Data Retention Law in United States
Mandatory Data Retention Law in the United States is not implemented. However, according to the law …

How to Change Your Location Online Using Geo-Spoofing?
Most people know about the benefits of location access, like adding locations in their social media …

How to Avoid Gambling Restrictions in 2024
Online gambling users are continuously increasing. Over 155.3 million people enjoy gambling. However…

Torrent Privacy Risks: How to Torrent Safely and Anonymously?
Torrenting was created with the best intentions, but it isn’t flawless. For one, when on a torrent n…

Does ExtremeVPN Work With Netflix? Yes!
ExtremeVPN is relatively new in the market but is quickly gaining popularity for its ultra-fast spee…

ExtremeVPN Review (2025): Fast, Affordable, User-friendly
ExtremeVPN is a modern VPN with some of the most fantastic privacy, security, streaming, and torrent…

Passengers’ Data Stored on User Devices, not on DigiYatra Storage, says India Govt
The Civil Aviation Ministry stated that the Digi Yatra process has no central storage of passengers’…

20 Best Penetration Testing Tools For Security Professionals
Cyber attacks are growing in severity and frequency, and businesses of all sizes are at risk. Statis…

19 Best Vulnerability Management Software or Tools in 2024
Vulnerability Management is a continuous process designed to detect, classify, remediate, and mitiga…

17 Best Password Managers For iPhone and iPad in 2025
iPhones are considered much safer and immune to viruses, but many technical ways can still harm your…

12 Best Encrypted Cloud Backup Services To Consider In 2024
Cloud adoption has increased rapidly during the past few years, but the cloud environment isn’t 100%…
15 Best Data Recovery Software in 2025 – Free & Paid
Data loss has become a severe challenge to business organizations, resulting in many consequences, f…
Tor Browser Privacy Setting – How to Setup Properly?
The Tor browser is notorious for providing a secure browsing experience and allowing access to the d…
15 Best Free Cell Phone Tracker Apps in 2024
Cell phone tracking apps allow you to trace someone’s private activities without consent. By secretl…

How to Detect, Identify and Fix Packet Loss with Best Tools
The most frustrating thing while surfing the web is slow or interrupted connections. If you ever exp…

15 Best Network Security Software – Top Pick Of Organizations
Network security is a set of actionable measures organizations take to prevent accidental damage to …

20 Best Free Websites to Watch Cartoons Online in 2025
Online streaming platforms are expanding daily, covering the world, and are becoming a source of ent…

15 Best Virtual Machine Software for Windows in 2024
A virtual machine is a digital version of a physical computer that can run multiple operating system…

What is Software Deployment: Risks and Best Practices
Software deployment is the process of configuring, updating, and deploying software applications. It…

Building Encryption into the Network Fabric with SASE
A network fabric is a mesh of connections between network devices such as access points, switches, a…

What is Incident Reponse? Best Incident Response Tools
Every organization nowadays uses the Internet. However, when you involve tech in your business, secu…
Synthetic Data: Compliance and Security Risks
As machine learning frameworks such as Tensorflow and PyTorch become easier to use and pre-designed …

14 Best Dark Web Monitoring Tools and Solutions in 2024
The dark web’s anonymity makes it a hub for illegal and nefarious activities. Cybercriminals use the…

6 Best VPN for Amazon Prime Video in 2025 – Fast & Secure
Amazon Prime Video is the second most popular streaming platform in the world. However, it allows li…
5 Best VPN for Binance in 2025
Binance is the world’s largest cryptocurrency trading platform, but its full version isn’t available…

21 Best Torrent Search Engines in 2024 (100% Working)
Finding the best torrent file might be a hassle because torrent sites are open platforms where anyon…

12 Best Torrent9 Alternatives in 2025
Torrent9 is one of the most famous torrenting sites. It was well-known in the torrenting and fi…
LastPass Review: How Safe And Trustworthy It Is To Use In 2025?
LastPass ranks among the best password manager, stuffed with a range of features worth using. It is …
What Is A Dashlane Password Manager? Full Review 2024
Dashlane is a top-tier password manager that provides excellent service. It offers top-notch securit…

Hushmail Review: Does It Provide Enough Security?
Hushmail is a secure email provider that works to keep its users’ data safe. It uses end-to-end encr…

Proton Mail Review: Have We Found Secure Email Provider?
If you are worried about how mainstream email providers like Gmail log your data and access every em…

7 Best Free VPNs for Torrenting in 2025 – [Safe and Tested]
Finding the best free VPN for torrenting might be hard, specifically since there are better choices …

6 Best PrimeWire Alternatives in 2025 [Safe & Secure]
PrimeWire is a popular free online streaming site for watching free movies and TV shows anywhere. Th…
Kaspersky Password Manager Review In 2025
Kaspersky is an established brand offering an advanced security solutions and services portfolio. Mi…
How Safe is Norton Password Manager? Full Review In 2025
Norton password manager is a reliable password manager with the Norton 360 Internet Security Plan. Y…
Does Keeper Password Manager Keep Passwords safe and secure?
Keeper is another established brand that belongs to Keeper Security and has specialized in password …
How safe is 1Password manager? Detailed and Complete Review
1Password is one of the best password managers available. It is an easy-to-use password manager that…
Is Samsung Password manager worth trusting for password security? Review In 2025
Samsung Pass is a built-in password manager part of the Samsung ecosystem software. It saves your we…
How Safe and Secure Is Google Chrome Password Manager In 2025
Most people use Google Chrome password manager, but not everyone is well aware of it. The Google pas…

The Role of Developer Security in Software Development
Developers play a crucial role in ensuring software security. Developer security refers to building …
NordPass Review- Is NordPass Safe To Use? In 2025 Edition
Nord Security, in 2019, released its password manager named ”NordPass”. The team behind NordPass i…
How Secure Is Avast Password Manager – Review In 2025
Avast markets its password manager under the name “Avast Passwords.” The password manager offers a s…
10 Best Alternatives of Tunnelbear (Free and Paid in 2025)
TunnelBear is a popular VPN provider because of its unique free plan, but it has shortcomings. One m…

4 Best Practices When Implementing Cloud Data Security And Protection
Businesses are using the cloud to store data and run daily operations more than ever. There’s much t…
StrongVPN Review: Is It Strong Enough to Use In 2025?
StrongVPN is one of the oldest yet most overlooked VPN service providers, giving the impression that…

PrivadoVPN Review: Is It Fast, Secure, and Private to Use In 2025?
PrivadoVPN is a small yet mighty VPN provider that offers free and premium plans. The paid version p…
Does FastestVPN Provide Fastest VPN Service? Detailed Review
FastestVPN marked its way in the industry in 2016. The VPN claims to have the jam-packed features re…
How TorGuard VPN Really Guards Your Privacy? Detailed Review
TorGuard VPN emerges as a strong product that provides an anonymous VPN, a business VPN, and a priva…
Does Bitdefender VPN Provide Enough Defence? Detailed Review
Bitdefender is a trustworthy brand that offers cybersecurity solutions for homes and businesses, inc…

7 Best Free VPNs for the Dark Web in 2025: Secure & Fast
Using a VPN to access the dark web is crucial due to its numerous privacy and security issues and co…

The 14 Best Temporary Email Services for 2025
Sharing email addresses with websites and services might seem harmless, but it has significant priva…
iTop VPN Review- Offering Free and Paid Versions – Worth Using?
iTop launches tools and software for desktop and mobile devices, and iTop VPN is one of their produc…
BlufVPN Review: Is the new Comer worth the hype?
BlufVPN is a newcomer in the market that seems like a secure and reliable VPN. The VPN started its s…
Ivacy VPN Review – Is This Really Safe and Private?
Ivacy VPN has been offering its services for over a decade. Because of its opaque ownership and susp…
Is malwarebytes VPN living up to its glory?- a detailed Review
With the increasing security threats and risks of cyber attacks, antivirus companies have stepped fo…
Atlas VPN Review: Is This New VPN Good to Use In 2025?
Atlas VPN is a relatively new VPN that started its services in 2019. Its growing success led Nord Se…
6 Best VPNs for Android TV in 2025
Android TV boxes have access to broader entertainment options than basic TVs as they rely on the int…

Is Tor Illegal? Learn What Makes It Legal to Use
Anonymity and privacy on the Internet are becoming more critical than ever. The Tor browser is the m…

CyberGhost Review: Is CyberGhost Good to Use In 2025?
CyberGhost VPN is a fully featured-packed VPN provider and is one of the most preferred users’ choic…

10 Best Torrent Apps for Android in 2025 (100% Working)
Torrenting is not limited to PCs or laptops. You can even use a portable device, preferably your And…

17 Best Tor Alternatives for Anonymous Browsing
Tor is one of the most reliable networks for accessing the deep and dark web. Its vast range of…

20 Best ExtraTorrent Alternatives and Proxy Sites in 2025
ExtraTorrent started its services in 2006 and was among the best torrent sites, offering a vast and …

20 Best Kickass Torrents Alternatives in 2025
Kickass Torrents was one of the famous torrent sites, like the Pirate Bay, until the alleged ow…

6 Best Dark Web VPN in 2025
The dark web is often known for its controversies. Despite offering fantastic benefits like helping …
Who Can See My Browsing History and Activities – Lets Find Out
Many surveillance eyes track and monitor everything you do on the web. The prying eyes learn about y…

6 Best VPNs for Popcorn Time – How to Stream Safely
Popcorn Time is an excellent torrent streaming site that allows you to watch directly instead of dow…
10 Best Secure VPN Providers in 2025
When choosing a VPN provider, security should be your top priority. After all, you’re entrusting you…
11 Best Dark Web News Sites Offering Factual Information
Internet censorship makes it impossible to stay updated about the latest events and access accurate …

12 Best Stream2watch Alternatives in 2025 – [Free and Paid]
Stream2watch is a free streaming platform that lets you watch live and on-demand sports content. How…

How to Use Tor Safely in 2024? 7 Tips for Beginners
The Tor network was designed and developed to provide anonymous connections without trackbacks. Law …

9 Popular Instagram Scams to Know and Avoid in 2024
Online scams take place all over social media, and Instagram’s popularity also has made it an ideal …
How to Change Netflix Region in 2025
Netflix is one of the most popular streaming platforms, accessible in over 190 countries globally. W…

The 17 Best Dark Web Marketplaces in 2025
The dark web marketplace is an online marketplace where you can buy and sell anything. These marketp…
Ways Google Use to Track You – How to Prevent Them
Browsing the internet without Google tracking has become essential because of growing security conce…

How To Detect Hidden Cameras And Listening Devices? A Complete Guide
Many people feel like someone is watching them or listening to their conversations. They may be righ…

How to Speed Up Your uTorrent Downloads
After BitTorrent, uTorrent is the most popular torrent client. Its main charm lies in its lightweigh…

How to Prevent Phishing Attacks in 2024
Phishing remains a significant security concern for most individuals and organizations. A report fin…

Dark Web vs. Deep Web: What’s the Difference?
The internet is much deeper than what you access daily. It comprises approximately five million tera…

The 10 Best VPNs for Torrenting in 2025 – Free and Paid
Torrenting has its benefits, but it can also put you in trouble. When you download torrents, the cop…
Top 13 Mobile Security Threats and How to Prevent Them
Mobile devices have become crucial in our daily lives. From emails to studying online or even stream…
ISP Throtlling: 4 Best Ways to Stop Bandwidth Throttling in 2025
ISP throttling is a widespread activity in which ISPs deliberately slow down internet speed to limit…

