’ll be prompted to set up Tor for a censored location or configure it with a pluggable transport or proxy.
Tor is less safe on some mobile devices
The Tor browser is available as an Android application. If you are careful, using Tor on Android is just as safe as using it on a desktop. Although the alpha release can be easily downloaded and used, it carries the same risks as the desktop browser.
While iOS lacks an official Tor application, you can use the Onion Browser app to visit the Tor network on iOS if absolutely necessary. This app was developed by Mike Tigas, a lead developer for the Tor Browser, and is considered open-source.
However, it’s important to note that even when exercising caution, using Tor on an iOS gadget is not as secure as using it on other devices. The app does not allow complete disabling of JavaScript, compromising privacy as JavaScript can potentially share private data and store cookies in the browser.
So, if you want to use Tor on a smartphone, we recommend an Android device.
When should I not use Tor?
Accessing the dark web has certain limitations, and there are specific activities you should avoid while using Tor:
- Torrenting or streaming content poses challenges on Tor. Many torrenting sites restrict access through Tor exit nodes, rendering peer-to-peer transfers impossible. Even if you configure your torrent client to work with the browser, its slow speeds make it less than ideal for downloading and seeding. Similarly, the browser’s speed is typically insufficient for smooth streaming.
- Logging into personal accounts while on Tor carries risks. By logging into a private account through Tor, you expose yourself to the potential disclosure of your identity. Furthermore, some websites consider The Onion Router usage suspicious and may lock your account. It is advisable to acquire an encrypted email address exclusively for use with the Tor Browser, such as one provided by ProtonMail.
- Using traceable financial information for payments on the Tor browser. Although the browser can help protect your identity and location, it cannot prevent fraud or other financial crimes. Utilizing identifiable payment details within the browser increases the likelihood of exposing sensitive information to malicious individuals. Additionally, certain websites block Tor traffic from accessing their payment pages, potentially preventing you from completing your transaction.
Can I use Tor without a VPN?
Due to its association with the dark web, government authorities actively prevent criminal activities on the Tor network. Regular use of Tor can, therefore, attract government surveillance.
Usually, your Internet Service Provider (ISP) can detect your connection to the Tor network if you aren’t using a VPN. This increases the chances of government authorities monitoring your online activities and targeting you for de-anonymization.
Without a VPN, Tor’s guard node can reveal your public IP address, exposing personal details such as your ISP and location. However, even with a Virtual Private Network connection, you still face certain risks and vulnerabilities inherent to the Tor network. Nevertheless, a VPN can provide an additional layer of protection.
Best VPNs for Tor
1. NordVPN
- Dedicated P2P servers
- Fast and secure downloading
- Automatic kill switch
- Split tunneling
- AES-256-bit encryption
- A strict no-log policy
- Dedicated IP address add-on
- 24/7 live support
NordVPN emerges as a top-notch VPN service. Its reputation is impressive, thanks to an expansive server network comprising over 6,200 servers across 111 countries. Fortunately, it also offers dedicated P2P servers explicitly designed for downloading and sharing P2P files.
These specialized servers can be found in America, Australia, Canada, France, Germany, and the UK.
NordVPN leverages advanced protocols like NordLynx, based on the WireGuard VPN protocol, accompanied by a double NAT setup that results in accelerated download speeds. To further enhance the dark web experience, the VPN features split tunneling, which enables you to route your traffic outside the VPN tunnel.
Regarding security, NordVPN takes robust measures to protect your torrent traffic. It will safeguard your data with AES-256-bit encryption, a kill switch, a double VPN, etc. Importantly, NordVPN adheres to a strict no-log policy, ensuring that no records of your activities are retained, thereby protecting your privacy. Also, its servers run on diskless RAM, meaning no data is stored locally, enabling you to browse anonymously.
2. ExpressVPN
- Network kill switch
- Leak protection
- AES 256-bit encryption
- Threat manager blocker
- Supports Mac, iOS, Android, Windows
- Supports up to 5 simultaneous device connections
- Automatic obfuscation
- No logs policy
- 24/7 live chat
ExpressVPN provides its own ‘onion’ site to ensure secure downloads. By signing up and installing the VPN app, you gain privacy protection right from the start. This is particularly beneficial if you reside in a country that restricts VPN usage or enforces strict censorship.
Operating from the British Virgin Islands, the VPN is located outside the jurisdiction of data-sharing alliances such as the 5, 9, and 14 Eyes. This means that the company is not obligated to hand over your data to governmental agencies, which is helpful when using the Tor network.
With ExpressVPN, you can simply access Tor Browser and your preferred dark websites by creating Tor shortcuts directly on your app’s home screen. This convenience proves particularly valuable considering the often intricate nature of Onion URLs.
Furthermore, you can simultaneously protect your Tor activity on one device while engaging in activities like streaming, gaming, or torrenting on up to five other devices. ExpressVPN incorporates automatic obfuscation to overcome VPN blocks, such as Deep Packet Inspection (DPI). This feature automatically disguises VPN traffic as a regular connection when faced with tough firewalls or in countries with strict censorship.
Additionally, ExpressVPN offers frequent discounts and a 30-day money-back guarantee. If you are not satisfied, obtaining a refund is a simple process. We tried requesting a refund through their 24/7 live chat, and within 2 days, the money was back in our account.
3. Private Internet Access (PIA)
- 256-bit AES encryption
- IP/DNS Leak protection
- MACE ad/malware/tracker blocker
- Unlimited device connections
- No logs policy
- Automatic network kill switch
- Compatible with Windows, routers, macOS, Android, Linux, and iOS.
Private Internet Access (PIA) incorporates a comprehensive ad/tracker/malware blocker within its system. This feature alerts you to potential malicious links that could infect your device and effectively blocks bothersome pop-ups. Additionally, it demonstrates excellent effectiveness in ad-blocking on regular websites.
When it comes to Tor security, PIA offers a multitude of customization options. You have the flexibility to select between the OpenVPN and WireGuard protocols and choose your preferred encryption level (128-bit or 256-bit AES encryption). This allows you to strike the perfect balance between security and speed.
Furthermore, it provides two kill switch options, which prevent data leaks even when the VPN is turned off. Unlike many other VPNs, PIA supports unlimited connections on a single account. This means that while you browse Tor, other individuals in your household can also utilize the VPN.
With an expansive server network of 35,000 servers spanning 90 countries, it offers an extensive range of options for finding a fast and nearby connection for your Tor browsing needs. Despite being based in the US, it operates under a verified no-logs policy, which has been tested and verified in court. Even when government agencies made multiple demands for user data, PIA had no information to hand over.
4. ExtremeVPN
- Unlimited bandwidth
- Up to 10 devices support with a single account
- 256-bit military-grade encryption
- No logs policy
- Supports Windows, Android TV, Xbox, Apple, Chrome, PlayStation
- Internet kill switch
- 24/7 customer support
ExtremeVPN stands out as a highly secure VPN by offering a range of exceptional security features. Our assessment found its reliability outstanding across various aspects of its functionality. Notably, the encryption protocol left a strong impression on us.
The provider uses AES 256-bit encryption, a level of security that government agencies and the military commonly employ. When venturing into the depths of the dark web using the Tor browser, it is crucial to have a VPN that shields your identity from the prying eyes of the outside world.
Additionally, the no-logs policy adds an extra layer of protection by ensuring that your activity logs are neither collected nor stored by their servers. It offers port forwarding support and a vast server network to enhance overall security while navigating the dark web.
These functionalities are designed to fortify the VPN’s security, making them invaluable tools when delving into the dark web. Furthermore, there is no need to worry much about the number of devices, as you connect up to 10 simultaneous connections.
5. Surfshark
- Optimized servers for P2P usage
- AES-256-bit encryption
- Camouflage mode
- No logs policy
- Unlimited bandwidth
- Automatic network kill switch
- MultiHop mode
- Unlimited simultaneous connections
- 24/7 customer support
If you frequently use Tor, Surfshark is one of your best VPN options. The provider offers an extensive network of 3200+ servers spread across 100 countries, which is useful when browsing geo-restricted regions. Additionally, Surfshark supports P2P connections which ehances your privacy and security.
Surfshark’s commitment to privacy and security is topped by its strict no-logs policy. The VPN is based on a safe jurisdiction making it a highly trusted provider for Tor browsing. It operates in the British Virgin Islands, where internet usage is not highly censored compared to other regions such as China.
Moreover, you’re confident that your data is in safe hands with AES 256-bit encryption. Therefore, the encryption protocol is robust and has been embraced by government agencies and the military.
You can also take advantage of the 30-day money-back guarantee. It allows you to request a refund within the first month if you are unsatisfied with its services.
How to access the Dark Web on the Tor Browser
The Dark Web is the unindexed internet used for criminal activities. It is a private network where users’ IP addresses remain hidden, making it a secure network to carry out confidential business activities and commit illegal actions.