10 Best Putlocker Alternatives in 2025 – Free and Safe
Putlocker was one of the best online streaming platforms, specifically since it was free. It has an …
17 Free Streaming Sites to Watch UFC Fights Online in 2025
If you love watching UFC fights live-action, you’d probably look for the best free UFC streaming sit…

18 Free Online Sports Streaming Sites to Watch Sports Live
The essence of watching sports lies in live streaming it. Watching the events unfold with adrenaline…

4 Easy Steps to Access Dark Web on Your Phone Safely in 2024
The dark web has been a source of mystery and caution, and accessing it seems complex. Let…

What is Virtual Firewall and How it Helps Us in 2024?
Scientists and technicians are trying to invent the latest technology protection to create barriers …

10 Ways to Prevent Ransomware Attacks
The scope and tactics of ransomware threats constantly evolve. Their prime objectives are …
How to Encrypt Your Emails on Gmail, Yahoo, Outlook, and G Suite
Encryption is, so far, the best possible way to secure your emails. With encryption, your informatio…

Is qBitTorrent Safe and Legal to Use?
qBitTorrent is one of the oldest and most widely used torrent clients that functions on all major op…

18 Best Torrent Clients for Safe Torrenting in 2025
Choosing a torrent client is crucial for privacy and security; it’s also important in fast downloadi…
How to Encrypt a Flash Drive on Windows, MacOS, and Linux
Flash drives are cheap, convenient, and portable methods of storing important information. But their…

How to Browse Privately in 2024 – 11 Best Tips
It isn’t new that online privacy and security have ceased altogether. On the one hand, cybercriminal…

12 Best Secure Email Providers in 2025
Using any mainstream email provider can risk your digital privacy. One of the best ways to send anon…

7 Best VPNs for Tor Browser in 2025 – Safe and Secure
The Tor browser is a privacy-focused browser that ensures user anonymity. It helps users to bypass i…

10 Best Ad Blockers for 2025 – Free & Paid
Pop-up ads are intrusive, ruin the browsing experience, and increase hardware loads. They are even t…
6 Best VPNs for Netflix in 2025
Netflix has a vast selection of content, with new episodes appearing right after they air on televis…

3 Best Ways to Hide Browsing History from ISP in 2024
ISP tracking is a way for companies to collect data about what their customers are doing online. Thi…

29 Best Flixtor Alternatives to Stream Free Movies in 2025
Are you planning a movie night with friends? The right platform is all you need to stream free movie…

11 Best Peerblock Alternatives for Anonymous Browsing
People are moving from PeerBlocks to its alternative because of its darker side. Firstly, it is now …

16 Best Private Broswers for Secure Browsing in 2024
Most web browsers don’t respect your online privacy, leaving you vulnerable to spying and data leaks…

5 Easy Steps to Perform a Torrent Leak Test in 2024
Torrenting continually exposes your IP address to other torrent downloaders and the Internet Provide…

How to Access the Dark Web Safely: A Step-by-Step Guide
There are several misconceptions about the dark web, as many users use it for illegal activities. Ho…

20 Best Yify or YTS Alternatives and Working Proxy Sites in 2025
The hunt for the best YTS alternatives is not new for torrent downloaders. Since the MPAA filed agai…

11 Best uTorrent Alternatives in 2025 – [All Free]
uTorrent is a great torrent client, functioning since 2005 and serving people for over a decade. It …

31 Best Free Online Streaming Websites in 2025
The best free online movie streaming websites are the antidote to watching movies without getting an…

13 Best Proxy Sites for Anonymous Browsing in 2025
A free web proxy service is perfect for protecting your online identity and browsing the web an…
6 Best Static and Dedicated IP Address VPN in 2025
Connecting to a VPN server assigns you an IP address shared with hundreds of other users. Though thi…
Surfshark VPN Review- How Good Is Surfshark VPN In 2025?
Surfshark VPN started its services in 2018, intending to secure your digital lives, and became domin…

Top 21 Network Scanning Tools – Network & IP Scanner in 2024
Within a network, a compromised or vulnerable device can disrupt your network security in the long r…
How Good Is PureVPN? Let’s Take A deep Review
PureVPN enjoys a good reputation among the people since it has improved its services and logging pol…

How to Hide Your IP Address? 7 Best Ways
In today’s world, how you use the internet can be important for your security and how people perceiv…
2 Best Ways to Encrypt Your Files and Folders in macOS
Your Mac might be one of the most secure and personal devices you have, containing a ton of personal…

13 Best Private Browsers for Android in 2024
Your privacy always remains at risk while using any browser that stores browsing data, login credent…

Top Mac Security Threats: Learn How to Prevent Them
Macs are more secure than Windows devices. However, it is a common misconception that Mac users don’…
21 Best Torrent Sites (Unblocked, Working List) of 2025
Torrenting is the perfect way of downloading and sharing files quickly and easily. However, several …
Cybersecurity Gamification: Everything You Need to Know
The frequency and effectiveness of cyber attacks like phishing are increasing, resulting in dire con…

20 Best Pirate Bay Alternatives in 2025 – Safe and Working
The Pirate Bay was the king of torrents and included thousands of torrent files. However, since its …
Facts-based Review Of Private Internet Access In 2025
The Private Internet Access or PIA VPN is a veteran VPN having more than ten years of experience in …
Is ExpressVPN Still the “Best” VPN Provider? Let’s Take A deep Look
ExpressVPN is one of the best VPN providers that has provided strong internet privacy and security f…
What is Torrenting? How Does it Work? – A Complete Guide
Torrenting is a distinguished file-sharing process that involves numerous individuals (peers) in the…
52 Best Torrent Trackers to Torrent Safely in 2024
Fast downloading speed and privacy are two vital elements while downloading torrent files. However, …

25 Best 1337x Alternatives + Working Mirror Sites in 2025
1377x is one of the best torrent sites, offering the latest anime, TV shows, movies, games, music, a…
How to Stop Someone from Spying on My Cell Phone
Spyware is a cell phone application that has become a common issue these days. But thinking about it…
NordVPN Review- Is that Safe to use? Review in 2025
Nord Security is a leading brand that produces online security solutions and tools, and NordVPN is o…

14 Best Ransomware Removal Tools and Software in 2024
Ransomware is a form of malware that encrypts files on a computer, making them inaccessible until yo…

Is uTorrent Safe to Use? Tips on How to Download Safely
More than 100 million people worldwide download uTorrent. This makes it one of the most popular torr…
What is Attack Surface Management? How Does it Protect You?
Cybercrime will continue to rise and will likely cost $10.5 trillion in 2025. As more companies suff…
How to Encrypt PDF Files on macOS and Windows
PDFs are the most common attachments in the email after docs. These lightweight, presentable documen…

How to Encrypt and Decrypt Folders in Windows in 2025
Windows is admittedly popular and unexceptionally easy to use. However, you might also know it is on…

3 Best Ways to Encrypt uTorrent or BitTorrent Traffic
Torrenting platforms work with a distributed file share protocol; you don’t download a file from sev…

How to Encrypt Your Home Wi-Fi Network
Wireless networks (Wi-Fi) have changed our lives and how we use the Internet for good. It is now eas…
How to Safely Store Large Volumes of Data
For many large companies, the data storage issue is becoming more acute daily. Volumes are growing b…

What is Gmail Encryption? Everything You Need to Know About it
If you use Gmail for electronic communication, whether for personal, business, or both, it’s essenti…
10 Best Ways to Encrypt Your Internet Connection in 2025
The internet is an amazing tool for connecting with other people across the globe and experiencing u…
What is Secure Access Service Edge (SASE)?
Secure Access Service Edge (SASE) is a new cloud-delivered service that combines networking, securit…

NCSC Chief: Clear Rules Needed to Prevent Cyberspace Conflict and Struggle
A safe and secure digital world necessitates a clear definition and enforcement of international cyb…

‘Revive’ has been upgraded to a banking Trojan on Android
This month, Cleafy’s security researchers discovered a new Android Banking Trojan in the wild. Ac…

Asian Industrial Control Systems Targeted by Hackers Using the Shadowpad Backdoor
Unpatched Microsoft Exchange servers in various Asian countries were the target of an attack campaig…
Data Breaches Could Occur Due to Kubernetes Misconfigurations That Were Leaked.
Over 900,000 Kubernetes (K8s) have been discovered to be vulnerable to malicious scans and/or data-e…
What is Incognito Mode? Does it Hide Your IP Address?
Private browsing or incognito mode has long since been recognized as an illusion of online privacy. …

Mullvad VPN Review: Is It Good For Maintaining Security In 2025?
Mullvad VPN is a beginner VPN that focuses on boosting digital privacy and security and is pretty go…
PrivateVPN Review: Does It Keeps Your Activities Private?
PrivateVPN is a relatively new VPN provider that has been functioning since 2013. The VPN provider c…
Hotspot Shield VPN Review: Is It Secure to Use In 2025?
The Hotspot Shield VPN always comes under the radar for its controversial jurisdiction, company owne…
6 Best VPNs for Mac That You Can Trust in 2025
If you’re a Mac user, you know that Apple emphasizes security and privacy. But did you know your dat…

Best Ways to Unblock Netflix from Anywhere
Netflix has started blocking users from accessing its service from foreign countries. For instance, …
IPVanish VPN Review: Does The VPN Lives Up to All Its Claims?
IPVanish VPN is a user-friendly VPN provider with impressive security and privacy features. The VPN …
6 Best VPNs with Free Trial in 2025
Free VPNs have many caveats, such as data and bandwidth caps, limited server locations, speed thrott…

10 Best VPNs for Android – Paid & Free Services
Most people use Android phones and often visit public places like cafes, shopping malls, e…
Proton VPN Review 2025: Security Insights after Privacy Scandals
Proton VPN is the product of Proton Technologies, the same company behind ProtonMail. However, the c…

9 Best Business VPN Services in 2025
As businesses grow, so does the need for secure communication. A business VPN is a perfect solution …

NordVPN vs Surfshark: See Which Provider Stands Out? (Updated)
NordVPN and Surfshark VPN are popular and the best top-rated VPN providers. NordVPN has provided exc…

20 Best NFL Streaming Sites to Watch Live Matches in 2025
The NFL is among the most popular sports in the US and outside. You can watch the NFL games on cable…

6 Best VPNs for uTorrent to Download Torrent Files Safely
uTorrent is the oldest yet most popular torrent downloading software. However, since downloading fil…

ExpressVPN vs NordVPN: Which One Works Best in 2025
NordVPN and ExpressVPN are the two leading VPN providers in 2024. But ExpressVPN has recently been f…

ExpressVPN vs Surfshark: What to Pick in 2025
ExpressVPN and Surfshark are among the most trusted VPN providers out there. Both VPN providers upho…
VyprVPN Review – How Secure And Trustworthy it is?
VyprVPN has improved its service and performance over the past few years. The VPN provider is a priv…

What is a VPN Kill Switch and How Does it Work?
Numerous internet users have now observed the possible risk of online data exposure to ISPs or cyber…

7 Best VPNs for iPhone in 2025
VPN apps are essential for iPhone users because they provide high security and privacy. But how do t…

Avast VPN vs. NordVPN: Which is the Better VPN Service in 2025?
NordVPN and Avast VPN are pretty known names in the VPN industry. Avast VPN is a product of Avast An…

5 Best Fastest VPNs to Use in 2025
Besides security and privacy, fast connection speeds are users’ top priority when using a VPN. No on…
10 Best Free VPN in 2025
Free VPN services are an easy and cheap way to increase your internet privacy and security without i…
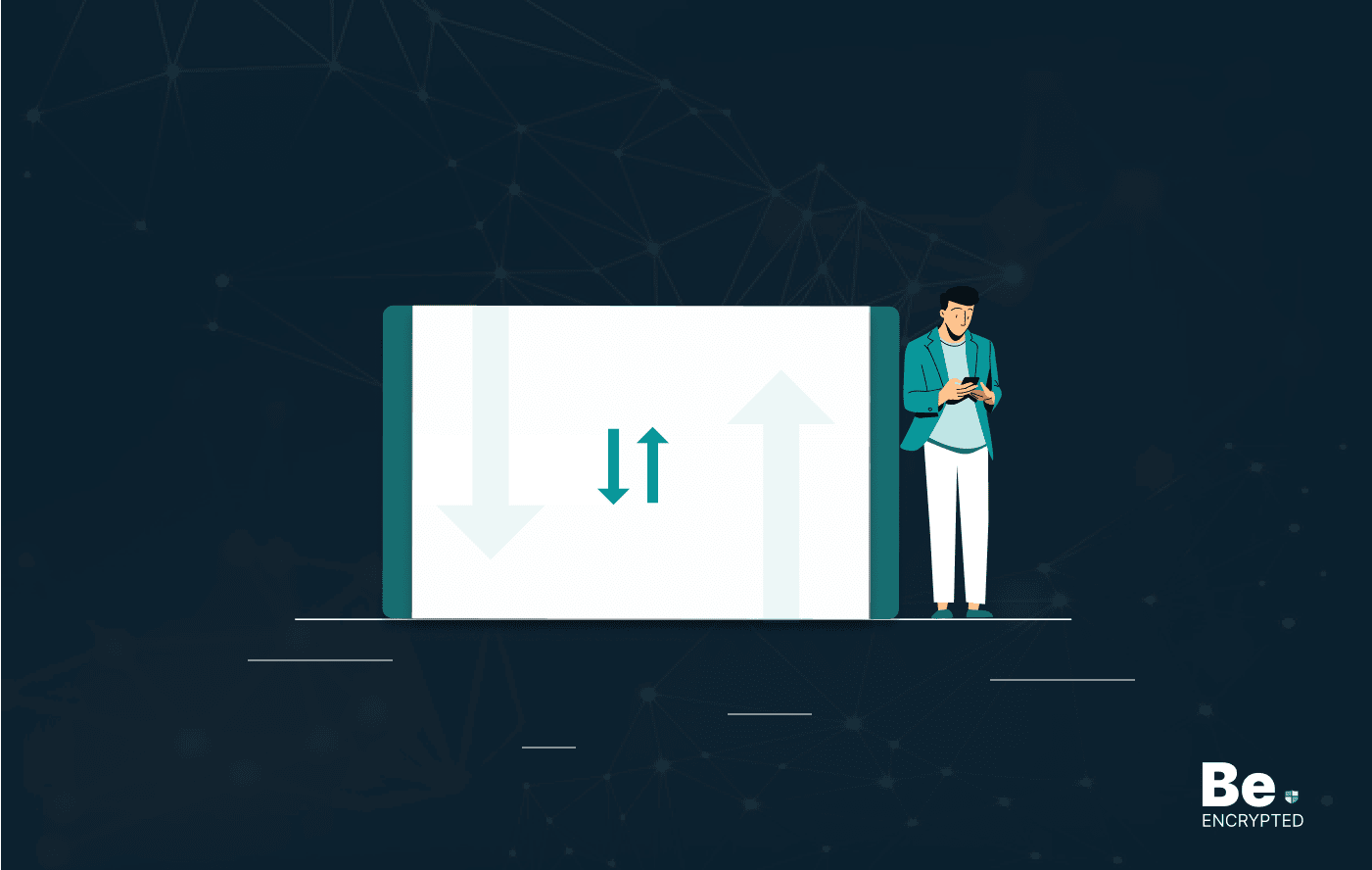
What is VPN Split Tunneling and How Does it Work?
Split tunneling is a VPN feature for anyone accessing foreign networks while connecting to their LAN…
10 Best VPN Services in 2025 – Top Ranked VPNs of All Times
VPN usage has grown more than ever before. A study reveals that almost one-third of internet users u…
Hide.me VPN Review: Is It a Good Choice to Use In 2025?
Hide.me VPN provider is a streamlined VPN provider famous for belonging to the safe jurisdiction of …

What is Browser Fingerprinting and 5 Ways to Hide it in 2024
Everyone wants to remain anonymous over the web, but complete anonymity is like a dream. While you b…
TunnelBear Review 2025: Is It Safe to Use?
TunnelBear is a product of McAfee, a renowned US internet security company. The compa…
What is VPN Encryption? It’s Types and Algorithims
Encryption is a method for enhancing the security and privacy of sensitive data or information that …

Does VPN Slow Down Internet Speed? [Resolved]
A VPN is a helpful tool that provides encryption, which enhances your Internet connection by providi…
Is Avast SecureLine VPN Review: Is It Any Good
Short Review: Avast Scureline comes from a very reputable cybersecurity family. But their loggi…

How to Spot Fake and Real Virus Warnings on Android
In 2024, Android is the world’s most popular mobile operating system. With over 3 billion users from…
Why is Opera VPN Not Working? How to Fix Opera VPN?
Before going any further, the first thing to be clear is that Opera was the first browser to introdu…

Top 3 Trends in Cybercrime You Need to Know
There was a time when the rate of new technology and the sophistication of cyberattacks went hand in…
Understanding Malware and How to Remove it from Your Website
As a business owner, your e-commerce site is your virtual brick-and-mortar store. It’s how you conne…

Protecting Your Web Application: DAST vs. EDR
Web application security is becoming a critical part of cybersecurity operations. Web applications h…

OpenSSL Vulnerability: What Do You Need to Know?
A security hole has been found in OpenSSL, which has now been addressed and fixed. If exploited, the…

6 Steps to Build an Incident Response Plan in 2024
The modern threat environment makes it challenging to protect organizations. An organization’s integ…
What is Facial Recognition? Is it a Blessing or a Curse?
Facial recognition is not a new buzz. It is an advanced method to identify a person’s identity based…

What is Password-Based Authentication? Is Passwordless Authentication Better?
Password security has grown to become a rising concern. Finding a secure password authentication met…
How to Prevent Account Takeover Attacks
Exposure to online account stealing threats is exponentially increasing as more people go online to …

Passwordless Authentication vs. MFA: Which One is Better?
Passwords have quickly become one of an organization’s most significant vulnerabilities. A 2020 Veri…

What is Phishing as a Service (PhaaS)? How to Protect Against It
Cybersecurity has always been a matter of concern for organizations and individuals alike. However, …

How To Check If Your Phone Is Being Tracked – 6 Common Signs To Check!
Mobile phone tracking is a very serious issue. It is one of the most invasive and potentially damagi…

What Is Spyware? Types and How to Remove it?
Most people have no idea what spyware is, let alone the different types of spyware. Spyware is malwa…

What is Keylogger – How to Find and Remove it Completely
A keylogger is a type of spyware installed on a computer to track and record all users’ keystrokes. …

What is Zero Trust Approach: Importance and Challenges
Many businesses have preferred the Zero-Trust model in recent years, and it is gaining popularity da…

13 Best Anti-Rootkit Software in 2024 – [Free and Paid]
There are many types of malware, but the most dangerous is rootkits. Rootkits hide deep in your comp…

Best FREE Anti-Malware Tools For Better Detection and Removal
Quick List Of Anti-Malware Well, if you’re looking for the best free anti-malware software, then h…

How Data Encryption Protects Your Devices
When the COVID-19 pandemic began, cybercrime cases exploded, and it’s only worsening. With the r…

What is Shadow IT? Benefits, Risks, and Mitigation
There is no secret that many people use their work devices for personal use. With the rise of smartp…

What is Ransomware: Types and Prevention Tips
Ransomware is malware that encrypts files on a user’s computer and then demands payment to decrypt t…

Why Should You Use a VPN? 12 Best Reasons
Did you know you’re not alone when you browse the web? Everything you do online is being monitored a…

What is Role-Based Access Control (RBAC)?
Role-Based Access Control (RBAC) is a type of security authorization that regulates access to system…

What is Privilege Escalation – How to Prevent it
Privilege escalation is a standard method hackers use to access systems or data. It’s essentially a …
Comprehensive Guide to Network Security – Importances, Types and Preventions
As the world progresses towards digitization rapidly, network security has become the need of the ho…

15 Best Encryption Apps for iPhone in 2025
Apple markets iPhones as “walled gardens,” a metaphor highlighting the security these devices offer….

What is Encryption and How Does it Work?
Our data is of particular importance to the government and cybercriminals alike. While cybercriminal…

What is Multi-factor Authentication (MFA)?
Today, we store our most essential bits and pieces online as data. This sensitive data is usually pr…

Denial-of-Service Attacks (DoS) – Types and Preventions
Denial-of-service attacks (DoS) are a common way for hackers to take down websites, but they can als…
ZTNA vs. VPN – Which One is Better for Your Company
It’s no secret that the coronavirus pandemic has led to a surge in remote work. In fact, a recent st…

15 Best Encryption Apps for Android in 2025
Encrypting Android phones using the best Android encryption apps is crucial primarily because Androi…

What is SOC 2? A Comprehensive Guide to Compliance
The system of controls known as SOC 2 ensures that organizations protect the privacy and security of…

What is Secure Web Gateway (SWG)? Why Do You Need it?
A Secure Web Gateway (SWG) is a security solution in front of your internet-facing applications and …
Network Security Vs. Application Security (2024 Comparison)
As businesses adopt new and innovative technologies, the need for robust security measures has never…
What are Intrusion Detection Systems (IDS)?
Intrusion detection is one of the most critical aspects of information security. By monitoring netwo…
Business Firewalls: Everything You Need to Know
Most internet users need a firewall, and that’s especially true for entrepreneurs. A business needs …

What Happens if You Get Caught Torrenting?
Torrents fall into the grey area since it is not the act itself that is illegal but the content you …

7 Best Free Encryption Software to Protect Your Data
Encryption is an excellent option for anyone who wants to transfer large volumes of data or ensure t…

What is a cross-site request forgery, and how can we avoid falling victim to such attacks?
Several cybercrimes involve forgery, which essentially consists of creating, modifying, or possessin…
How Trade Wars Impact the Tech Industry?
Many people view the internet as an international landscape where every user is treated equally, as …
How to Stop Third-Party Apps from Reading Your Emails?
In 2021, a report disclosed how third-party applications and developers can view and read your email…

4 Strategies Small Businesses Can Use to Counter Cyber Crime
With the increasing number of businesses, there is always room for confidential storage or managemen…
Artificial Intelligence and its Impacts on Industries
There is an immense noise about artificial intelligence, while multiple news stories about the impac…
European Union MetaData Rentention Law
In 2006, the European Union passed the Data Retention Directive (DRD), which is considered an extrus…

Is Digital Crime the Next Big Threat to Vehicle Owners?
While the concept of driverless vehicles was challenging to visualize even a few years ago, recent f…

Review of the Mandatory Data Retention Law
The data retention laws that are creating havoc worldwide are now being imposed in many countries in…