However, in addition to potential illegal uses, the dark web can also be used for several legitimate reasons. For instance, if you are a journalist or a whistleblower, you may want to share confidential information by keeping your identity hidden.
The Onion browser allows access to .onion sites, which is the best way to securely access the dark web. These domains aren’t like regular domain names, and using such a domain makes it impossible for the site or the user to know where the other party belongs. Using a VPN and connecting to the Tor browser is better for maximum privacy and protection.
Can you be de-anonymized on Tor?
There have long been suspicions that the FBI, National Security Agency (NSA), and other government authorities can de-anonymize Tor users. As a result, there have been rumors suggesting that Tor is a trap set by law enforcement to monitor individuals seeking online anonymity.
It’s important to note that the Onion network was initially created and developed by the US Navy and continues to receive substantial funding from the US government. While this fact doesn’t necessarily pose a problem, the ongoing collaboration between Tor developers and the US government, as highlighted in Yasher Levine’s book Surveillance Valley, raises concerns.
Despite Tor’s intended purpose of providing ultimate anonymity, several suspicions of de-anonymization have been reported.
In a 2017 court case, the FBI refused to reveal evidence of a potential Tor vulnerability used to uncover a suspect, ultimately leading to the case’s collapse. This incident shows that while the FBI can de-anonymize users, it cannot disclose its methods.
If a government agency were to disclose a vulnerability openly, Tor users would refrain from using the platform, making it ineffective for surveillance purposes. Additionally, it would be straightforward that the remaining traffic is state-affiliated.
Nevertheless, various email conversations between Tor developers and US intelligence agencies have been leaked in recent years. For instance, there is an instance where a Tor co-founder discusses with the US Department of Justice regarding collaborating with them, including mentioning the inclusion of ‘backdoors’ into the network.
De-anonymizing Tor Users: Research at Columbia University
Columbia University researchers have made advancements in traffic analysis attacks, enabling them to unveil the identities of up to 81% of Tor users by carefully examining router data.
NetFlow, a technology designed explicitly for gathering IP traffic information and monitoring network flow, is embedded within Cisco routing protocols. It facilitates traffic data collection as it enters and exits an interface.
Infiltrators can utilize these valuable insights obtained through NetFlow to conduct traffic analysis attacks, where they closely observe traffic patterns across various points within the Onion network.
By exploiting NetFlow’s capabilities, infiltrators can expose a user’s original IP address, thereby revealing their true identity. These findings further support the idea that Tor users are susceptible to identification and de-anonymization.
Tor’s three layers of encryption and randomized IP address
At its core, Tor serves the purpose of ensuring online activity remains anonymous. It achieves this by employing techniques similar to those used by VPNs, which involve encrypting web traffic and altering the IP address associated with the user.
Unlike a VPN, Tor operates through a decentralized network of servers, offering a randomized connection to users. Consequently, the choice of server location is beyond the user’s control. To enhance security, the browser employs a new set of servers to route your data every ten minutes. This system ensures that each node within the network is aware of only the server.
FAQs
Share this article
About the Author
Waqas is a cybersecurity journalist and writer who has a knack for writing technology and online privacy-focused articles. He strives to help achieve a secure online environment and is skilled in writing topics related to cybersecurity, AI, DevOps, Cloud security, and a lot more. As seen in: Computer.org, Nordic APIs, Infosecinstitute.com, Tripwire.com, and VentureBeat.
More from Iam WaqasRelated Posts

Tor Browser Privacy Setting-How to Setup Properly?
The Tor browser is notorious for providing a secure browsing experience and allowing access to the d...

The 14 Best Temporary Email Services for 2024
KEY TAKEAWAYS If you’re in a hurry to find out the disposable email service provider, have a q...

Is Tor Illegal? Learn What Makes It Legal to Use
KEY TAKEAWAYS Tor is one of the most popular private browsers in the industry. However, most people ...

17 Best Tor Alternatives for Browsing Anonymously
KEY TAKEAWAYS If you are looking for a Tor alternative to achieve better privacy and security, then ...

Who Can See My Browsing History and Activities – Lets Find Out
KEY TAKEAWAYS The following mentioned below are the most prominent sources that can see your browsin...
How Can Google Track You and How To Stop Google Tracking
Browsing the internet without Google tracking has become essential because of growing security conce...