What Is Malware and Common Types – How To Prevent It?
Malware is a general term used to describe a variety of malicious software that can infect your comp…
Android Ransomware, SLocker’s Source Code Revealed Online
A security researcher has revealed the Android ransomware SLocker’s source code and published it onl…
Improve Your Browsing With The Best Privacy Extensions
While browsing online, you could experience many privacy issues. To prevent such security risks, som…
What is Google Blacklist? How to Prevent it
Google is among the world’s leading search engines. It is entrusted with providing its users with a …
Breach and Attack Simulation: How it helps Improve Security?
According to the FBI’s Ransomware Prevention and Response for CISOs, “more than 4,000 ransomware att…
How to Protect Yourself from MetaData Retention
Many countries worldwide, such as the United States, Australia, and the European Union, have Mandato…

Facebook Privacy Settings: You Shouldn’t Ignore
Facebook is one of the most popular social networking sites, where people share their details, such …
VPN vs. Firewall vs. Antivirus: Which One is Better?
More often than not, most people tend to forego their devices’ security for pure confusion. With …

Top 5 Benefits of Blockchain Technology
The increasing dangers of cyber-attacks can now bring your entire network to a halt. Therefore, it i…

How to Remove Ampxsearch.com Virus from Your Device
We download browser extensions or third-party software into our computers daily without knowing abou…
How Has the Evolving Nature of Bluetooth Hacks Impacted Cybersecurity?
Nowadays, most of us look down on Bluetooth as a vestigial feature that we only turn to if we have n…
How SMBs Can Reduce The Growing Risk of File-Based Attacks?
Small and medium-sized business networks are subjected to cybersecurity risks every day. Any worker …

4 Best WhatsApp Alternatives in 2024 – Safe & Secure
WhatsApp is among the most popular instant messaging apps, boasting over two billion users. The app …
How AI Impacts Cybersecurity in 2024?
AI has been the core fantasy of many technologists and tech geeks. Various works have been done to a…
How to Protect Web Applications from Breaches?
Businesses now commonly deploy web applications to interact with customers and support their interna…

How AI Helps to Bridge the Cybersecurity Skills Gap?
Given the dire nature of the current, ever-evolving threat landscape facing enterprises today, the r…

6 Best TrueCrypt Alternatives For Better Encryption
TrueCrypt was popular among millions of macOS and Windows users. For data encryption, it creates enc…

How to Disable WebRTC on Various Browsers?
WebRTC became popular in 2008; major browsers have adopted it as a default feature for their users. …
How to Get Free WiFi Anywhere with Privacy
When traveling, we constantly search for free Wi-Fi, and you get a massive list of available Wi-Fi n…

How to Remove and Prevent Facebook Malware
Facebook is the world’s most-used social media platform, with over 3 billion monthly active users. T…
Why Companies Need AI Software?
Artificial intelligence has revolutionized the business industry, providing marketers with significa…

4 Best VPNs for Australia for Fast Streaming and Privacy in 2025
Australia is one of the countries that faces internet censorship. Under the Australian data retentio…

What is Phishing Attack? How to Protect Yourself from it?
Want to know how hackers can hack your account? Do you learn the techniques a hacker can use to hack…
Future Of Artificial Intelligence – Expert Opinions
Artificial intelligence is not a new concept for people. Machine learning and robots were infused in…
10 Tips to Use Public Wi-Fi Securely
Today, the Internet and Wi-Fi access are essential for our routine lives. However, we must not forge…

Is UC Browser Safe to Use? 2024 Review
Nowadays, many people choose the UC Browser because they know it is one of the fastest and best web …

A Guide to Choosing the Right VPN for Downloading
How to hide downloading files from ISP? From the very start of the hilarious popularity of P2P file-…
6 Shocking Ways of Data Collection | Secure Backup
Being tech-savvy, you would be familiar with tech or security news informing you about your data col…
What is Port Forwarding and How Does it Work?
Port Forwarding is a technique for redirecting computer signals between the local network and the In…
10 Best Firefox Privacy Extensions in 2024
Firefox has many add-ons that guarantee security and remove unwanted ads and pop-ups. These add-ons …
Torrent Proxy Settings With uTorrent And BitTorrent
Proxies are known for surfing the web anonymously. They offer a means to hide your real identity and…
What is a Botnet: Usage and Prevention
Robot Networks, or Botnets, are exclusively designed for financial profit purposes, whereas many bot…
Is Torrenting Illegal? What Happens If You Get Caught?
Torrenting is a widespread technique for downloading files such as movies, songs, games, and others …

How to Delete Google Search History
We all think that clearing our browser history deletes every search we make. Do you believe that? …

How to Torrent Safely and Anonymously? – Easy Guide
Torrenting is fascinating, but it is also risky. You can get caught torrenting the latest movies, TV…

What is DNS Hijacking? How to Prevent and Fix it?
DNS Hijacking, also known as DNS Redirecting or DNS Poisoning, is a strategy used by cyber pillagers…

Mandatory Data Retention Law in Germany
In January 2016, the German law on data retention came into effect to ‘strengthen’ the national cybe…
What is Scareware and How can I Avoid it?
Scareware, known as deception software, earns its name from introducing itself to the targeted victi…
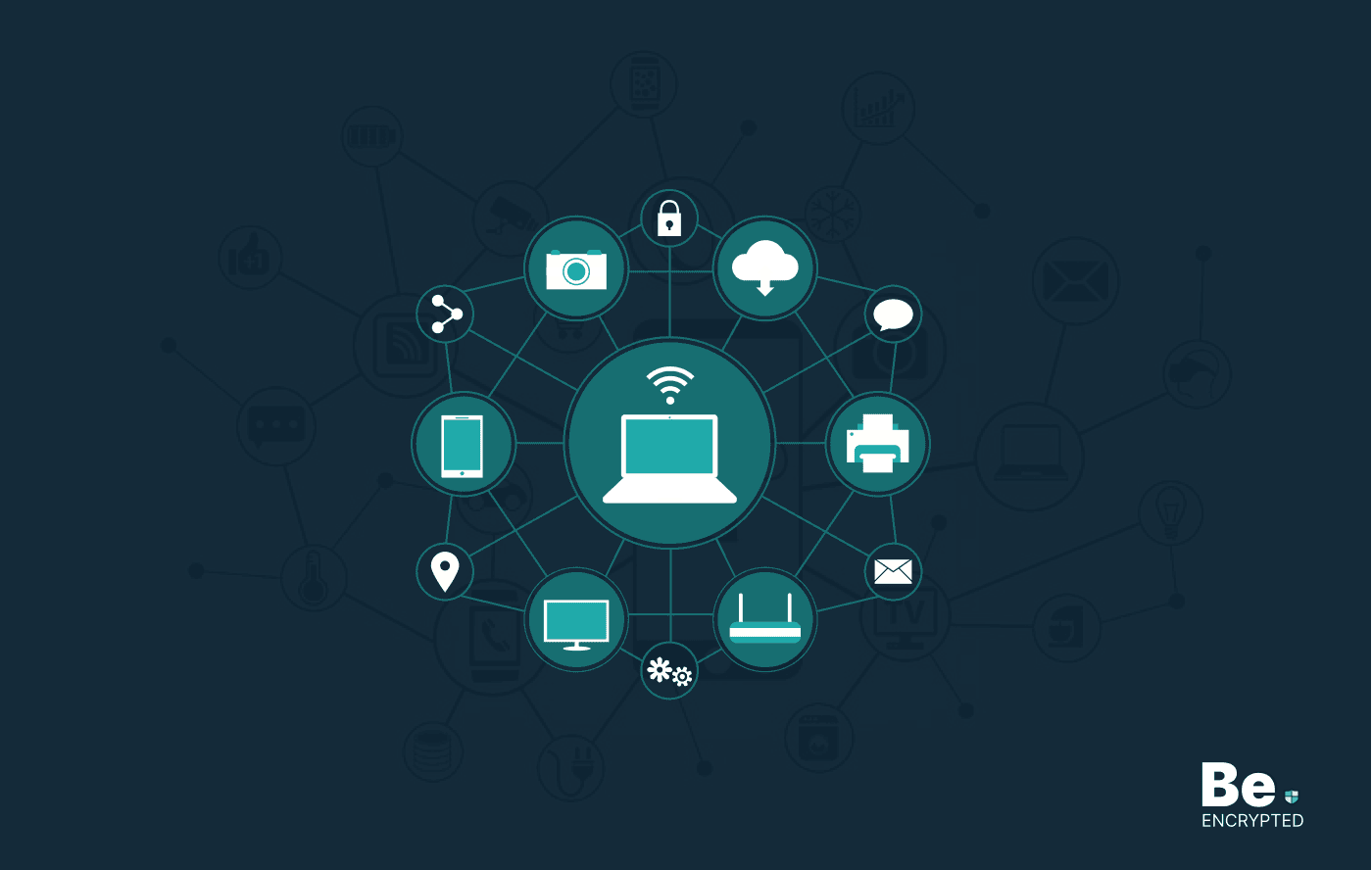
Internet of Things – What to Expect in The Coming Year?
The Internet of Things (IoT) has already boosted the concept of interconnectivity, and we have seen …

What is VPN Over TOR? How to Use It?
There are some pretty long debates these days; we thought we might summarize a little. Most people g…

Surveillance practices in Canada, Facing Criticism
With the revelation that the Canadian Revenue Agency (CRA) regularly supervises social networking si…
Difference Between Hackers and Crackers
Nowadays, the internet sometimes provides us with complex news and information that we do not even u…

What is Australia Data Retention Law? How to Protect Yourself
The countdown for ‘intrusive data surveillance’ has expired after the 18-month deadline. From this d…

Small Tech Investments to Optimize Your SMB
Many small business owners shy away from investing in modern technological solutions. Price is often…

The 5 Best VPNs for Windows in 2025: Fast & Safe
Windows is currently the preferable operating system but is exceedingly open to attacks. However, Wi…
Best Practices to Create an Effective CSIRT in 2024
Most organizations have a security operation center (SOC) and CSIRT. However, both are entirely diff…
Top 7 IoT Vulnerabilities That You Know About in 2024
IoT devices’ security and safety, mainly intended for client use, remain at significant risk. This i…

What is SecValOps, and Why Do Organizations Need It?
Cybersecurity expert Amital Ratzon calls SecValops the next step in proactive security. This is a ne…

26 Best Nyaa Alternatives to Watch Anime
Nyaa is one of the most famous BitTorrent platforms, offering East Asian content. It was the leading…

10 Ways to Unblock Websites from Anywhere
When a website restricts users from accessing the content, it annoys them. However, such website res…

8 Best No-Log VPN Providers in 2025
With the rapid spread of technology, internet privacy and security get tossed out of the box. For th…

Can You Be Tracked If Using a VPN in 2025
Virtual Private Network (VPN) is a privacy tool with many well-known features. However, there are qu…

Best Free VPN for FireStick & Amazon Fire TV in 2025
The Amazon Fire TV Stick and Fire TV are large plug-and-play devices that simplify streaming on HD T…
Does VPN Protect Me? Is That Really Works?
VPN is a buzzword among the netizens of the present era. But is the hype worth it? Does VPN actually…

Can ISP See Your VPN Traffic? Let’s Find Out
According to Google Trends, a massive flux has been reported in VPN searches, whether it is a paid o…
DotVPN Review 2025: Is It Any Good?
DotVPN is a VPN provider believed to encrypt your data traffic unblock websites, and …

Best Zenmate Alternatives to Use in 2025
Zenmate is a Virtual Private Network (VPN) based in Berlin, Germany, with free and paid services. Th…

How to Choose a VPN for Remote Work in 2025
Since the COVID-19 pandemic, employees have started working from home, and cybercrimes have increase…

Digital Wallets: How to Protect it from Cyber Threats
Digital wallets are increasingly being developed to perform more than just monetary transactions; th…

5 Ways to Protect Your Privacy on Social Media
Using social media comes at the cost of our privacy, and that is because of the companies behind the…
Big Data Security Analytics: A Weapon against Rising Cyber Security Attacks?
With the open-end digitalization of the business world, the risks of cyber attacks on companies have…
Avoiding Security Misconfigurations Through XSPM
Cybersecurity teams have the unenviable task of ensuring the security of the organization. This resp…

Children’s Online Privacy Protection Act (COPPA)
You probably think your site is safe by simply posting a privacy policy in your site’s footer. Still…

How Dangerous is to Download Torrents Without a VPN?
Torrenting involves sharing and downloading copyrightable files like movies, music, and books. If yo…

Cloud Asset Management: Keeping Your Data Secure & Private
Cloud-based data services offer businesses a great value proposition, including IT cost efficiency, …

Browsec VPN Review 2025: Is It Worth Your Money?
Author Findings: While writing this Browsec review, I have plenty of flows in the service. Found DNS…

Android vs. iOS: Which is Secure to Use?
Android and iOS operating systems are gaining popularity, and millions of sets are marketed yearly. …

5 Ways to Unblock Websites on Google Chrome in 2024?
People using Chrome cannot adequately secure their online browsing through alternative settings. How…

5 Best VPNs for Chrome in 2025
Chrome took the Internet world by storm just as it was released in the market. Google launched the C…

What is DNS Leak? Best Tools to Conduct DNS Leak Tests
In this article, we will guide you through performing DNS leak tests and actual DNS leak test&n…

20 Best Private Search Engines For Anonymous Browsing
Search engines like Google, Bing, and Yahoo risk your digital privacy by tracking and recording ever…
What is Malvertising: Detection & Preventive Measures
Malvertising is a way to inject malware into your computer via maliciously coded ads. These ads come…

What is Key Escrow? How is It Different from Key Recovery?
Do you know what the concept of escrow is? Well, allow me to give you a storyline view of it. Kev…

Ways to Defend Your Site from SEO Attacks!
An increased focus on SEO among small businesses has led to cyber-attacks that could harm your searc…

The Internet of Things (IoT) Further Complicates Cloud Security
The Internet of Things, or IoT, is a new digital interaction that promises to bring numerous changes…
Top 5 Biggest Data Breaches in the UK of All Time
The frequency of breaches isn’t limited to one or two a year. Likewise, the targets of the attacks a…
How to Block ISP Tracking in 2024
ISP (Internet service provider) keeps hold of everything on your bandwidth, no matter what they say …
How to Avoid IoT from Getting Doomed?
The IoT industry flourishes every day, and because of this, IoT is present all around us. Its benefi…

15 Best Cybersecurity News Sources in 2024
The world of cybersecurity is continuing to evolve at warp speed. We face new threats daily, and sce…

Is Zoom Safe to Use in 2024?
Zoom was a name we were unaware of before the deadly COVID-19 pandemic hit the world and its civiliz…

What is Clickjacking and How to Protect Yourself From it
Hacking and data attacks are made in many ways, which help an attacker access your information. But …

How to Setup Wireless Network for Your Mac Computers
If you have two or more Mac computers and want to connect them for fast and hassle-free sharing of f…
Windscribe VPN Review 2024 – A Lifetime Free VPN
Windscribe VPN (Location – Canada) Countries: 20+ | Server Locations: 45+ | Number of Servers: 20…

How ML Benefits the E-Commerce Industry?
Machine learning technology is helping e-commerce companies transform the customer experience. It ma…
What is SSL VPN and How Does it Work?
SSL stands for Secure Sockets Layer and is the security standard when a web server and a web browser…
What is PPTP VPN Protocol and How it Works?
PPTP stands for point-to-point tunneling protocol and is one of several methods to implement virtual…
How VPN Servers Connect and Provide Anonymous Connection?
A virtual private network (VPN) is a hardware and software interface between a computer and an Inter…

5 Effective Tips for Safer Online Banking and Transaction
Internet banking has evolved over the years to become a formidable technology today. Now that we can…

Practical Steps to Cybersecurity for Law Firms
An in-depth analysis found that businesses containing customers’ data, like law firms, have become m…

How to Secure Electronic Health Records
Electronic healthcare record systems and databases have facilitated the entire healthcare industry. …

What to expect from Artificial Intelligent (AI)?
Emerging technologies are already swift; however, the coming year could embrace significant advancem…

Fileless Cyber Attacks: How to Prevent Them
According to a recent report by Barkly and Ponemon Institute, “2017 State of Endpoint Security Risk,…

Cybersecurity Basics: Are They Enough for Current Threats?
There is no formal definition for essential cybersecurity, but based on how most organizations perce…

Net Neutrality: Is it Good for Us?
When you go online, you expect to have full control of your internet experience, which means you exp…

6 Effective Techniques to Prevent Ongoing Threats at US Border
U.S. Homeland Security Secretary John Kelly signaled the presumption that U.S. border agents could s…
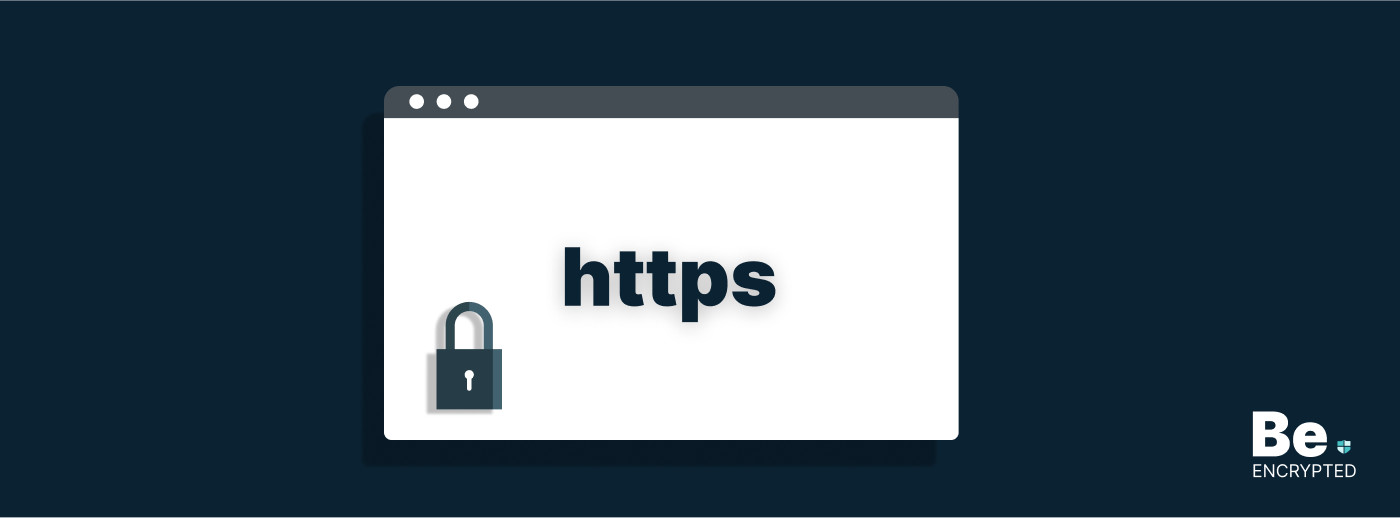
What is HTTPS? How Does it Secure Your Connection?
With the constant increase in social networking, a vast amount of sensitive information is being tra…

What Does The Incognito Mode Do? How to Turn it On
The incognito mode was initially created to allow people who share computers to browse the Internet …

The Best USA VPNs in 2024
Acquiring digital security and privacy has become imperative, especially if you’re in the USA. Becau…

How to Test Your VPN Encryption and Security Levels in 2024
VPNs are online privacy and anonymity tools that offer relief from several infosec issues, such as I…

10 Best Browsers With Built-in VPN in 2025: The Detailed Guide
VPN is the best-known method for enabling online anonymity, which is why browsers with built-in VPNs…

What You Need to Know about Email Security
Email is among the biggest achievements in the world of communication. In 2015, it was reported that…
What is FileVault Encryption in Mac and How to Use it?
FileVault is a Disk encryption program for macOS that saves your data if your Mac is ever stolen or …

5 Best VPNs for Kodi in 2024
Kodi is an open-source and one of the most portable media players in the streaming industry. It is f…

The Best VPN for Streaming in 2024
Online streaming is one of the many ways people relax and spend their leisure time. However, with th…
5 Best VPN Services for Linux in 2024: Fast & Secure
Linux is the most popular open-source alternative to Windows and is the standard server OS many gove…

Top 7 Weakest Points of VPN Security
Your VPN is the safety net between you and the rest of the world. That layer of security is only as …
Betternet VPN Review: Is Worthy To Use?
Betternet is a free and premium VPN service that offers access to free users via ad support and to p…

11 Most Frequently Asked Questions About VPN
A Virtual Private Network lets you create a safe and secure connection to another system. It can be …

7 Best VPN for Firefox in 2025 – Paid & Free
Nowadays, people are looking for browsers with enhanced features and continuously updating their ser…
I2P vs TOR vs VPN vs Proxy Which is More Secured?
Security tools such as I2P, Tor, VPN, and Proxy are the most preferred in an era of such privacy has…
Hola VPN Review 2025: Is It Safe to Use?
Internet-hassle for hola VPN and confusing debate for hola safety forced me to hatch a detailed hola…
What is Social Engineering? Examples and Prevention Tips
Social engineering is generally used for various malicious activities accomplished by human interact…
Is Zenmate Safe To Use? Detailed Review
Note: This wouldn’t be the regular product review; in this Zenmate VPN review, I will keep everythin…

How to Spot a Fake VPN – Quick Tips
Virtual private networks (VPNs) are great—if you use a legitimate service. VPNs add an extra layer o…
How to Encrypt Disk in a Linux Enivronment
Encryption has become a mainstream term as a solution to many privacy risks. Privacy advocates and s…

How to Use Mailvelope to Send Encrypted Emails
Over the last few years, we have repeatedly witnessed that our communication mediums are no longer s…

How to Tackle Security Challenges While Working Remotely
The cybersecurity landscape changes over time. However, the post-COVID-19 pandemic modifies and disr…

How Can Your USB Device Pose Security Risks
A Universal Serial Bus – USB device is a helpful external data storage device. It includes a flash m…
This Is “How To” Download Torrents Anonymously
Torrenting is simply a file-sharing process that involves several individuals in the downloading pro…

Attacks by Cybercriminals Will Become the Main Threat in 2024. Privacy Issues Tendencies
Internet Privacy is the main Concern today Advertisers track your online activities and int…

12 Signs to Know if Your Phone is Hacked
Hackers are becoming increasingly creative and invade your phones to track your online activities, c…

How to Protect Your Privacy on Android
The introduction of smartphones has morphed into an integrated part of our lives. We store most of o…

How to Check If Your Webcam Has Been Hacked in 2024
Webcam hacking or competing is something that people usually witness in detective movies, but this i…

5 Must-Do’s for Organizations that are New to Encryption
Encryption technology is one of the most popular techniques for data security. Essentially, it makes…

12 Tips to Achieve Anonymity on Android or iPhone in 2024
When considering the modern threat landscape, it is obvious how crucial it is for iPhone and Android…

What is Two-Factor Authentication (2FA)?
Cybersecurity attacks have gone wild, so implementing multiple-layer protection is a must. According…
What are Endpoint Protection Platforms?
Endpoint protection platforms (EPPs) prevent file-based malware and other attacks on endpoint device…

Techniques Cyber-criminals Uses to Get Access to Your System and How to Protect Yourself?
It is a common myth that the internet is so vast that it won’t be easy to attack my system. Most peo…

WhatsApp Security Issues You Must Know
Founded in 2009, WhatsApp has quickly become immensely popular—with a whopping 2 billion users …

Top 6 Online Privacy and Security Tips for Travelers
There was a time when people carried only a few things while traveling. But modern times are differe…
How To Download Torrent Safely
Torrenting is the most discussed topic these days, so we decided to take a look at it. This article …

10 Tips to Increase Your iPhone Security
Your iPhone is the key to your deepest secrets but is still vulnerable to cyberattacks. Hackers are …
What is Passwordless Authentication?
Passwordless authentication is still relatively new to most of us, and the implication is still uncl…

10 Best Antivirus Software in 2025 – Free and Paid
Antivirus software is like police at the gate of your computer system, preventing threats from enter…

4 Best iPhone Security Apps You Need to Know in 2024
Security is always the first priority for phone users. If you are an iPhone user, the following four…
Best WordPress Hosting For Bloggers
WordPress is the most used CMS all around the world and that’s because the ease it provides to the u…
Is Hostinger Worth It? compateblity WP
Hostinger was started back in 2004 by the company “Hosting Media” that is located in Kaunas, Lithuan…
8 Best WordPress Security Plugins For Top Security
WordPress is the most used CMS “Content Management System” and it’s free to download and use. Thousa…

Things Organization Should Know to Secure Their DNS
DNS plays an essential role in running online businesses like websites, online services, cloud conne…

How to Increase Your WiFi Router Privacy With 7 Easy Steps!
Wi-Fi connections could be unsafe when there are suspicious connections to them. But how could it be…
How to Migrate Your Business to the Cloud
The future of networking lies in the cloud, and for a fast-growing business, you need to switch to c…
The Best SSL Certificate Providers to Secure Your Site
SSL certificates are an essential and elemental part of the modern website required for running your…

How to Secure Your eCommerce Website with an SSL Certificate
SSL certificate being a necessity for today’s age has too compelled Google and other browser authori…
How to Solve Error Code 0 When Copying Large Files
Have you ever encountered Error code 0 in your finder when copying large files from your Mac to an e…
How to Make a Bootable Flash Drive for Mac OS X
Mac computers and Mac OS X make the most stable combination in the world of computers. Nevertheless,…
Protect Your Website From Hackers – Prevent Hack Attacks
The damage done by a hacker is irreparable. You may not consider your website worthy being hacked fo…
How to Encrypt Your Windows Phone: A Complete Guide
Encryption, in general, is a problem. It scrambles the contents of a file to be encrypted. An encryp…
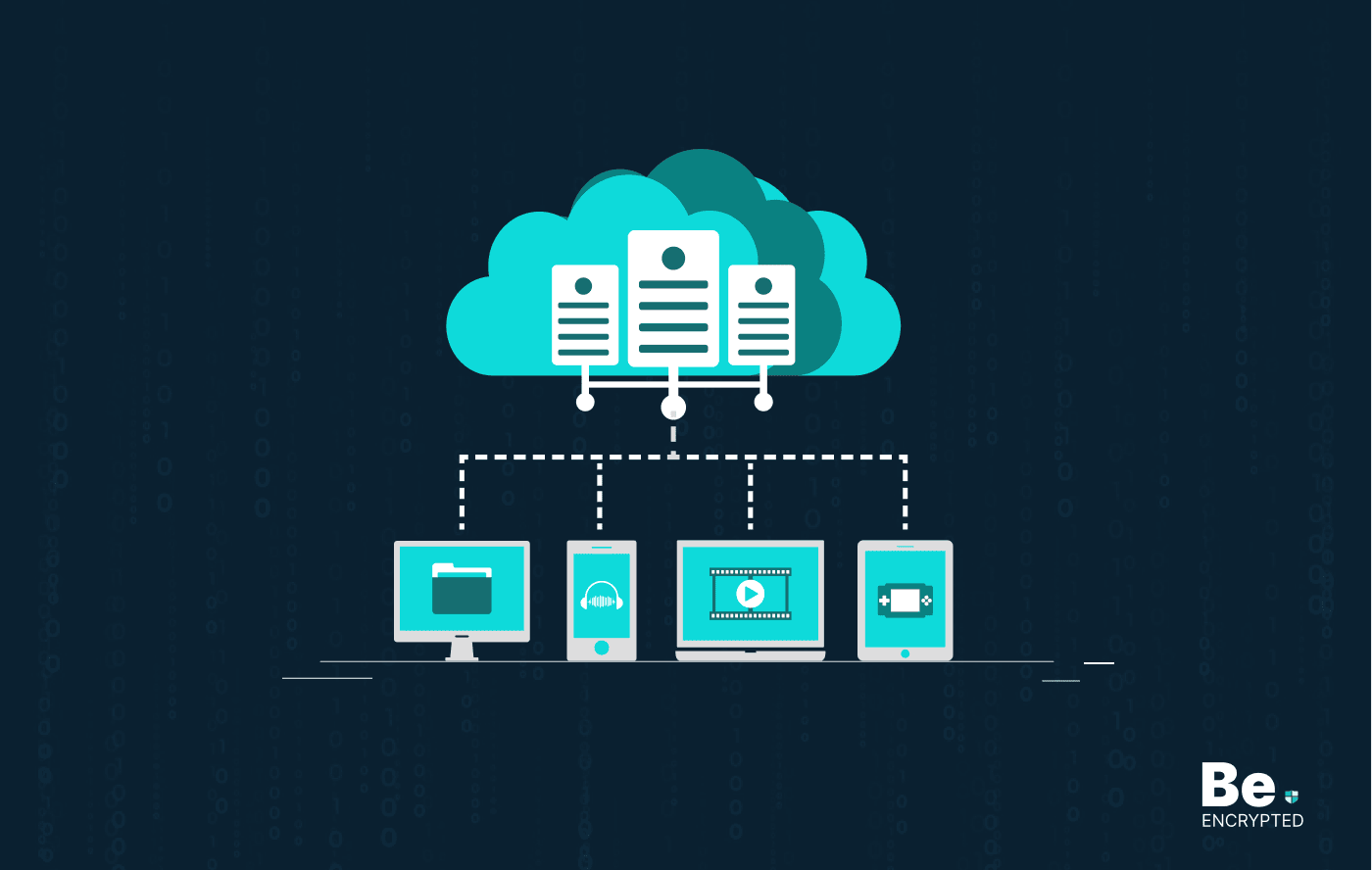
Is Cloud Storage Safe & Encrypted?
The information technology industry sometimes takes the lead itself. Cloud storage has become one of…
How to Encrypt Your Hard Drive in 2025 [Windows and Mac]
Encryption is receiving tremendous attention and positive response due to the hindrance it has creat…

How to Encrypt Macintosh or Mac Systems
Earlier this year, reported by Palo Alto at CNBC, major ransomware, named “KeRanger,” hit Mac u…

Website Security Certificate – What It Is And Why You Should Care
The error “There is a problem with this website’s security certificate” is quite commonly observed. …

Scammers trapping users via fake VPN services after anti-privacy bill
Recently signed by trump, the new broadband laws will allow ISPs to sell your data without any legal…
5 Best Hosting Services to Use in 2024
When searching for the best hosting provider the consumer may face a little trouble, mainly bec…

How to Prevent Cybersecurity Breaches in Healthcare
You might be surprised that cybercrime has also increased in healthcare organizations. Like any othe…

Amazon Employee Reveals New WhatsApp Bug Which Exposes Entire Chat in Plain Text!
One of the most famous and widely used social networking application WhatsApp gets infected by a nas…

WhatsApp Coming Up With Fingerprint Authentication For Android Users
The renowned messaging app has started the work to introduce fingerprint authentication feature in a…

Your Reddit Account Might be Locked Over Security Concern
The uncounted number of Reddit accounts have been locked out due to the prevailing security risk fou…

Australia’s New Encryption Law Give More Power to Authorities to Get Hold of Encrypted Communications
The Australian government has passed a new security law recently. Under this law, the authorities wi…

21 Popular Apps Exposed, Sharing User Data With Facebook
Out of 34 reviewed apps, at least 21 were found sharing user data with the social media platform, Fa…
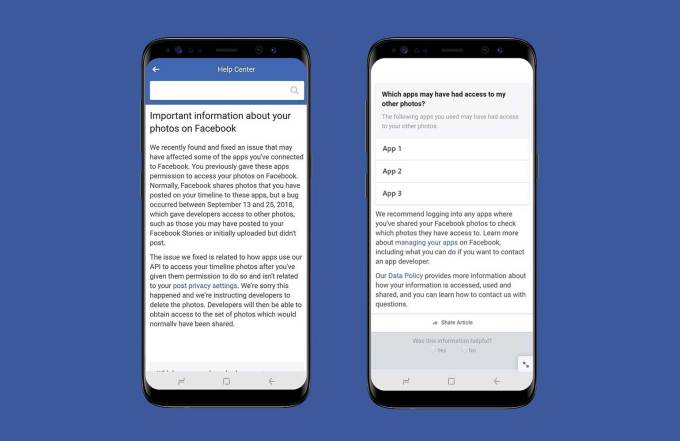
Facebook Unveils Bug Exposed up to 6.8 million user’s unposted photos
The bug permits 1,500 apps built by 876 developers to view user’s unposted photo which gets stored a…

Pirate Bay Founder’s ‘’Njalla’’ Slammed for Protecting Pirate Sites
The Pirate Bay founder Peter Sunde in 2017, declared the launch of a completely new privacy-oriented…
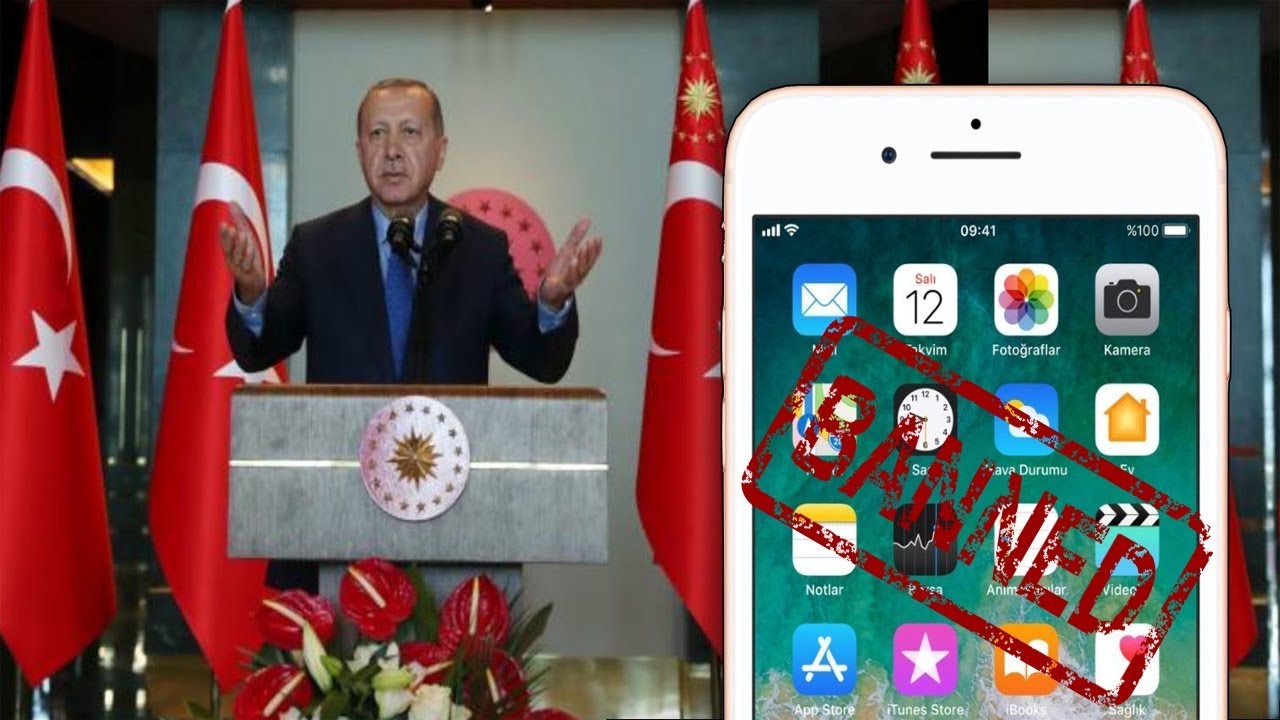
Turkey To Boycott iPhone And US Electronics – Are They Hurting Themselves?
On Tuesday, the Turkish president Tayyip Erdogan proclaimed that the electronic products from the Un…

Facebook Plays Cleverly Against New EU Privacy Rules
The social networking platform, Facebook has confirmed Reuters on Tuesday to shift responsibilities …

Net Neutrality Repeal: EFF Once Again in Opposition to Pai’s Unfair Settlement
The final call is here. The results of the elections conducted for the killing of net neutrality hav…

Net Neutrality : Ultimate FCC Election, Just a Few hours Away
The “NO CARE” strategy: The story goes a long way back but the gist of it is the election about to b…

Ethereum at its Highest Peak, Becomes Second on the List after Bitcoin
The biggest rival of Bitcoin, Ethereum has reached an all-time height of $425.55 on Thursday, as dep…

Facebook Users Can Now Spot Fake Russian Accounts Via “New Tool”
On Wednesday, Facebook has announced its plan to initiate a web page that would allow users to exami…

Samsung All Set To Compete AI Development
Looking at the extreme pace of Artificial intelligence, Samsung has also revealed their plans to cre…

Skype Dismissed From Apple App Store In China
Along with many popular apps, now Skype would also be inaccessible for Chinese citizens. The app has…

Tether Claims the Steal of US Dollar Token Worth $30
On Monday, the cryptocurrency firm, Tether has claimed that their system is hacked, as a result of w…

Amazon Announce To Launch Secret Region Service To assist CIA
The popular cloud storage platform, Amazon has announced to launch a service designed to assist CIA …

Unable to Regain Prominent Browser’s Trust, StartCom will Halt all Certificates till 2020
The Chinese certificate authority StartCom has announced to halt their certificate issue by the end …

Pentagon Data Leak; Fully Secured Data, Exposed On Amazon Servers
A Researcher at cyber Security Company, UpGuard, Chris Vickery has discovered the Pentagon data leak…
ABC Validate the S3 data leak as Claimed by Kromtech Security Firm
According to Kromtech Security Center, the Australian Broadcasting Corporation has mistakenly leaked…

FCC’s December Vote Could Be the Ultimate One to Kill Net-Neutrality Rules
The prolonged discussion and debate regarding net neutrality rules may end soon. The FCC has decided…
Max Schrems Entitled To Sue Facebook Over Privacy Concerns
Max Schrems expressing his thoughts regarding the matter in a video; First little video summary on …

Cryptocurrency Worth $1 billion Stolen by hackers through CryptoShuffler malware
Hackers have now managed to access popular cryptocurrency wallets including Bitcoin which were worth…

“Ban on Kaspersky can evoke regrets”, Russian respond to the US
As the government of United States has put ban on federal agencies for using a Russian brand of secu…

Kaspersky banned!! : US amid fears of Russian espionage
The government of United States has put a ban on federal agencies for using a Russian brand of secur…

Russia in Reprisal, FA boost up Cyber-security ahead of 2024
England if beats Slovenia on October 5 so it will be qualified for the tournament which begins next …

Equifax Breach: Are you one of 143 million hacked victims?
Equifax, a credit and other information supplying service discovered a security breach that may have…

Instagram Hack: Celebrity details exposed worth just ‘2 cups of coffee’
This seems really terrible when an unknown person pops out from nowhere and starts purloining your p…

Verizon affirmed Video Throttling as Accused by Netflix Users
Yesterday, the users of the Verizon Wireless network noticed that Netflix videos stream at a conside…

Even 9 Million Comment Outburst couldn’t stop Trump’s endorsement to Net neutrality overruling
To the hottest internet issue nowadays, the FCC has received a record response of 9 million public c…

Net-Neutrality Fight Encompassing Internet World
The Next Step to Revert Obama’s Open Internet Rules As a proceeding step to the turnaround of Obama’…

Ukraine at the Risk of other Cyber Attack after ‘NotPetya’
The immense cyber security attack causing global damage previous week, launched through Ukrainian so…

Week’s Top Trending Cyber Security News, at a Glance
WikiLeaks Reveals CIA Hacking PCs via USB The popular WikiLeaks Vault 7 series has more revelations…

WikiLeaks Vault 7: CIA’s Malware Could Hack Unconnected PCs via USB
The latest Vault 7 documents released by WikiLeaks enclose the techniques CIA is using to infect so-…

Russia Targeted Election Systems in 21 States, U.S Officials Confessed
On Wednesday, Department of Homeland security official testified the Russian Government individuals …

EU Wishes To Prohibit Backdoors in New Data Protection Regulations
The European Union is considering to officially forbid the implementation of the so-called “backdoor…

California Decides To Abstain From the Anti-privacy Bill Signed By Trump
Over the past few months, we have witnessed the impacts of the anti-privacy bill signed into law by …
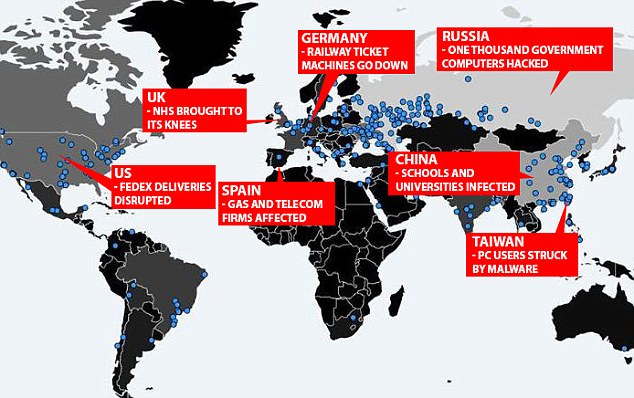
Biggest Ransomware Attack in History Halted By The ‘Accidental Hero’
More than 45,000 cyber-attacks were recorded in nearly 99 countries around the world, including the …

Forced Search & Seizures at US Border is Abuse of Constitution – Rebecca Jeschke EFF
Soon after Trump has banned the entry of people, US border agents have increased inquiring citizens …

Redefine Your Privacy Measures After Trump’s Signature Threatens Users Privacy
About a week ago the congress has voted in favor of ISPs selling your personal data. Suspending the …

Hackers Threaten Apple For Ransom, Here’s How To Protect Your iCLoud Account
Turkish Crime Family, a seven-membered hackers group claims their ability to access as many as 250 m…

Wikileaks, CIA, or FBI, Encryption Is Still Balancing Net Neutrality, Talks CMO of NordVPN
Accusing CIA of conducting mass surveillance, Wikileaks has created a hot environment by releasing a…

Equivocal UK Citizens Agonizing Over Mass Surveillance
The frantic situation created by the combined efforts of surveillance camera technology and “big dat…

McDonald’s delivery app leaks 2.2 million customers data
The most used application in India; Dubbed Mcdelivery leaked the personal data of about 2.2 million …

Mobile numbers of former prime ministers and several MPs, accidentally published online
Department of parliamentary services(DPS) have confirmed that personal mobile numbers of several fed…

WhatsApp image could be hacker’s key to your account details
WhatsApp, one of the most used and famed app for messaging has now been disclosed to be at risk when…

Facebook Takes Huge Initiative Against Surveillance
The social media is growing in their roles for society and is taking up challenges that they were ne…

Ajit Pai’s decision Is A Spark For War Among FCC and Consumers
The new FCC chairman Ajit Pai has reversed the net neutrality rules, set by the former establishment…

Fix NSA first, Snowden advises President Trump
Edward Snowden in an interview by The Intercept’s Jeremy Scahill at the South by Southwest Conferenc…

White House Member’s Favorite Confide App Can Leak Their Secrets
Confide – an app known to be preferred by white house staff officials, providing “military level end…

Another Giant US Corporation Recklessly Leaks Massive Database
The database exposed, has more than 33 million records along with unique e-mail addresses and inform…

NHS staff entrapped in a ‘data security attack’, losing personal details
A data security attack has been reported, exposing the detail that several NHS staff’s personal info…

Samsung, LG, and plenty android devices found with pre-installed malware
A severe infection has been found in almost 38 android devices, belonging to a populous telecommunic…

StoneDrill: A Disk Wiping Malware Attacks Cybersecurity
In 2012 Saudi Aramco, the Saudi national oil company got hacked by a disk-wiping malware Shamoon 2 t…

Stopping ISPs From Selling Your Data Seems Unlikely By FCC
Protecting Customer privacy and security, Federal Communication Commission has delayed its own new r…

Wikileaks May Severs Ties Of CIA & Silicon Valley, Says Former CIA Chief
Former CIA director David Petraeus viewed the recent outburst of WikiLeaks document Vault 7 as a ven…

CIA Backfires On Wikileaks, Says Surveillance Is For ‘Protecting’ Citizens
In response to recently released documents by WikiLeaks, CIA has issued an official statement negati…

FBI Director Purports Encryption As Dark And Hurdle In Investigation
The FBI director, James Comey warned that the chances of collecting evidence through the cyber world…

WikiLeaks To Help Tech Giants Fix CIA Exploits Before Going Public
WikiLeaks, on Tuesday, released a thousands of paper files, accusing the CIA of employing software t…

Hacking Smartphones Is A Game For CIA, Reveals WikiLeaks
Wikileaks released a trove of files on Tuesday that confess about the CIA’s expertise on hacking you…

WikiLeaks Unveils Smart TV Surveillance By US Intelligence
Would you ever prefer staying under constant surveillance? The expected answer will be ABSOLUTELY NO…

More Than 1 Billion Personal Details Leaked By Spammers
Neglecting to password-protect a database backup, an American organization has exposed about 1.37 bi…
What Is Web Hosting? Types Of Web Hosting
Once you create a website and want to make it available to users then the basic thing to do is to br…

Dark Web Is Selling A Million Gmail & Yahoo Hacked Accounts
Lately, Dark Web marketplace is being a sale store for the personal information and credentials of m…
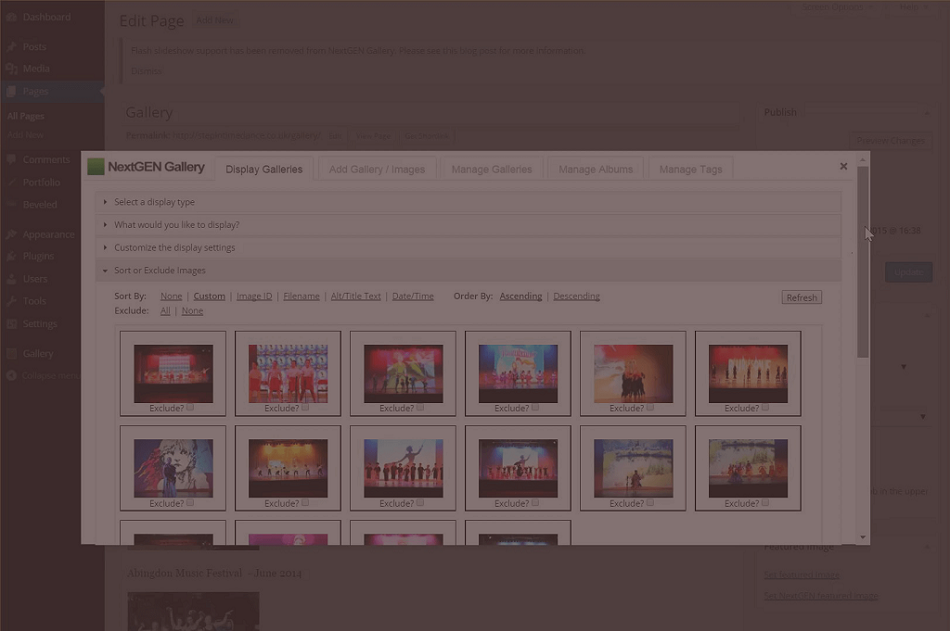
Remote Code Flaw Exploits WordPress Renown Plugin
A dangerous SQL injection vulnerability has been detected in NextGEN Gallery, WordPress’ renowned im…

Hackers Breached Singapore’s Ministry of Defense
The hackers of Singapore have invaded a military system of their own country which holds the non-cla…

Hackers Targeted ‘Teddy Bears’ For Massive Data Breach
With providing ease to please your children, the toys ‘Cloudpets’ have now become the backdoor for h…

Facebook Locked Its Users From Access
Today was a great fear for Facebook users when some of them suddenly locked out of their account. Bu…

This Is How You Get Hacked On Public Wi-Fi
Walking around the street seems to be exciting and less boring with a WiFi connection. But at the sa…

Rule 41 Empowers FBI To Extend Its Hacking Operations
The FBI and other security agencies can now search computers with a single search warrant because of…

The NSA “support of encryption” is ‘disingenuous’ says EFF
CAMBRIDGE, Ma. – Cambridge Cyber Summit by MIT – The NSA came out in support of encryption. But the …
Dailymotion hack exposes 85 million users online
Dailymotion video-sharing website has suffered a massive data breach, exposing 85 million accounts o…

Mozilla Firefox Zero-Day Exploit Exposes Tor Users
A zero-day exploit in the FireFox browser is in the wild that is used by hackers to de-anonymize peo…

Hackers Crashed San Francisco Municipal Railway Systems
San Francisco Municipal Railway computer systems hacked in a Ransomware attack and the authorities h…

Facebook Spam Campaign Spreads Ransomware Via SVG Image File
Hackers are now leveraging Facebook Messenger’s trust to spread locky-ransomware via SVG images in a…

UK Slams Its Citizens With An Extreme Surveillance Law
United Kingdom – House of Lords has passed Investigatory Powers Bill (IPB), which is being called as…

Government Of Italy Website Breached In A Kapustkiy Awareness Program
Since last week the 17 years old security pentester has been in headlines for his activities of ‘rai…

Mark Zuckerberg Hit ‘Being Hacked’ For The Third Time This Year
It’s now the third time of this year that Mark Zuckerberg has had his Pinterest account hacked once …

Adups Secret Backdoor In Some US Phones Sent Data To China
America is apprehensive about whether $50 smartphones from China surveillance over it through backdo…

Hackers Can Use iOS WebView To Make Phone Calls
The iOS apps for LinkedIn, Twitter, and possibly be many other vendors can be squandered by hackers …

Facebook ‘Memorial’ Glitch Kills Off Its Founder & Users As Dead
Funny as it sounds, the technology has its odd ways when it comes to glitches, as it happened with F…
How Trump Won? Don’t Open E-Mails, Malware Hits Again
How Donald Trump won US Presidential Election is still a mystery to some. People actually voted him …

Windows Patches Exploits Used By Russian Hackers, Update Your Windows Now
Microsoft released 14 new security bulletins on Tuesday, in which, it addressed many security issues…

EFF Slams DEA In A ‘Hemisphere Surveillance’ Lawsuit
The Drug Enforcement Agency is being sued by Electronic Frontier Foundation (EFF) as part of Freedom…

IT Security Negligence Of Indian Embassies Leads To Hack
Indian embassies in 7 countries experienced a severe data breach and more than 900 individuals sensi…
Mirai Malware Test-Run On Liberia’s Entire Internet Connectivity Finally Ceases
Intermittent DDoS attacks one of the largest Mirai malware powered botnets targeted Liberia, the Afr…

Unknown Malware Shuts Down National Health Service Operations
A malware attack on National Health Service (NHS) network caused hundreds of scheduled appointments,…

Google Discloses Microsoft’s ‘Unpatched Actively Exploited’ Bugs, Used by Russian Hackers?
Google disclosed Microsoft’s windows zero-day vulnerability. Microsoft doesn’t seem happy about it. …
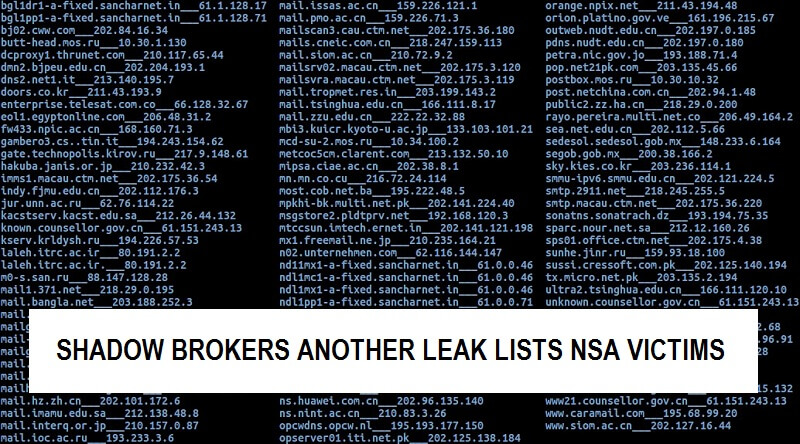
Shadow Brokers’ Another Leak Lists NSA Victims
The Group Shadow Brokers has leaked more files which include a servers list allegedly used by the Eq…

Throwback: NSA Hacking Tools – What You Need To Know
Announcing the auction of NSA agency made “cyber weapons” by a hacking group, “Shadow Brokers” confi…

Australian Red Cross Blood Service – Australia’s Largest Leak Of Private Data
Australian Red Cross Blood Service’s ‘blood donors’ data leak is being considered as the ‘most sever…

Customers Handle ‘Driver’s Seat’ Of Their Private Data, FCC New Rule Order ISPs
The U.S. Federal Communication Commission (FCC) has passed long-expected new orders that will give c…
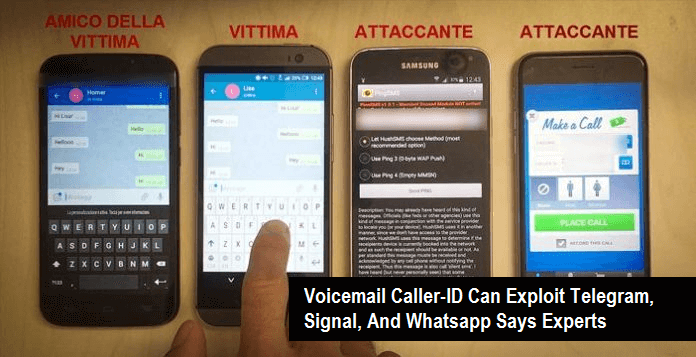
Voicemail Caller – ID Can Exploit Telegram, Signal, And WhatsApp
Italian cyber security experts have found a voicemail caller-ID vulnerability that can potentially b…
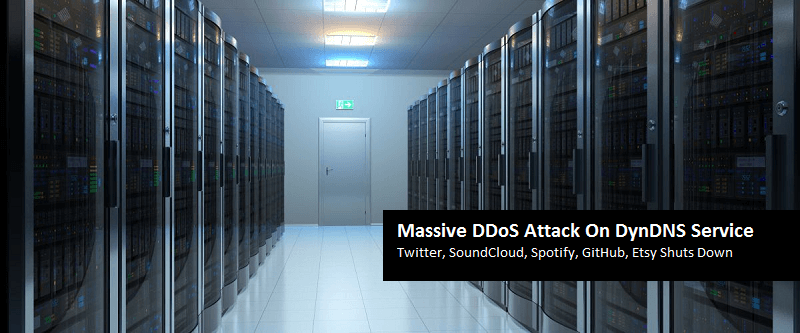
Another Massive DDoS Attack Shuts Down Popular Websites
GitHub, Twitter, and a long list of known websites are inaccessible for the majority of users worldw…
Skype Typing – A Serious Threat To Your Online Privacy
Multitasking while on call especially on Skype is good for productivity, but not much for privacy. …

Anti-Reconnaissance Tool By Microsoft Researchers
Microsoft has released a new tool ‘NetCease’ to help security teams in protecting corporate networks…

Nuclear Plants Hit By Cyber Attacks
“This issue of cyber attacks on nuclear-related facilities or activities should be taken very seriou…
BlockChain’s DNS Servers Breached By Cybercriminals
The developer of globally accepted popular BitCoin wallet, BlockChain, suffered a blackout this week…

Attackers Uses IE & Edge Zero-Day To Avoid Security Researchers
On Tuesday, Microsoft patched the vulnerabilities affecting its products. One of the internet explor…

Insulin Pumps Could Be Hacked, Johnson & Johnson Warns
OneTouch insulin pump by the company “Animas” contains vulnerabilities that a malicious attacker can…

Apple vs. FBI – The Summary Of Events
The legal battle between the U.S. Federal Bureau of Investigation (FBI) and Apple over accessi…

Tim Cook defended Apple’s Security – ‘Encryption is inherently great’
Apple CEO Tim Cook stood firm on his stance on encryption while attending Utah Tech Tour, a trade an…

DressCode Malware Hits 400 Apps in Google Play
A recent discovery in mobile malware family been calling as “DressCode” has infected over 400 apps t…

Diagnosing and Solving Disk Ejection Errors in Mac
Is your Mac ejecting disks for seemingly no reason? A lot of Mac users have experienced this problem…

CYBER DEFENSE | Various Cyber Defense Products
Cyber attacks have become a key weapon in the arsenal of nation-backed aggressors, terrorist organiz…

